Paloalto Networks PCNSA - Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)
Which three types of authentication services can be used to authenticate user traffic flowing through the firewalls data plane? (Choose three )
A server-admin in the USERS-zone requires SSH-access to all possible servers in all current and future Public Cloud environments. All other required connections have already been enabled between the USERS- and the OUTSIDE-zone. What configuration-changes should the Firewall-admin make?
Which firewall plane provides configuration, logging, and reporting functions on a separate processor?
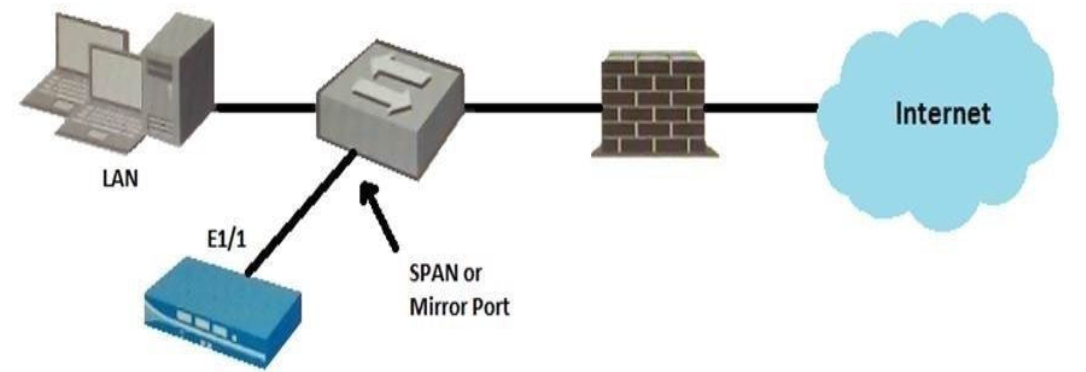
Given the topology, which zone type should you configure for firewall interface E1/1?
An internal host wants to connect to servers of the internet through using source NAT.
Which policy is required to enable source NAT on the firewall?
Which type of profile must be applied to the Security policy rule to protect against buffer overflows illegal code execution and other attempts to exploit system flaws?
An administrator would like to block access to a web server, while also preserving resources and minimizing half-open sockets. What are two security policy actions the administrator can select? (Choose two.)
What is the best-practice approach to logging traffic that traverses the firewall?
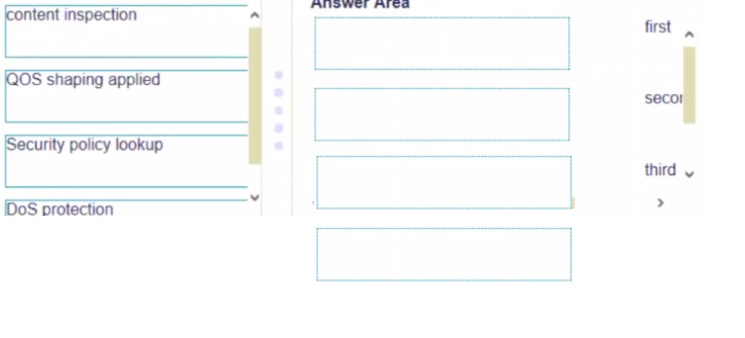
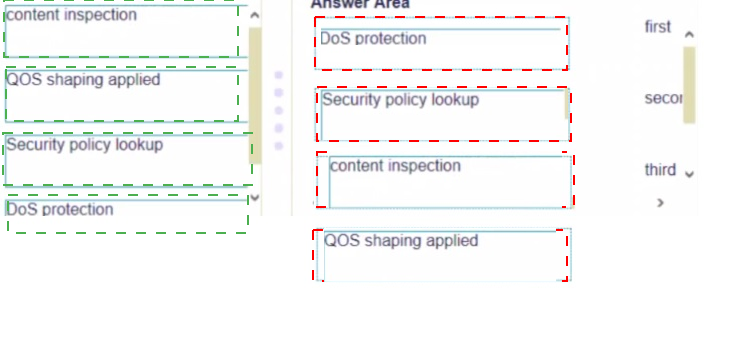
Place the following steps in the packet processing order of operations from first to last.