Fortinet NSE4_FGT-7.2 - Fortinet NSE 4 - FortiOS 7.2
Which statement is correct regarding the use of application control for inspecting web applications?
24
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on
which device?
16
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy. Which two other security profiles can you apply to the security policy? (Choose two.)
40
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
95
Examine this output from a debug flow:
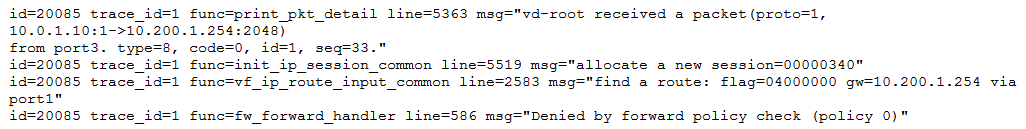
Why did the FortiGate drop the packet?
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
18
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
Which statement correctly describes the use of reliable logging on FortiGate?
What are two characteristics of FortiGate HA cluster virtual IP addresses? (Choose two.)



