Fortinet NSE7_NST-7.2 - Fortinet NSE 7 - Network Security 7.2 Support Engineer
Refer to the exhibit, which shows the output of a BGP debug command.
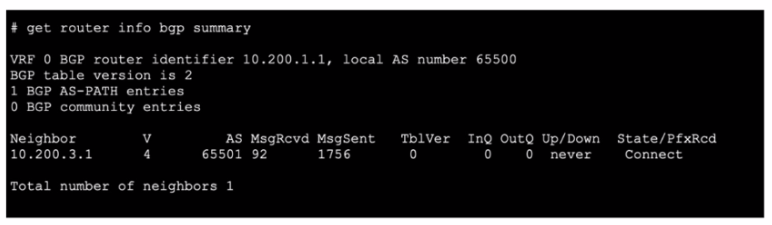
Which statement explains why the state of the 10.200.3.1 peer is Connect?
Refer to the exhibit, which shows a truncated output of a real-time LDAP debug.
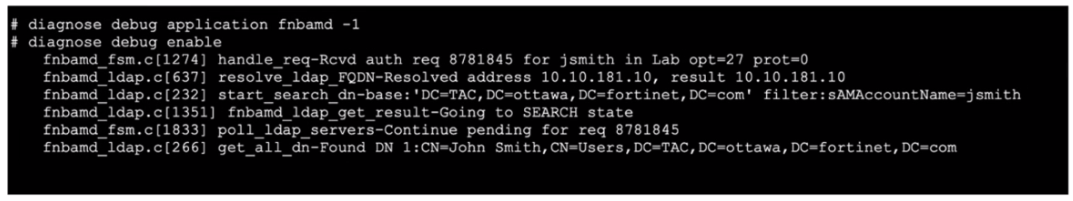
What two conclusions can you draw from the output? (Choose two.)
There are four exchanges during IKEv2 negotiation.
Which sequence is correct?
Refer to the exhibit, which shows the output of diagnose syssessionstat. Which statement about the output shown in the exhibit is correct?
Which two statements about conserve mode are true? (Choose two.)
What are two functions of automation stitches? (Choose two.)
Refer to the exhibits.
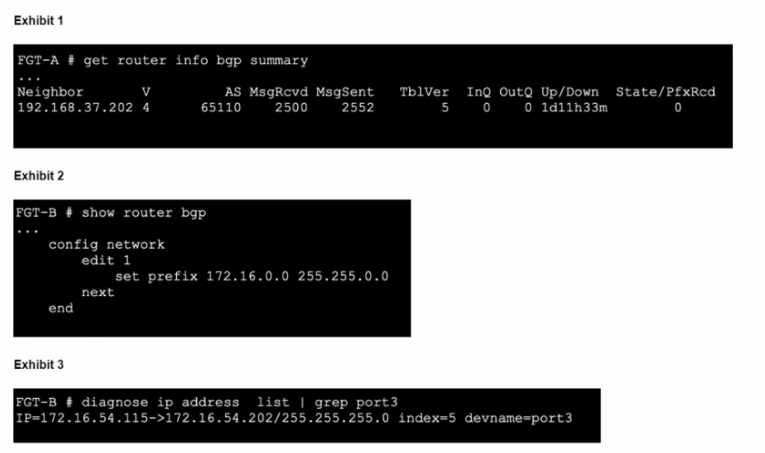
An administrator is attempting to advertise the network configured on port3. However, FGT-A is not receiving the prefix.
Which two actions can the administrator take to fix this problem'' (Choose two.)
Referto the exhibit, which shows oneway communication of the downstream FortiGate with the upstream FortiGate within a Security Fabric.
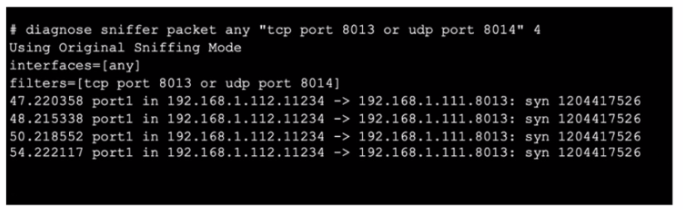
What three actions must you take to ensure successful communication? (Choose three.)
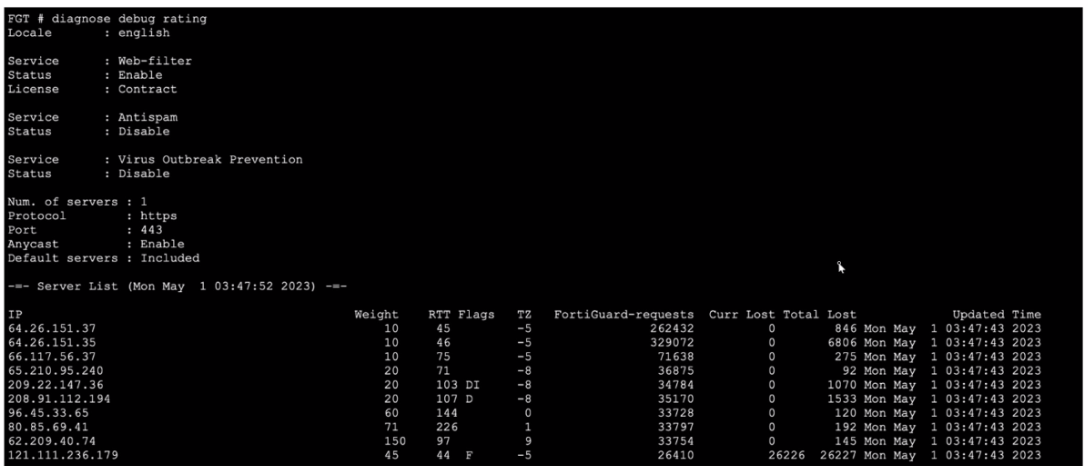
Refer to the exhibit, which shows the output of a diagnose command.
What can you conclude from the RTT value?
Refer to the exhibit, which shows a truncated output of a real-time RADIUS debug.
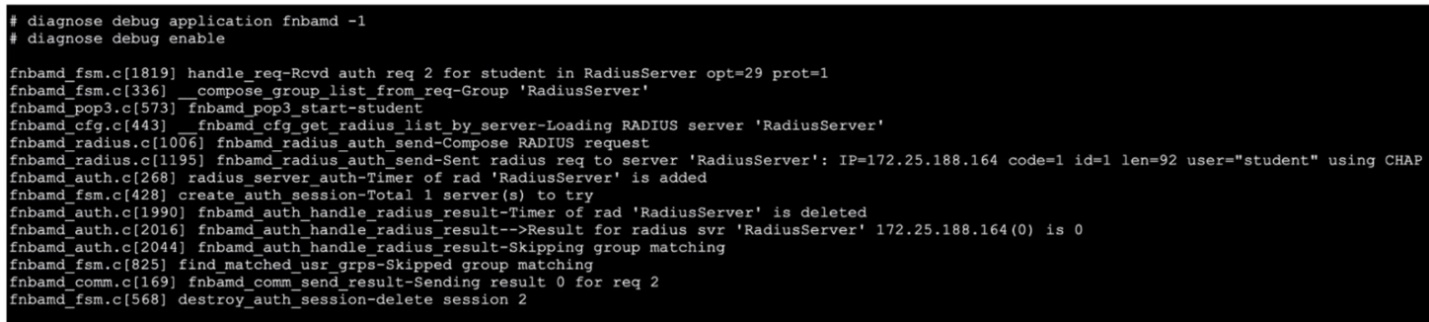
Which two statements are true? (Choose two.)



