Fortinet NSE6_FNC-7.2 - Fortinet NSE 6 - FortiNAC 7.2
When FortiNAC is managing FortiGate VPN users, why is an endpoint compliance policy necessary?
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
Refer to the exhibit.
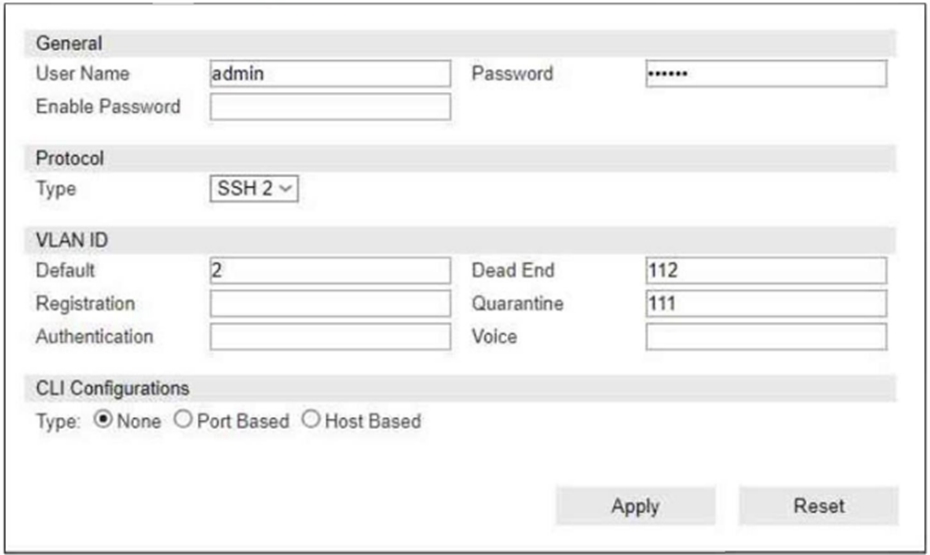
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
While troubleshooting a network connectivity issue, an administrator determines that a device was being automatically provisioned to an incorrect VLAN.
Where would the administrator look to determine when and why FortiNAC made the network access change?
Where are logical network values defined?
Which connecting endpoints are evaluated against all enabled device profiling rules?



