Paloalto Networks PCCET - Palo Alto Networks Certified Cybersecurity Entry-level Technician
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
Why have software developers widely embraced the use of containers?
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
What is a key benefit of Cortex XDR?
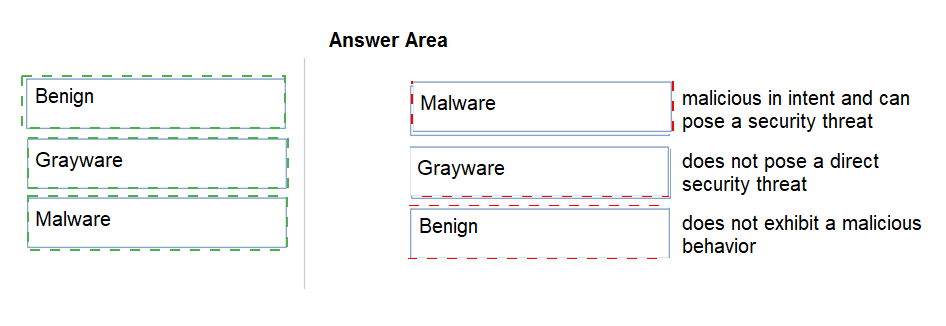
Match the Palo Alto Networks WildFire analysis verdict with its definition.

What are the two most prominent characteristics of the malware type rootkit? (Choose two.)
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
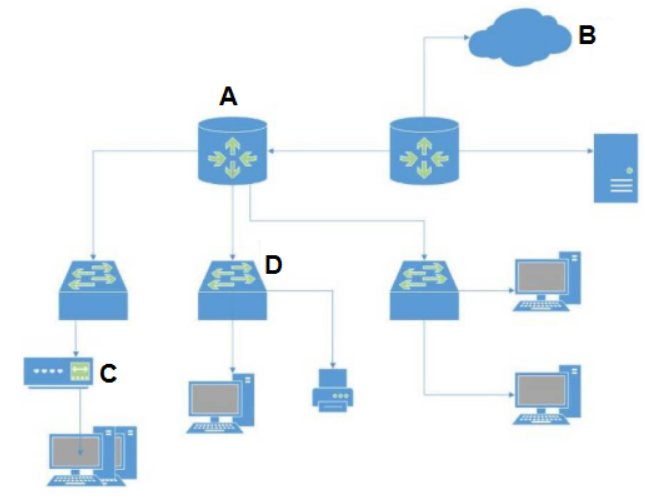
In the network diagram below, which device is the router?