Fortinet NSE6_FML-6.4 - Fortinet NSE 6 - FortiMail 6.4
Which three statements about SMTPS and SMTP over TLS are true? (Choose three.)
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
Which two CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
Refer to the exhibit.
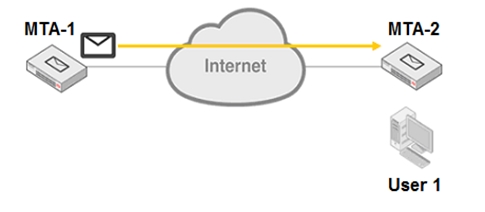
MTA-1 is delivering an email intended for User 1 to MTA-2.
Which two statements about protocol usage between the devices are true? (Choose two.)
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
Refer to the exhibit.
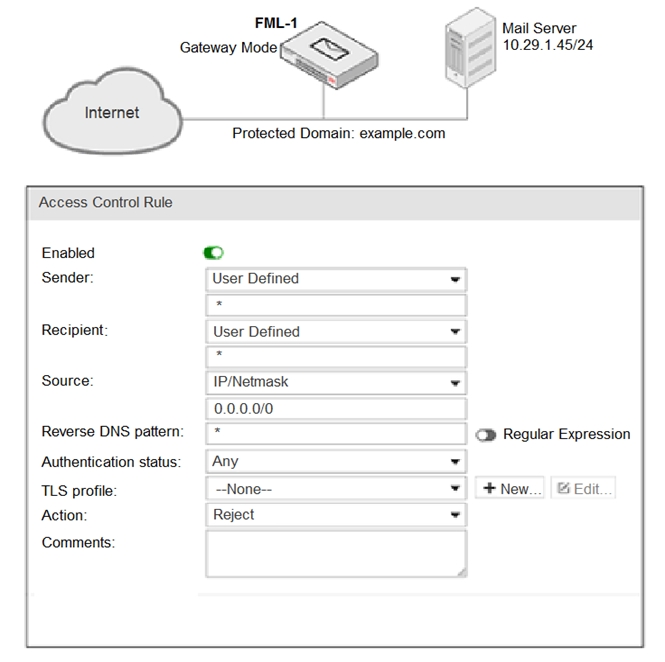
It is recommended that you configure which three access receive settings to allow outbound email from the
example.com domain on FML-1? (Choose three.)
Refer to the exhibit.
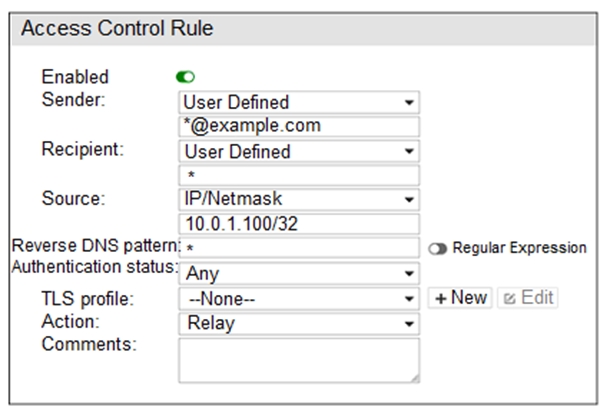
Which two statements about the access receive rule are true? (Choose two.)
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9.
Which two scenarios will generate this policy ID? (Choose two.)
Examine the FortiMail topology and access receive rule shown in the exhibit; then answer the question below.
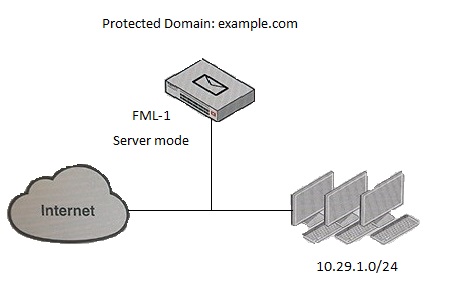
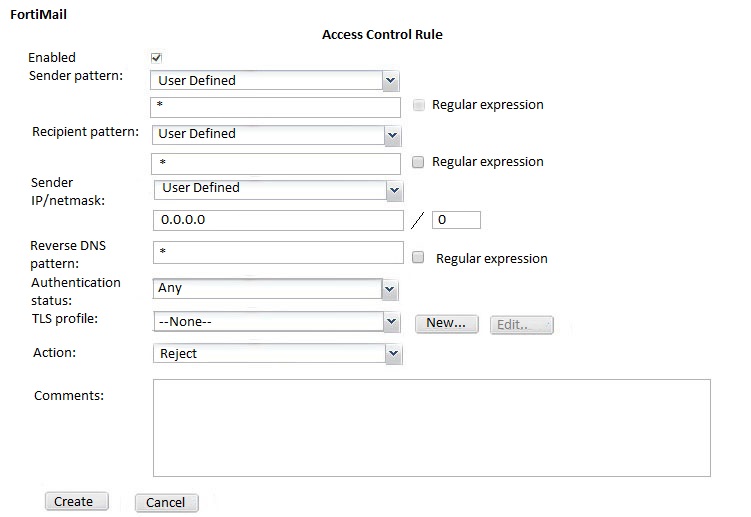
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain. Which of the following settings should be used to configure the access receive rule? (Choose two.)
Examine the message column of a log cross search result of an inbound email shown in the exhibit; then answer the question below
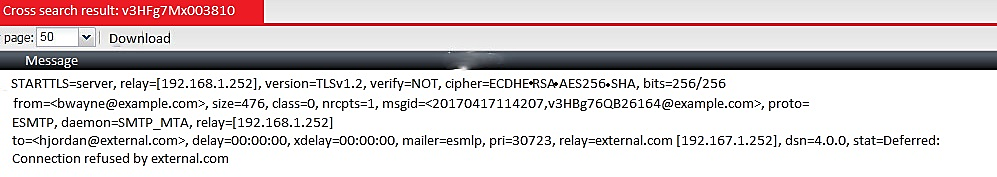
Based on logs, which of the following statements are true? (Choose two.)



