Paloalto Networks PCNSE - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
An engineer is troubleshooting a traffic-routing issue.
What is the correct packet-flow sequence?
How can a firewall engineer bypass App-ID and content inspection features on a Palo Alto Networks firewall when troubleshooting?
Which two items must be configured when implementing application override and allowing traffic through the firewall? (Choose two.)
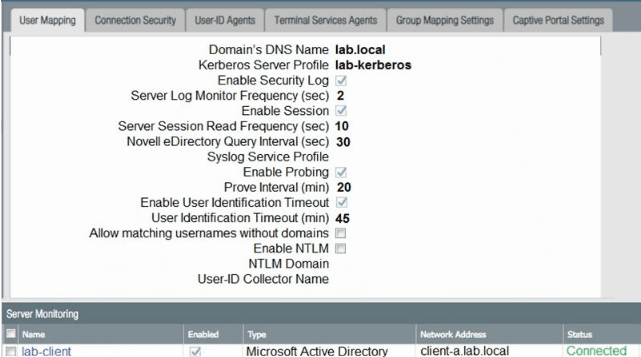
Based on the graphic which statement accurately describes the output shown in the Server Monitoring panel?
What happens when the log forwarding built-in action with tagging is used?
Which translated port number should be used when configuring a NAT rule for transparent proxy?
A firewall administrator has configured User-ID and deployed GlobalProtect, but there is no User-ID showing in the traffic logs.
How can the administrator ensure that User-IDs are populated in the traffic logs?
An engineer is pushing configuration from Panorama to a managed firewall What happens when the pushed Panorama configuration has Address Object names that duplicate the Address Objects already configured on the firewall?
A company CISO updates the business Security policy to identify vulnerable assets and services and deploy protection for quantum-related attacks. As a part of this update, the firewall team is reviewing the cryptography used by any devices they manage. The firewall architect is reviewing the Palo Alto Networks NGFWs for their VPN tunnel configurations. It is noted in the review that the NGFWs are running PAN-OS 11.2. Which two NGFW settings could the firewall architect recommend to deploy protections per the new policy? (Choose two)
When creating a Policy-Based Forwarding (PBF) policy, which two components can be used? (Choose two.)



