CyberArk PAM-SEN - CyberArk Sentry PAM
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? Choose all that apply
Which component must be installed before the first CPM installation?
You are installing the HTML5 gateway on a Linux host using the RPM provided.
After installing the Tomcat webapp, what is the next step in the installation process?
Which tools are used during a CPM renaming process? (Choose two.)
In a SIEM integration it is possible to use the fully-qualified domain name (FQDN) when specifying the SIEM server address(es)
How should you configure PSM for SSH to support load balancing?
In large-scale environments, it is important to enable the CPM to focus its search operations on specific Safes instead of scanning all Safes it sees in the Vault.
How is this accomplished?
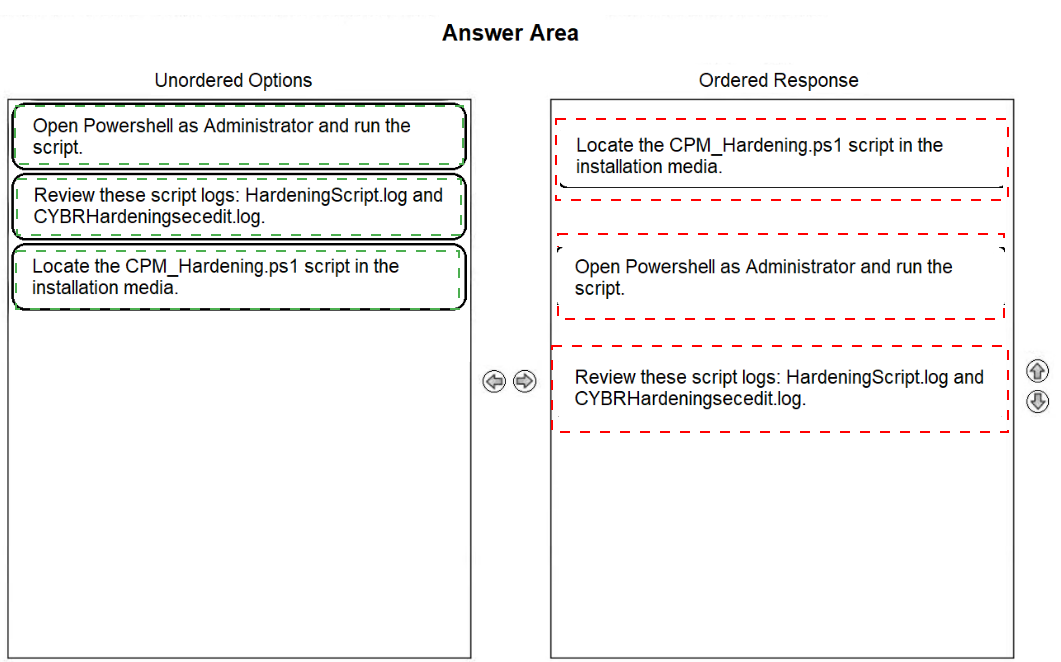
Arrange the steps to complete CPM Hardening for Out-of-Domain Deployment in the correct sequence.
You need to add a new PSM server to an existing CyberArk environment.
What is the best way to determine the sizing of this server?
Which configuration file and Vault utility are used to migrate the server key to an HSM?