Paloalto Networks PCCSE - Prisma Certified Cloud Security Engineer
What are the two ways to scope a CI policy for image scanning? (Choose two.)
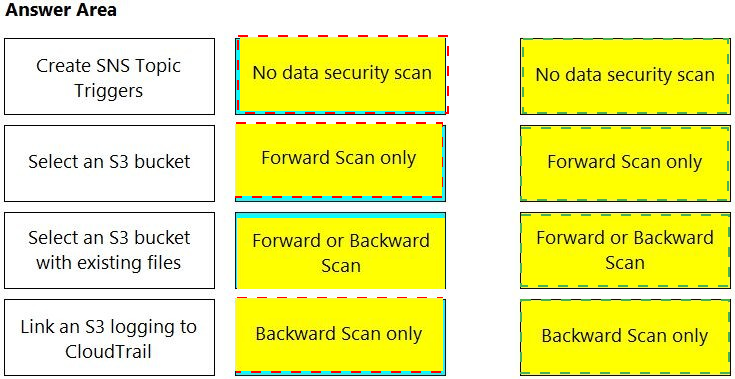
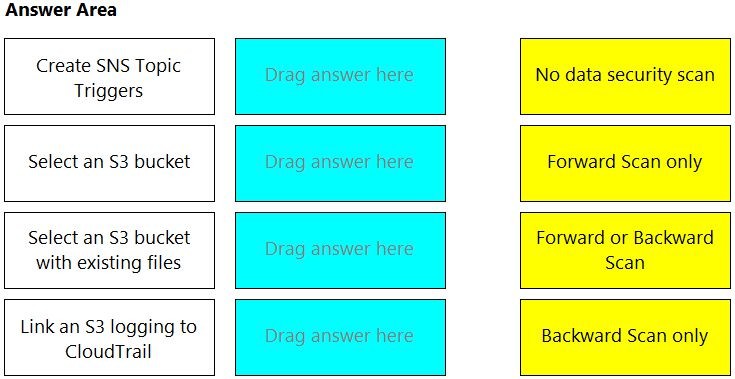
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
Which “kind†of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
What will happen when a Prisma Cloud Administrator has configured agentless scanning in an environment that also has Host and Container Defenders deployed?
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time.
What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application. The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
Which two statements are true about the differences between build and run config policies? (Choose two.)
Which field is required during the creation of a custom config query?
The security team wants to target a CNAF policy for specific running Containers. How should the administrator scope the policy to target the Containers?
Given the following audit event activity snippet:
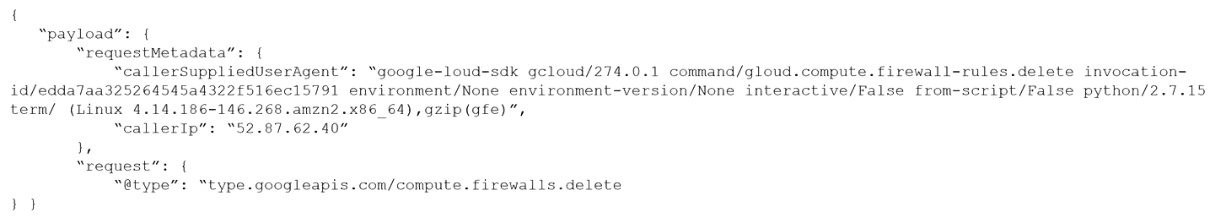
Which RQL will be triggered by the audit event?
A)
B)
C)
D)