Paloalto Networks PCNSA - Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)
Which two Palo Alto Networks security management tools provide a consolidated creation of policies, centralized management and centralized threat intelligence. (Choose two.)
What must be configured before setting up Credential Phishing Prevention?
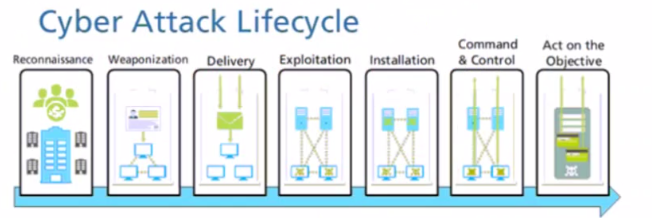
Given the cyber-attack lifecycle diagram identify the stage in which the attacker can run malicious code against a vulnerability in a targeted machine.
Which information is included in device state other than the local configuration?
Which type of address object is "10 5 1 1/0 127 248 2"?
Which DNS Query action is recommended for traffic that is allowed by Security policy and matches Palo Alto Networks Content DNS Signatures?
Which component is a building block in a Security policy rule?
Review the Screenshot:
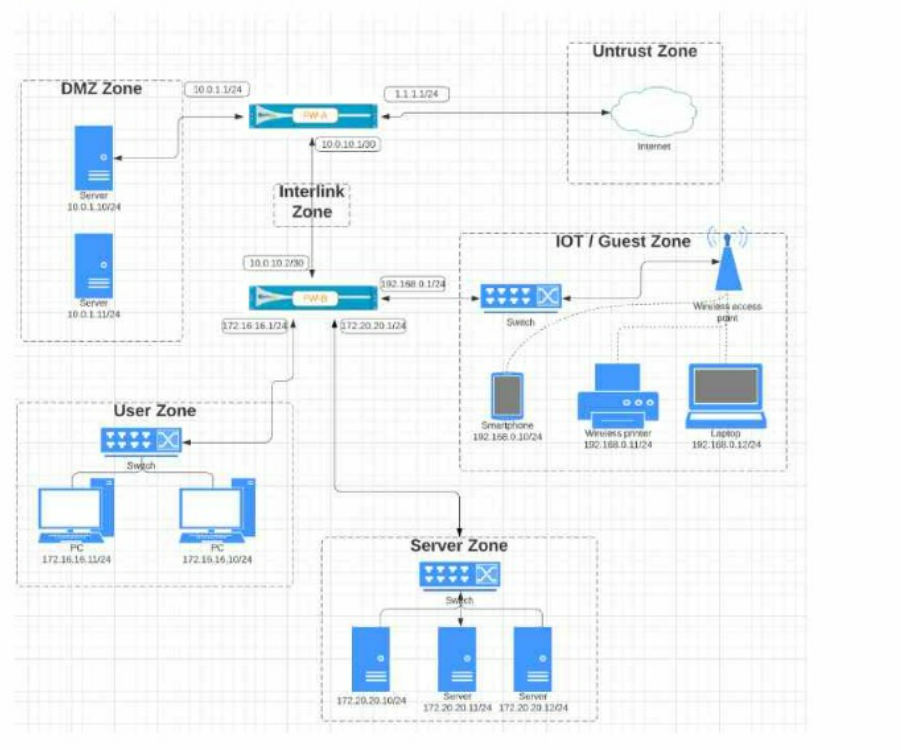
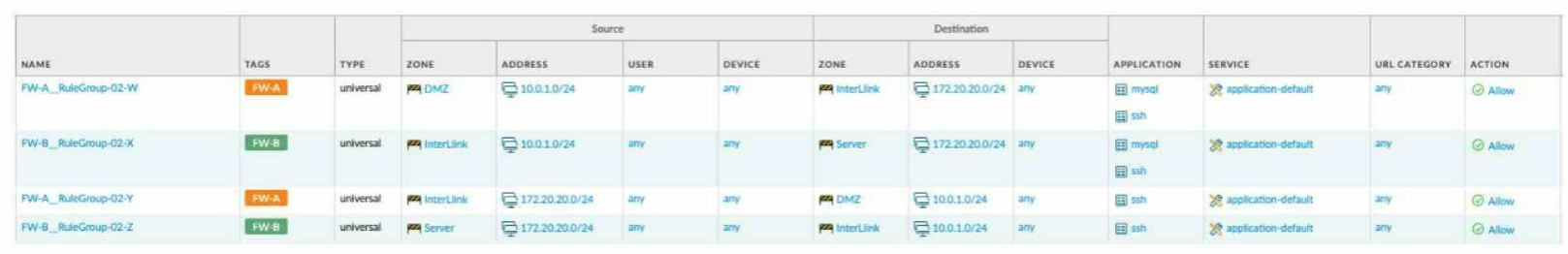
Given the network diagram, traffic must be permitted for SSH and MYSQL from the DMZ to the SERVER zones, crossing two firewalls. In addition, traffic should be permitted from the
SERVER zone to the DMZ on SSH only.
Which rule group enables the required traffic?
A)
B)
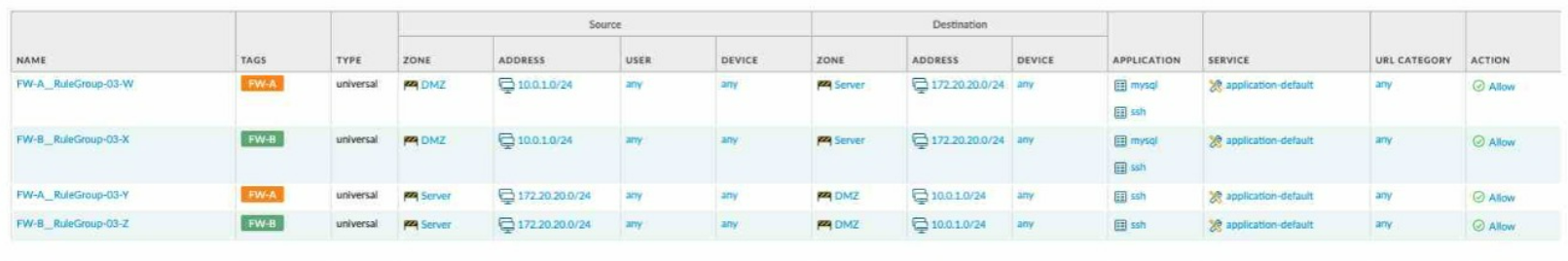
C)
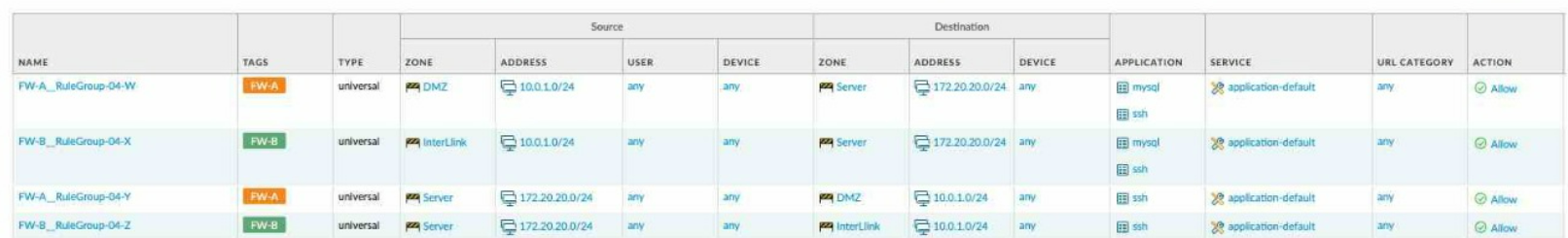
D)
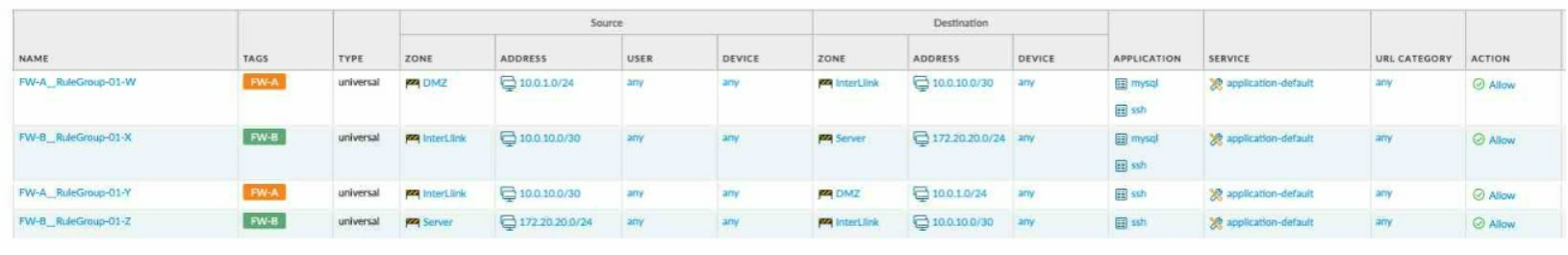
What are two valid selections within an Antivirus profile? (Choose two.)
Access to which feature requires PAN-OS Filtering licens?



