Netskope NSK200 - Netskope Certified Cloud Security Integrator (NCCSI)
While most Web and SaaS traffic is decrypted for inspection, you are asked to prevent a certain host on the network from SSL decryption for privacy purposes.
You are troubleshooting private application access from a user's computer. The user is complaining that they cannot access the corporate file share; however, the private tunnel seems to be established. You open the npadebuglog.log file in a text editor and cannot find any reference to the private application.
Your customer is migrating all of their applications over to Microsoft 365 and Azure. They have good practices and policies in place (or their inline traffic, but they want to continuously detect reconfigurations and enforce compliance standards.
Which two solutions would satisfy their requirements? (Choose two.)
A customer wants to use Netskope to prevent PCI data from leaving the corporate sanctioned OneDrive instance. In this scenario. which two solutions would assist in preventing data exfiltration? (Choose two.)
Your company has a Symantec BlueCoat proxy on-premises and you want to deploy Netskope using proxy chaining. Which two prerequisites need to be enabled first in this scenario? (Choose two.)
Review the exhibit.
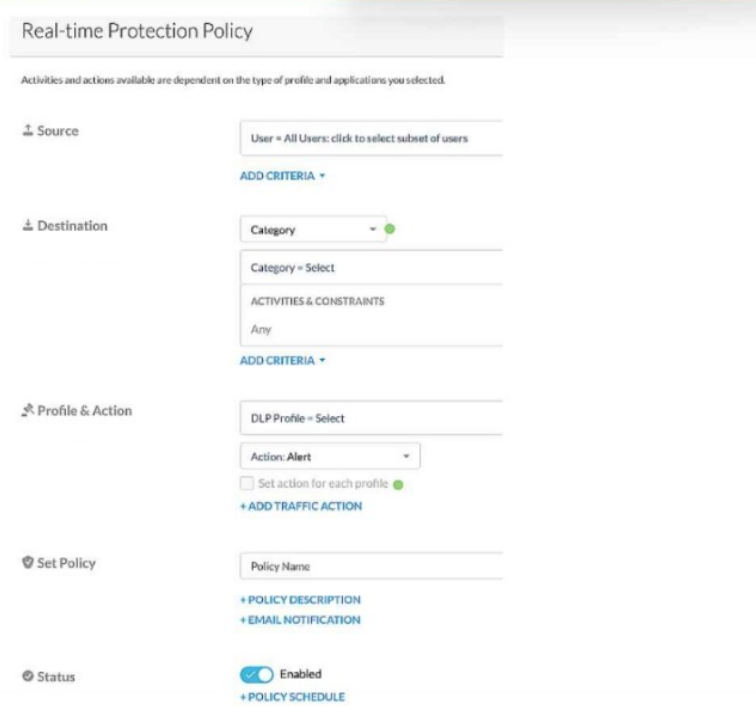
Given the information shown below:
-for PCI data uploads, you want to provide no notification,
-for PHI data uploads, you want to allow users to proceed by clicking OK,
-for GDPR data uploads, you want to provide block notification,
-if none of the above matches, you want to provide no notification.
You want to reduce the number of policies by combining multiple DLP profiles Into one policy.
Referring to the exhibit, which two statements are true? (Choose two.)
What is the purpose of the file hash list in Netskope?



