CyberArk PAM-DEF - CyberArk Defender - PAM
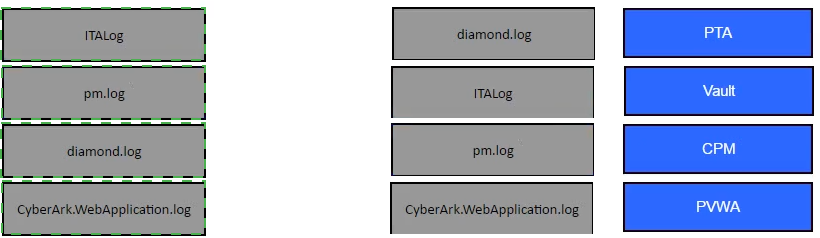
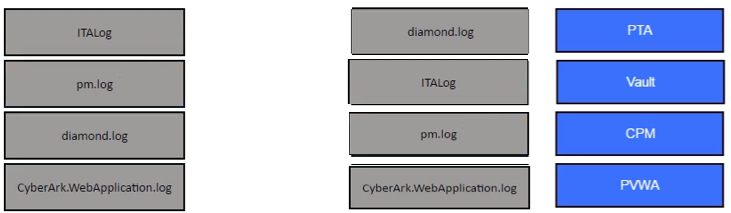
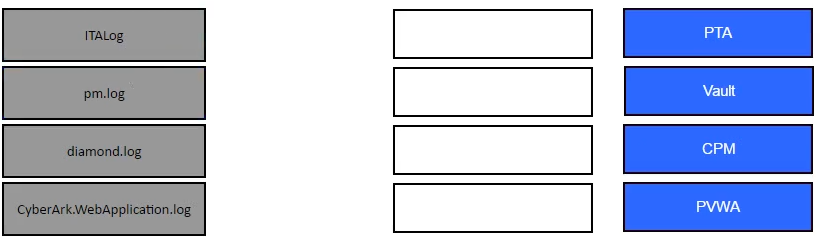
Match the log file name with the CyberArk Component that generates the log.
When managing SSH keys, the CPM stores the Public Key
If PTA is integrated with a supported SIEM solution, which detection becomes available?
Which item is an option for PSM recording customization?
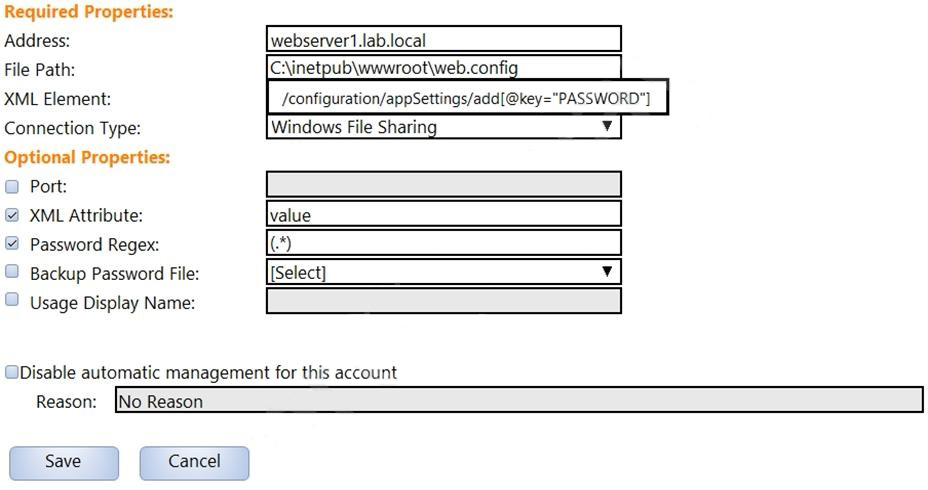
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to be changed.
Which methods can you use to add a user directly to the Vault Admin Group? (Choose three.)
By default, members of which built-in groups will be able to view and configure Automatic Remediation and Session Analysis and Response in the PVWA?
You are creating a Dual Control workflow for a team’s safe.
Which safe permissions must you grant to the Approvers group?