Paloalto Networks PCNSE - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
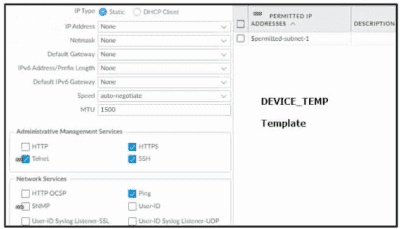
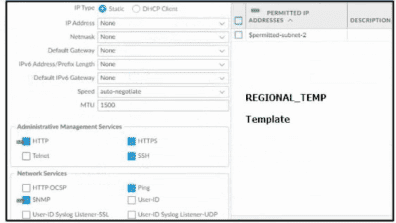
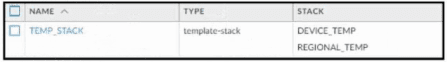
Based on the images below, and with no configuration inside the Template Stack itself, what access will the device permit on its management port?
Which protocol is supported by Global Protect clientless VPN
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
Which Panorama feature protects logs against data loss if a Panorama server fails?
An engineer troubleshoots a Panorama-managed firewall that is unable to reach the DNS servers configured via a global template. As a troubleshooting step, the engineer needs to configure a local DNS server in place of the template value.
Which two actions can be taken to ensure that only the specific firewall is affected during this process? (Choose two )
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules.
How can this be achieved?
What action does a firewall take when a Decryption profile allows unsupported modes and unsupported traffic with TLS 1.2 protocol traverses the firewall?
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
A company has a PA-3220 NGFW at the edge of its network and wants to use active directory groups in its Security policy rules. There are 1500 groups in its active directory. An engineer has been provided 800 active directory groups to be used in the Security policy rules.
What is the engineer's next step?
An administrator pushes a new configuration from Panorama to a par of firewalls that are configured as an active/passive HA pair. Which NGFW receives the from Panorama?



