Netskope NSK200 - Netskope Certified Cloud Security Integrator (NCCSI)
You are troubleshooting an issue with Microsoft where some users complain about an issue accessing OneDrive and SharePoint Online. The configuration has the Netskope client deployed and active for most users, but some Linux machines are routed to Netskope using GRE tunnels. You need to disable inspection for all users to begin troubleshooting the issue.
In this scenario, how would you accomplish this task?
You are an administrator writing Netskope Real-time Protection policies and must determine proper policy ordering.
Which two statements are true in this scenario? (Choose two.)
Your customer is concerned about malware in their AWS S3 buckets. What two actions would help with this scenario? (Choose two.)
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as CrowdStrike. In this scenario, what is a requirement for a successful Integration and sharing of threat data?
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?
You are currently migrating users away from a legacy proxy to the Netskope client in the company’s corporate offices. You have deployed the client to a pilot group; however, when the client attempts to connect to Netskope, it fails to establish a tunnel.
In this scenario, what would cause this problem?
Your organization has three main locations with 30.000 hosts in each location. You are planning to deploy Netskope using iPsec tunnels for security.
What are two considerations to make a successful connection in this scenario? (Choose two.)
Review the exhibit.
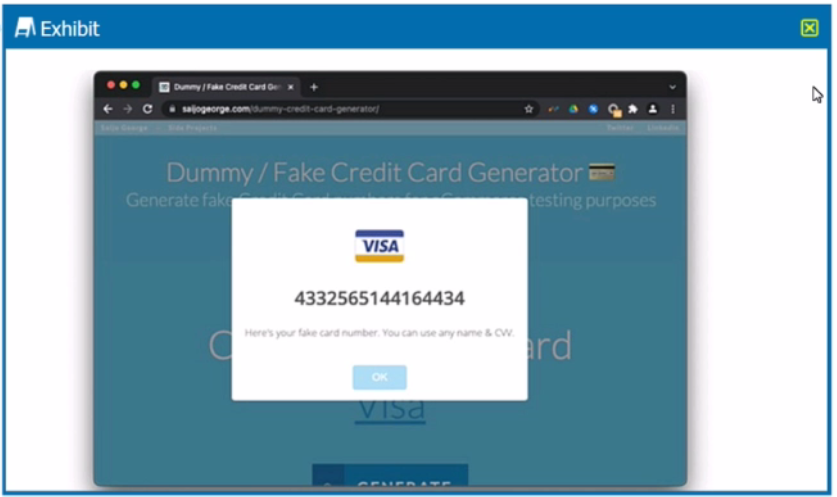
You are asked to create a DLP profile that will ensure that the data shown in the exhibit cannot be uploaded to a user's personal Google Drive.
What must be used to accomplish this task?
Review the exhibit.
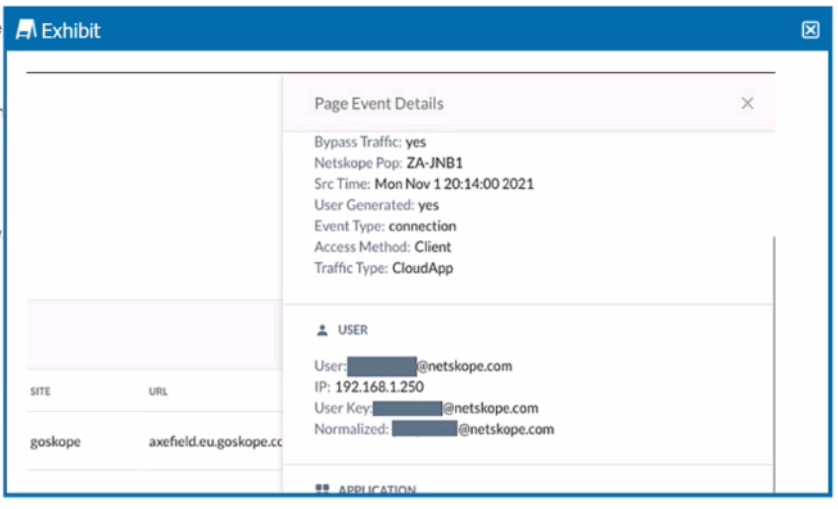
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
You have deployed a development Web server on a public hosting service using self-signed SSL certificates. After some troubleshooting, you determined that when the Netskope client is enabled, you are unable to access the Web server over SSL. The default Netskope tenant steering configuration is in place.
In this scenario, which two settings are causing this behavior? (Choose two.)



