Paloalto Networks PCCET - Palo Alto Networks Certified Cybersecurity Entry-level Technician
Which method is used to exploit vulnerabilities, services, and applications?
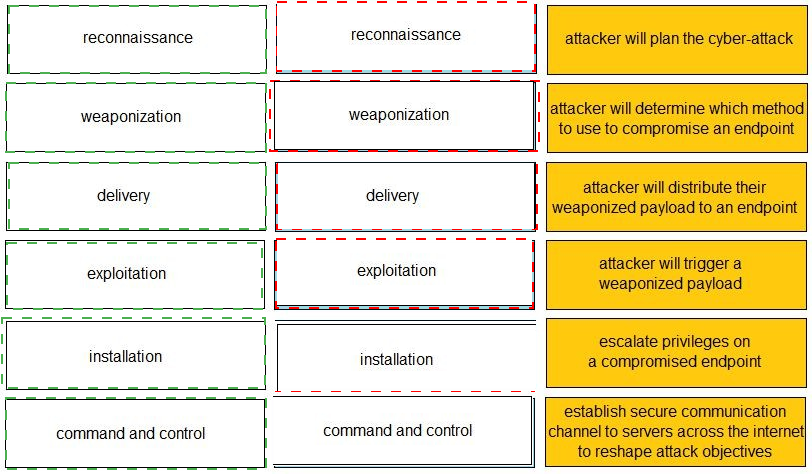
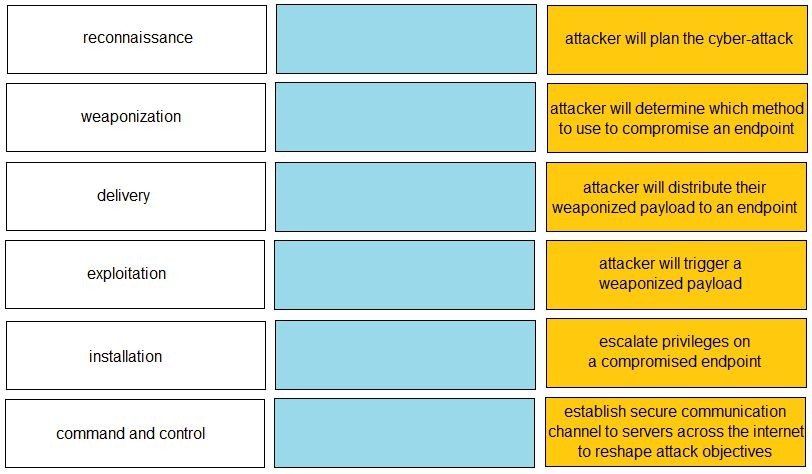
Given the graphic, match each stage of the cyber-attack lifecycle to its description.
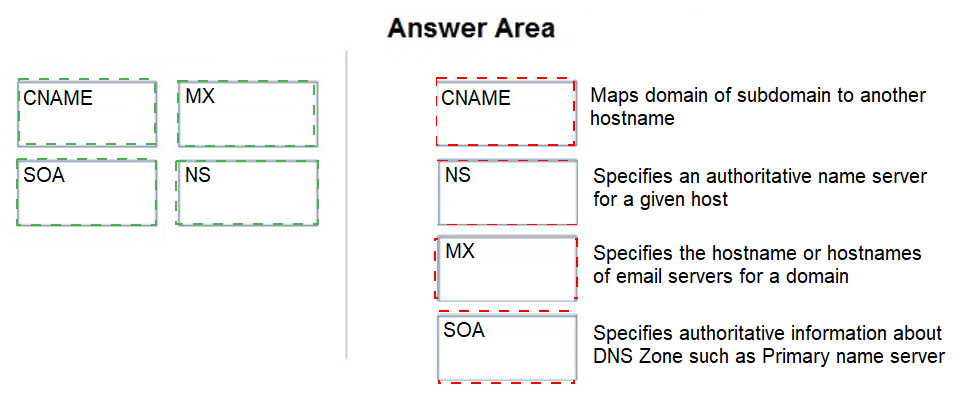
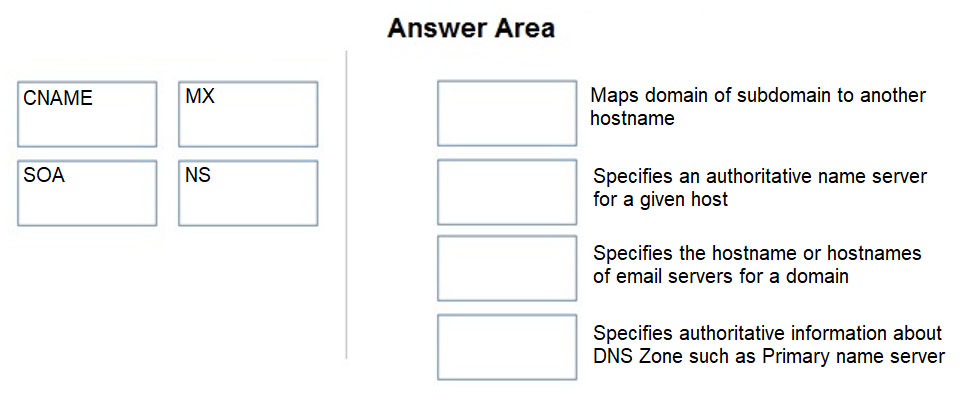
Match the DNS record type to its function within DNS.
What type of area network connects end-user devices?
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
Order the OSI model with Layer7 at the top and Layer1 at the bottom.
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
Which type of malware takes advantage of a vulnerability on an endpoint or server?
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
If an endpoint does not know how to reach its destination, what path will it take to get there?