Fortinet NSE8_812 - Network Security Expert 8 Written Exam
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
You are running a diagnose command continuously as traffic flows through a platform with NP6 and you obtain the following output:
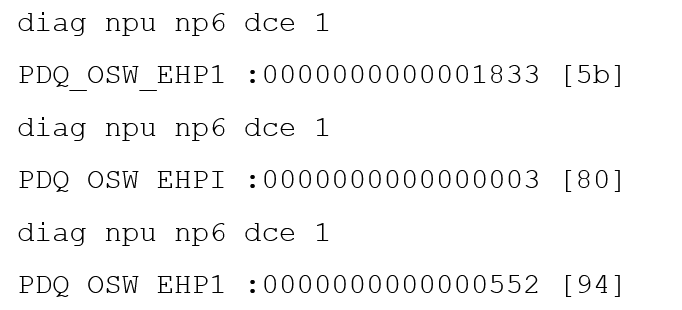
Given the information shown in the output, which two statements are true? (Choose two.)
Refer to the exhibit showing an SD-WAN configuration.
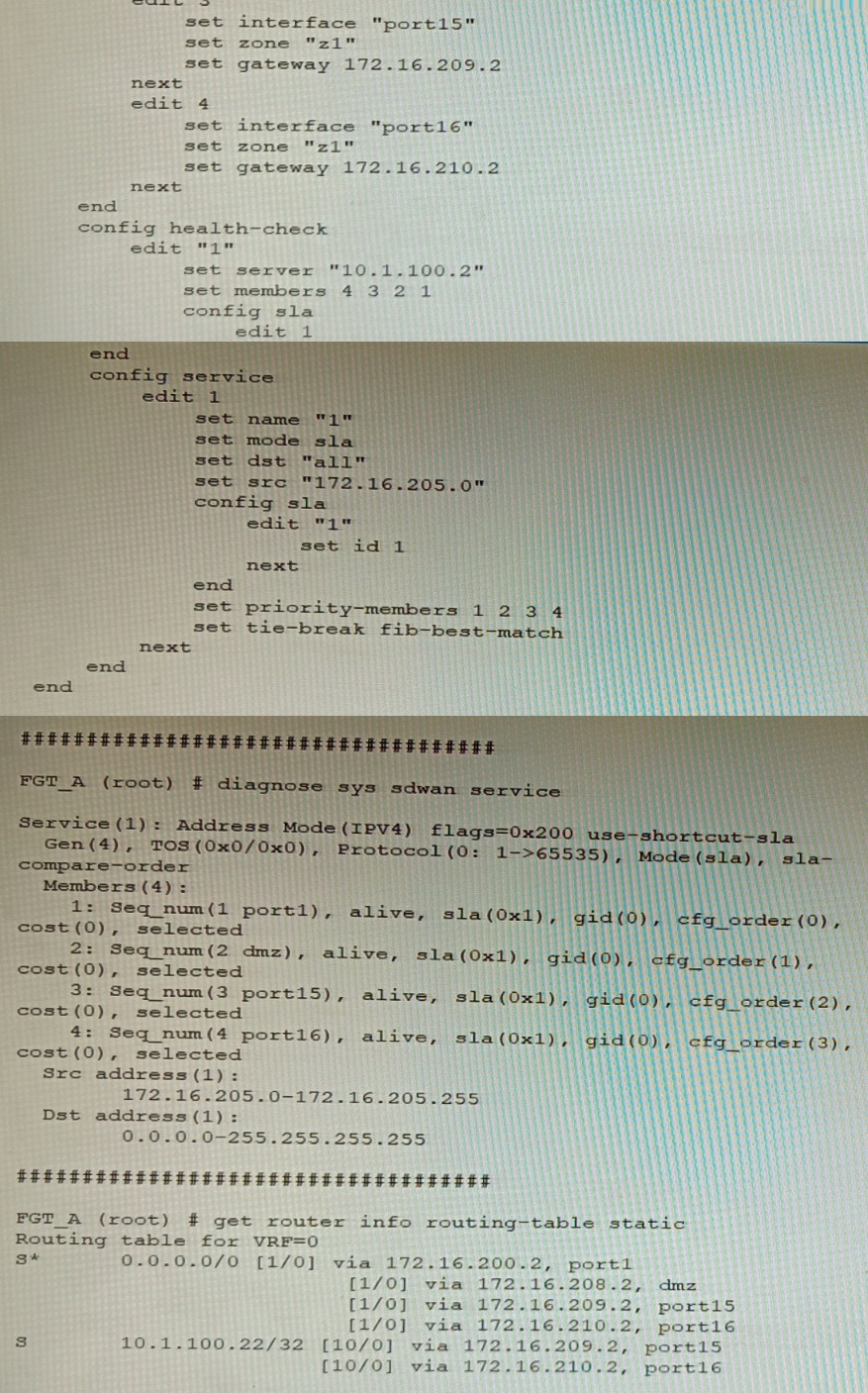
According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
An administrator discovers that CPU utilization of a FortiGate-200F is high and determines that no traffic is being accelerated by hardware.
Why is no traffic being accelerated by hardware?
Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
A customer's cybersecurity department needs to implement security for the traffic between two VPCs in AWS, but these belong to different departments within the company. The company uses a single region for all their VPCs.
Which two actions will achieve this requirement while keeping separate management of each department's VPC? (Choose two.)
Refer to the exhibits, which show a topology and diagnostic commands.
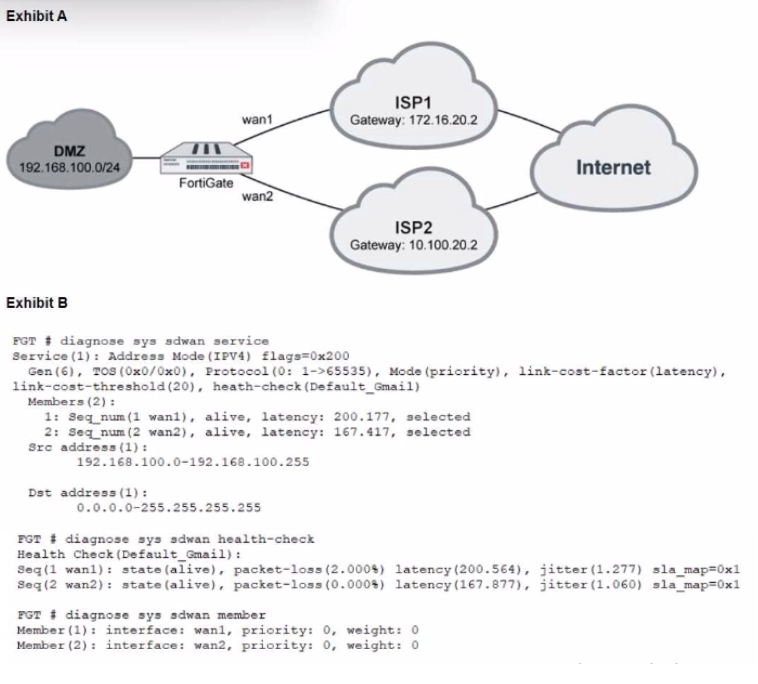
Which two statements about the path resolution are true? (Choose two.)
Refer to the exhibits.
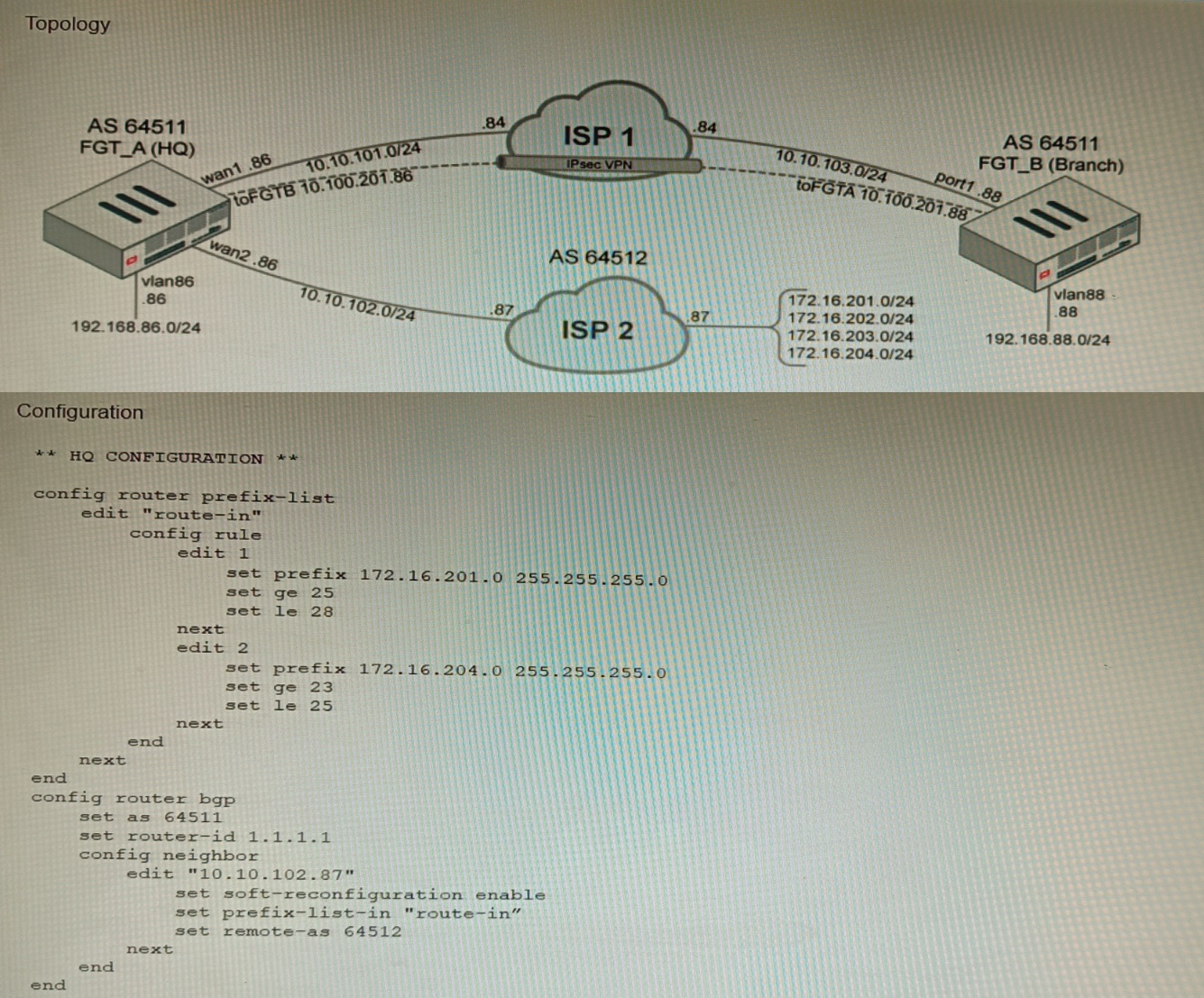
A customer has deployed a FortiGate with iBGP and eBGP routing enabled. HQ is receiving routes over eBGP from ISP 2; however, only certain routes are showing up in the routing table-Assume that BGP is working perfectly and that the only possible modifications to the routing table are solely due to the prefix list that is applied on HQ.
Given the exhibits, which two routes will be active in the routing table on the HQ firewall? (Choose two.)
You deployed a fully loaded FG-7121F in the data center and enabled sslvpn-load-balance. Based on the behavior of this feature which statement is correct?
Refer to the exhibit.
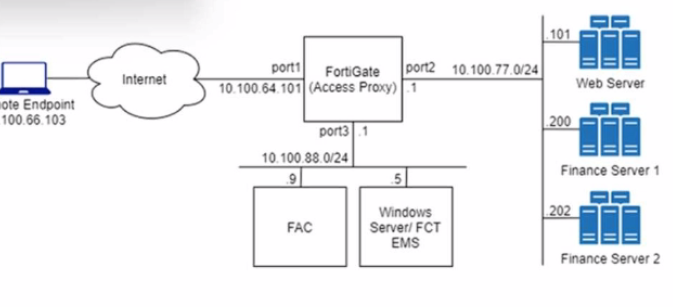
An HTTPS access proxy is configured to demonstrate its function as a reverse proxy on behalf of the web server it is protecting. It verifies user identity, device identity, and trust context, before granting access to the protected source. It is assumed that the FortiGate EMS fabric connector has already been successfully connected.
You need to ensure that ZTNA access through the FortiGate will redirect users to the FortiAuthenticator to perform username/password and multifactor authentication to validate access prior to accessing resources behind the FortiGate.
In this scenario, which two further steps need to be taken on the FortiGate? (Choose two.)



