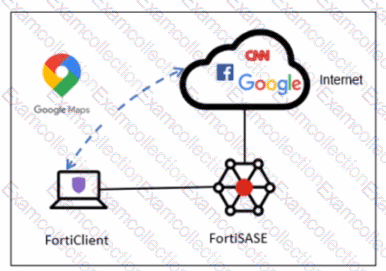
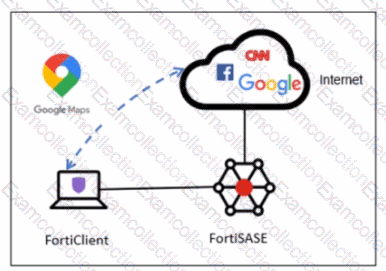
In a default FortiSASE deployment, endpoints are typically onboarded using a shared invitation code sent via email. While this code simplifies deployment, it can represent a security risk if the code is leaked or intercepted, as any device with the code could potentially register with the SASE management service.
User Verification (SAML SSO): To mitigate this risk, administrators can enable user verification as an additional layer of security.3 When this feature is enforced, entering the invitation code is no longer sufficient to complete registration.
Authentication Workflow: After the end user enters the invitation code in FortiClient, they are prompted to provide their corporate credentials via a SAML SSO login.5 FortiSASE acts as the Service Provider (SP), while an external identity provider (IdP) such as Microsoft Entra ID, Okta, or FortiAuthenticator verifies the user's identity.
Security Benefit: This ensures that only authenticated users—not just anyone with a valid code—can successfully register an endpoint and receive the organization's security and VPN profiles. It prevents unauthorized "shadow" endpoints from joining the managed environment.
Incorrect Options:
Option A: Security posture tags are used after registration to determine if an endpoint is compliant (e.g., checking if an antivirus is active); they do not secure the registration process itself.
Option C and D: Device identification and application inventory are monitoring and visibility features that occur once the endpoint is already managed.
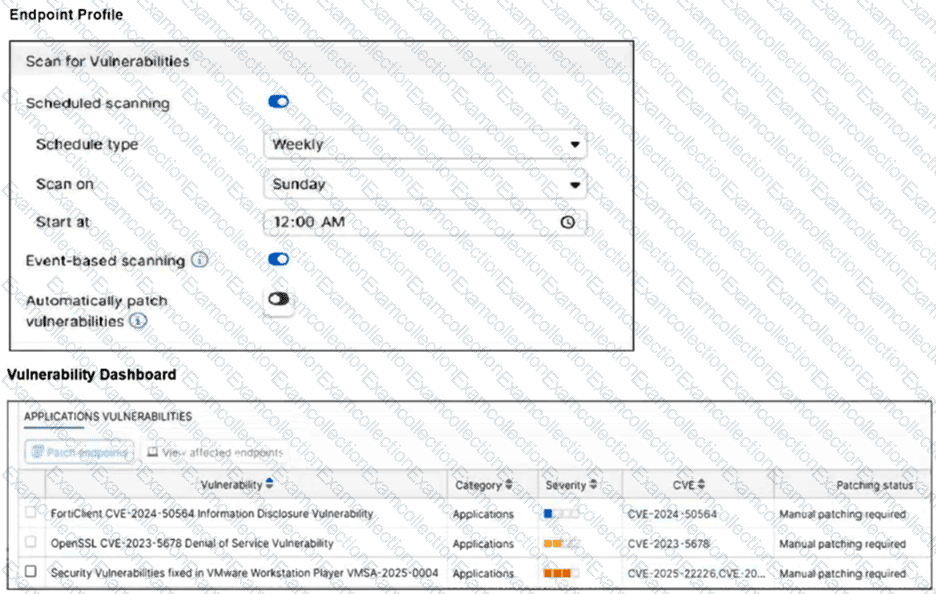
Refer to the exhibit. Based on the configuration shown in image_595357.jpg, FortiSASE will process sessions requiring FortiSandbox inspection in the following two ways:
A. Only endpoints assigned a profile for sandbox detection will be processed by the sandbox feature.
C. All files executed on a USB drive will be sent to FortiSandbox for analysis.
Answer: A, C
The provided exhibit displays an Endpoint Profile configuration specifically for the Sandbox module. This profile controls how the FortiClient agent on remote endpoints interacts with the integrated FortiSASE cloud sandbox engine.
Profile Assignment (A): In the FortiSASE architecture, security and endpoint settings are organized into profiles that must be explicitly assigned to users or user groups via endpoint policies. Consequently, the sandbox detection and remediation features are active only on those endpoints that have been assigned this specific endpoint profile. If an endpoint is not assigned a profile with sandbox enabled, it will not submit files for analysis.
Removable Media Analysis (C): Under the File Submission Options, the toggle for All Files Executed from Removable Media is enabled (shown in blue). Since USB drives are the most common form of removable media, this configuration ensures that any file executed from a USB drive is intercepted by FortiClient and submitted to the FortiSASE sandbox for behavioral analysis before being allowed to run, protecting the endpoint from offline-delivered threats.
Understanding Verdict Levels (B): The exhibit shows the Action is set to Quarantine and the Sandbox Detection Verdict Level is set to Medium. This configuration functions as a threshold; FortiClient will quarantine any file that receives a verdict of Medium or higher (including High and Malicious). Option B is incorrect because it claims only medium-level files are quarantined, which ignores the high-risk and malicious files that would also be blocked.
Sandbox Mode (D): The Sandbox Mode is clearly set to FortiSASE, which utilizes the built-in cloud-native sandbox. This contradicts Option D, which suggests the use of an on-premises or standalone sandbox appliance.