Fortinet NSE5_FSM-6.3 - Fortinet NSE 5 - FortiSIEM 6.3
If a performance rule is triggered repeatedly due to high CPU use, what occurs in the incident table?
Refer to the exhibit.
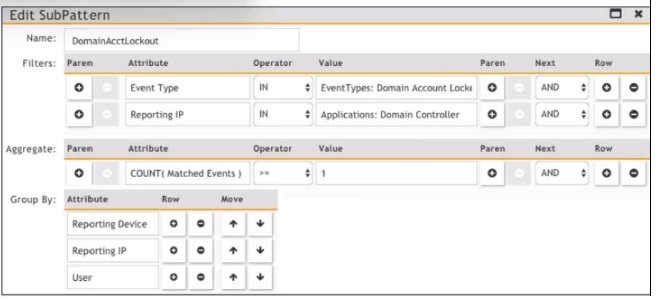
Which section contains the sortings that determine how many incidents are created?
Refer to the exhibit.

The output shows that the license is in which condition?
Which is a requirement for implementing FortiSIEM disaster recovery?
Which database is used for storing anomaly data, that is calculated for different parameters, such as traffic and device resource usage running averages, and standard deviation values?
Refer to the exhibit.
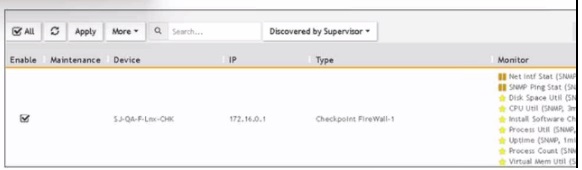
What does the pauso icon indicate?
How is a subpattern for a rule defined?
An administrator is using SNMP and WMI credentials to discover a Windows device. How will the WMI method handle this?
Consider the storage of anomaly baseline date that is calculated for different parameters. Which database is used for storing this data?
In which state can a device be moved into the CMDB to prevent monitoring log collection?



