Fortinet NSE7_SDW-7.2 - Fortinet NSE 7 - SD-WAN 7.2
Which two statements reflect the benefits of implementing the ADVPN solution to replace conventional VPN topologies? (Choose two.)
Which two statements about SD-WAN central management are true? (Choose two.)
Refer to the exhibit.
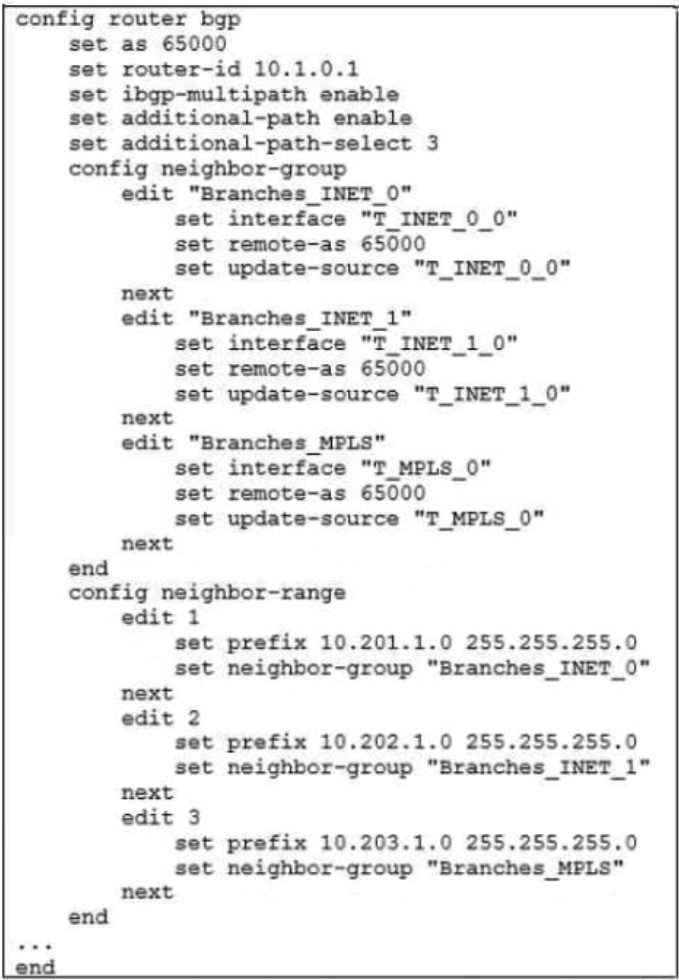
The exhibit shows the BGP configuration on the hub in a hub-and-spoke topology. The administrator wants BGP to advertise prefixes from spokes to other spokes over the IPsec overlays, including additional paths. However, when looking at the spoke routing table, the administrator does not see the prefixes from other spokes and the additional paths.
Based on the exhibit, which three settings must the administrator configure inside each BGP neighbor group so spokes can learn other spokes prefixes and their additional paths? (Choose three.)
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
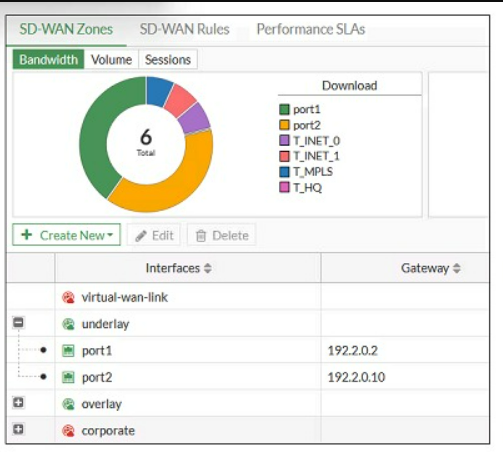
Based on the exhibit, which statement is true?
Refer to the exhibit.
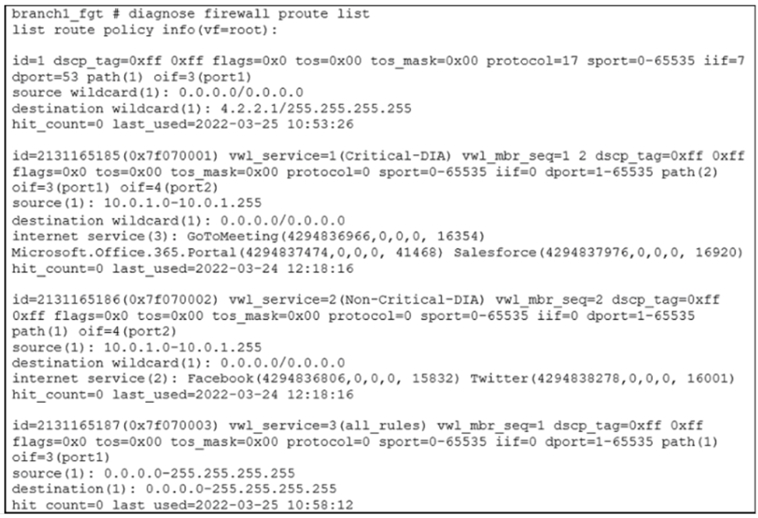
Based on the output, which two conclusions are true? (Choose two.)
Which two statements describe how IPsec phase 1 main mode id different from aggressive mode when performing IKE negotiation? (Choose two.)
Which two performance SLA protocols enable you to verify that the server response contains a specific value? (Choose two.)
Which two protocols in the IPsec suite are most used for authentication and encryption? (Choose two.)
What are two benefits of using the Internet service database (ISDB) in an SD-WAN rule? (Choose two.)
What is a benefit of using application steering in SD-WAN?



