Paloalto Networks PCNSE - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
To ensure that a Security policy has the highest priority, how should an administrator configure a Security policy in the device group hierarchy?
What is the best definition of the Heartbeat Interval?
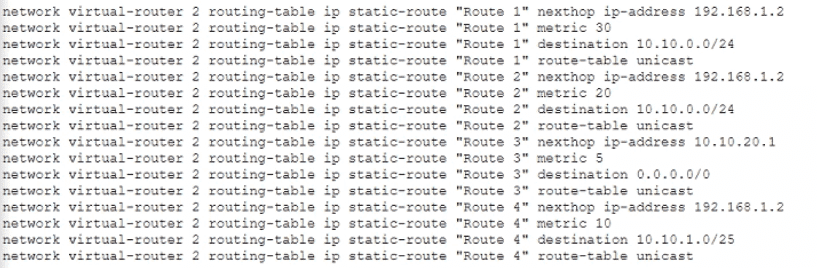
Given the following configuration, which route is used for destination 10 10 0 4?
Which tool can gather information about the application patterns when defining a signature for a custom application?
If an administrator wants to apply QoS to traffic based on source, what must be specified in a QoS policy rule?
A firewall administrator has been tasked with ensuring that all Panorama configuration is committed and pushed to the devices at the end of the day at a certain time. How can they achieve this?
Which new PAN-OS 11.0 feature supports IPv6 traffic?
What should an engineer consider when setting up the DNS proxy for web proxy?
An engineer is tasked with decrypting web traffic in an environment without an established PKI When using a self-signed certificate generated on the firewall which type of certificate should be in? approved web traffic?
Review the screenshot of the Certificates page.
An administrator for a small LLC has created a series of certificates as shown, to use for a planned Decryption roll out. The administrator has also installed the self-signed root certificate in all client systems.
When testing, they noticed that every time a user visited an SSL site, they received unsecured website warnings.
What is the cause of the unsecured website warnings?



