Fortinet NSE4_FGT-7.2 - Fortinet NSE 4 - FortiOS 7.2
82
Consider the topology:
Application on a Windows machine <--{SSL VPN} -->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
An organization requires remote users to send external application data running on their PCs and access FTP resources through an SSL/TLS connection.
Which FortiGate configuration can achieve this goal?
6
Which three options are the remote log storage options you can configure on FortiGate? (Choose three.)
Refer to the FortiGuard connection debug output.
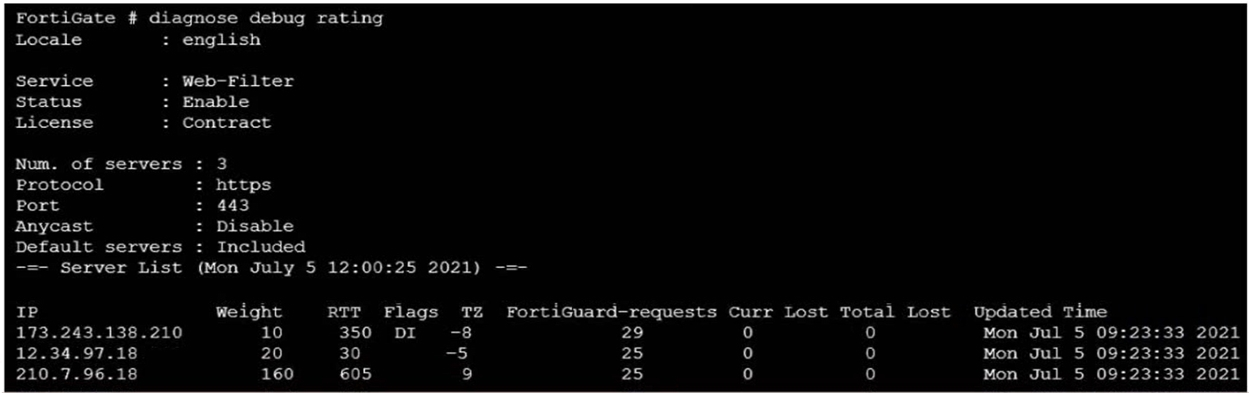
Based on the output shown in the exhibit, which two statements are correct? (Choose two.)
Refer to the exhibit.
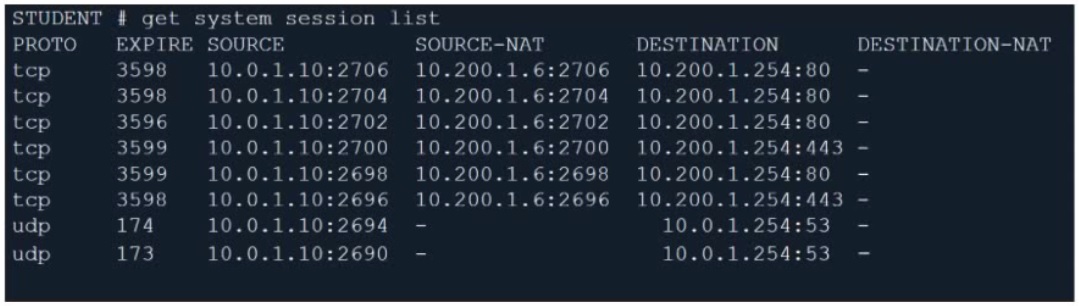
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
51
Which of the following statements about central NAT are true? (Choose two.)
31
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
94
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The administrator disabled the WebServer firewall policy.
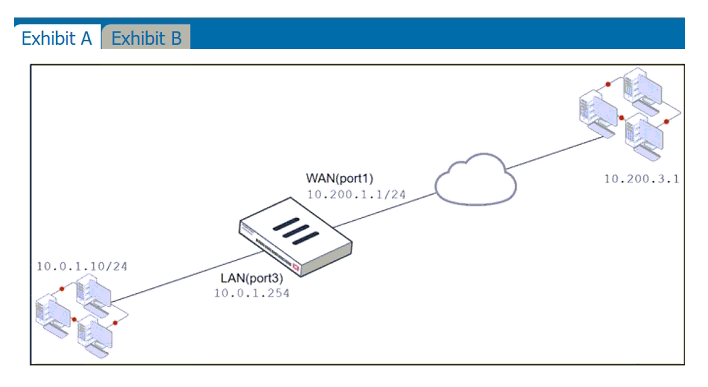
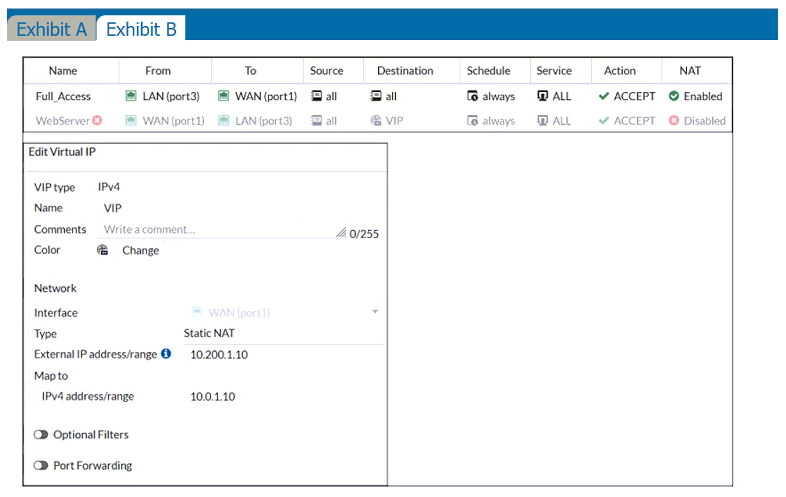
Which IP address will be used to source NAT the traffic, if a user with address 10.0.1.10 connects over SSH to the host with address 10.200.3.1?
Refer to the exhibit.
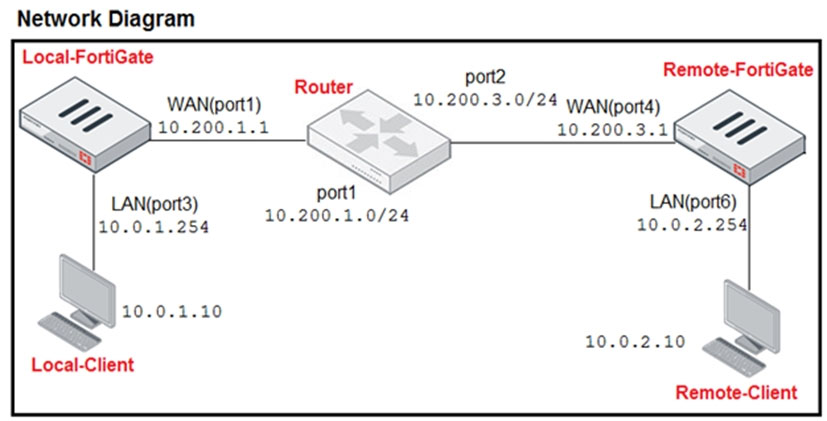
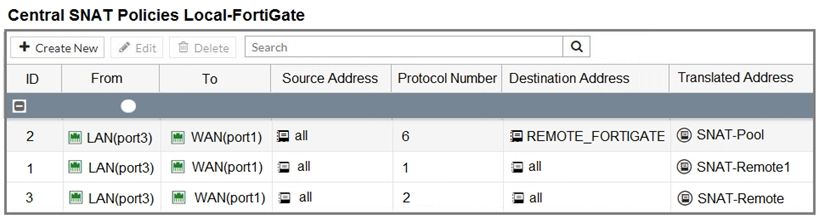
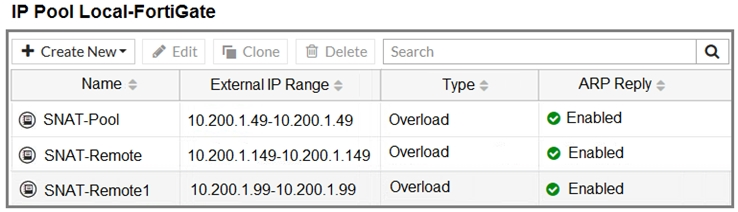
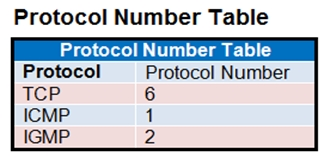
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10.0. 1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0. 1. 10) pings the IP address of Remote-FortiGate (10.200.3. 1)?



