Fortinet NSE6_FAC-6.4 - Fortinet NSE 6 - FortiAuthenticator 6.4
Which interface services must be enabled for the SCEP client to connect to Authenticator?
Which behaviors exist for certificate revocation lists (CRLs) on FortiAuthenticator? (Choose two)
Examine the screenshot shown in the exhibit.
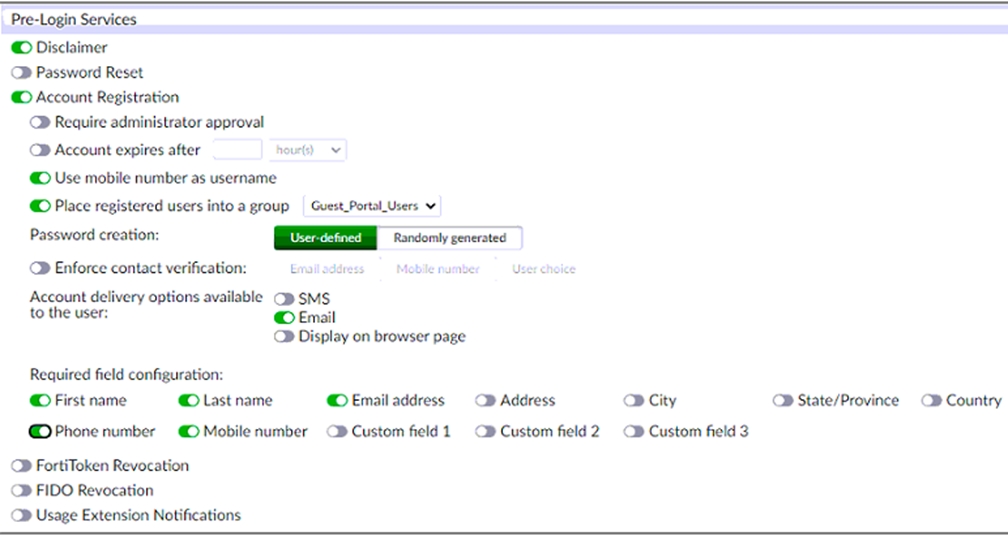
Which two statements regarding the configuration are true? (Choose two.)
You are the administrator of a global enterprise with three FortiAuthenticator devices. You would like to deploy them to provide active-passive HA at headquarters, with geographically distributed load balancing.
What would the role settings be?
An administrator wants to keep local CA cryptographic keys stored in a central location.
Which FortiAuthenticator feature would provide this functionality?
A digital certificate, also known as an X.509 certificate, contains which two pieces of information? (Choose two.)
Which method is the most secure way of delivering FortiToken data once the token has been seeded?
Which option correctly describes an SP-initiated SSO SAML packet flow for a host without a SAML assertion?
Which FSSO discovery method transparently detects logged off users without having to rely on external features such as WMI polling?
Which two statements about the EAP-TTLS authentication method are true? (Choose two)



