Paloalto Networks PCNSE - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
In a template, which two objects can be configured? (Choose two.)
Which three items must be configured to implement application override? (Choose three )
A network security engineer needs to ensure that virtual systems can communicate with one another within a Palo Alto Networks firewall. Separate virtual routers (VRs) are created for each virtual system.
In addition to confirming security policies, which three configuration details should the engineer focus on to ensure communication between virtual systems? (Choose three.)
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates. Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
Refer to Exhibit:
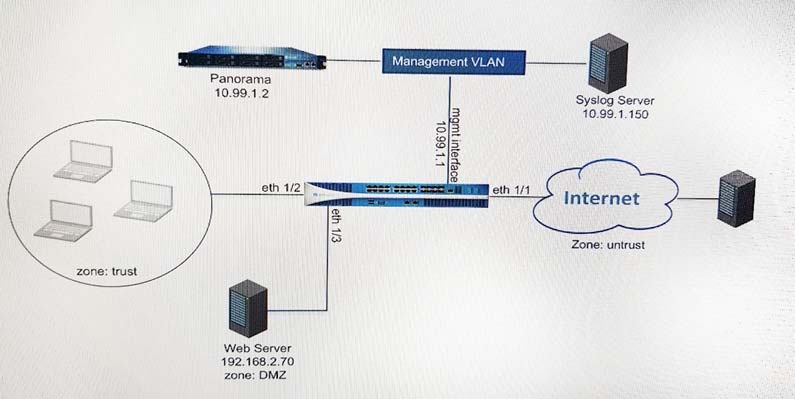
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
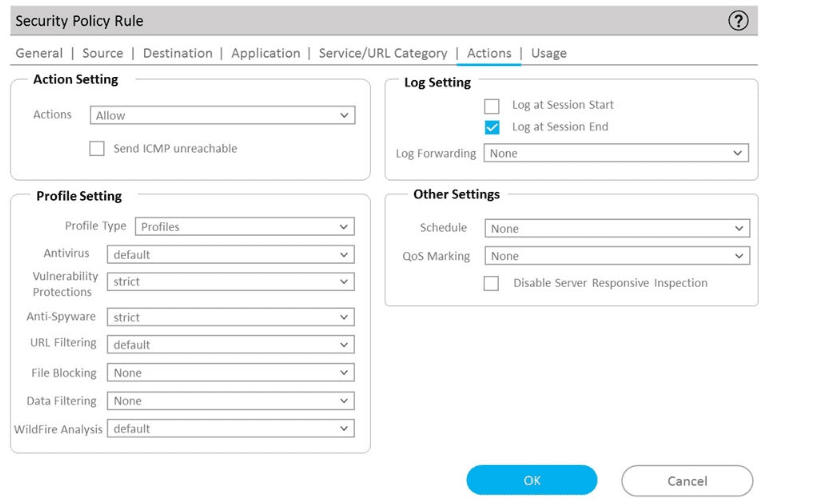
B)
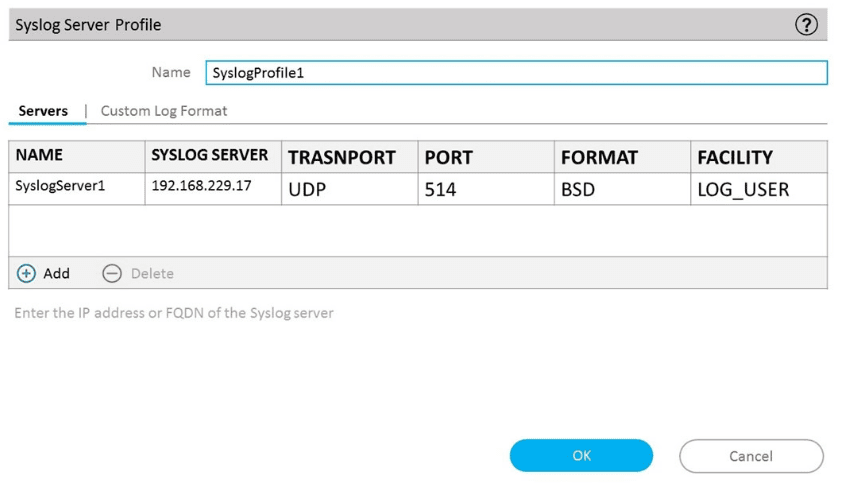
C)
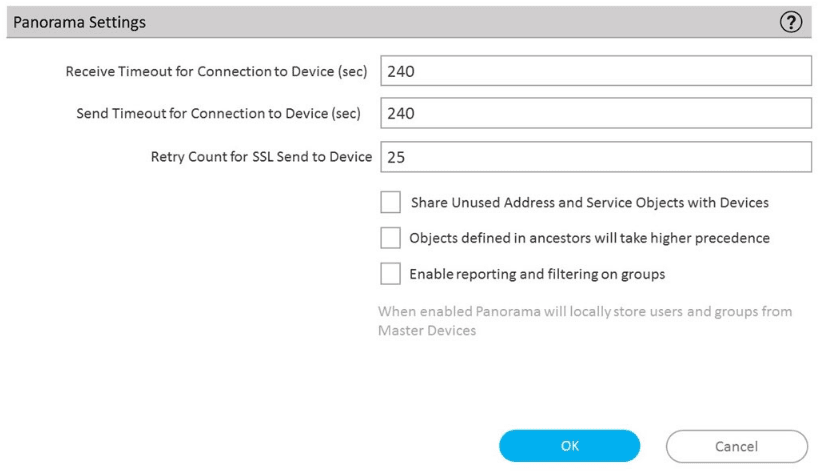
D)
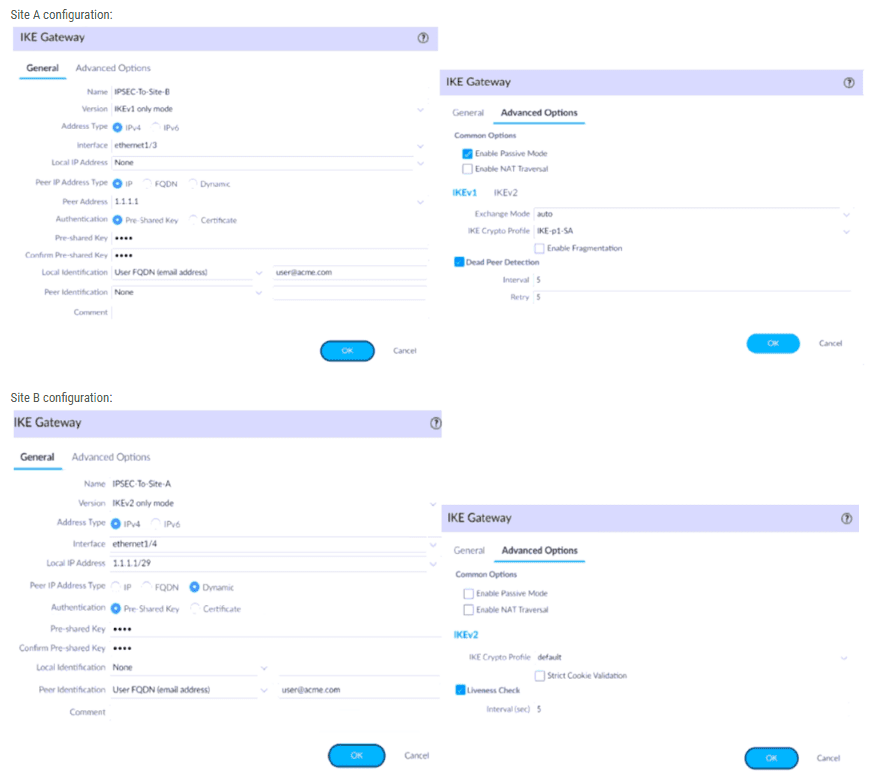
A firewall administrator is configuring an IPSec tunnel between Site A and Site B. The Site A firewall uses a DHCP assigned address on the outside interface of the firewall, and the Site B firewall uses a static IP address assigned to the outside interface of the firewall. However, the use of dynamic peering is not working.
Refer to the two sets of configuration settings provided. Which two changes will allow the configurations to work? (Choose two.)
Site A configuration:
The server team is concerned about the high volume of logs forwarded to their syslog server, it is determined that DNS is generating the most logs per second. The risk and compliance team requests that any Traffic logs indicating port abuse of port 53 must still be forwarded to syslog. All other DNS. Traffic logs can be exclude from syslog forwarding. How should syslog log forwarding be configured?
A firewall engineer has determined that, in an application developed by the company's internal team, sessions often remain idle for hours before the client and server exchange any data. The application is also currently identified as unknown-tcp by the firewalls. It is determined that because of a high level of trust, the application does not require to be scanned for threats, but it needs to be properly identified in Traffic logs for reporting purposes.
Which solution will take the least time to implement and will ensure the App-ID engine is used to identify the application?



