Paloalto Networks PCCSE - Prisma Certified Cloud Security Engineer
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
Which component of a Kubernetes setup can approve, modify, or reject administrative requests?
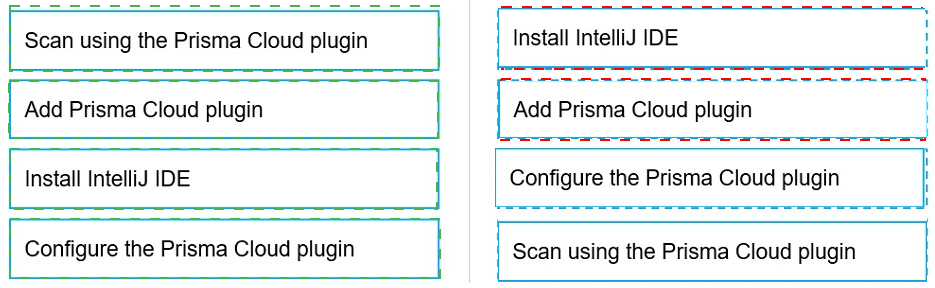
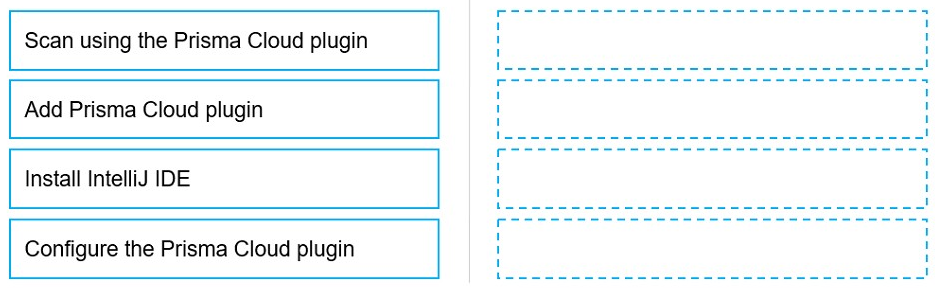
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
Which three platforms support the twistcli tool? (Choose three.)
What are two built-in RBAC permission groups for Prisma Cloud? (Choose two.)
What is the default namespace created by Defender DaemonSet during deployment?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
What is the behavior of Defenders when the Console is unreachable during upgrades?
What is the function of the external ID when onboarding a new Amazon Web Services (AWS) account in Prisma Cloud?