Paloalto Networks PCNSE - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates.
Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
SAML SLO is supported for which two firewall features? (Choose two.)
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
An administrator configures two VPN tunnels to provide for failover and uninterrupted VPN service. What should an administrator configure to enable automatic failover to the backup tunnel?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
An administrator has purchased WildFire subscriptions for 90 firewalls globally.
What should the administrator consider with regards to the WildFire infra-structure?
Which conditions must be met when provisioning a high availability (HA) cluster? (Choose two.)
A firewall administrator needs to check which egress interface the firewall will use to route the IP 10.2.5.3.
Which command should they use?
Which three actions can Panorama perform when deploying PAN-OS images to its managed devices? (Choose three.)
Exhibit.
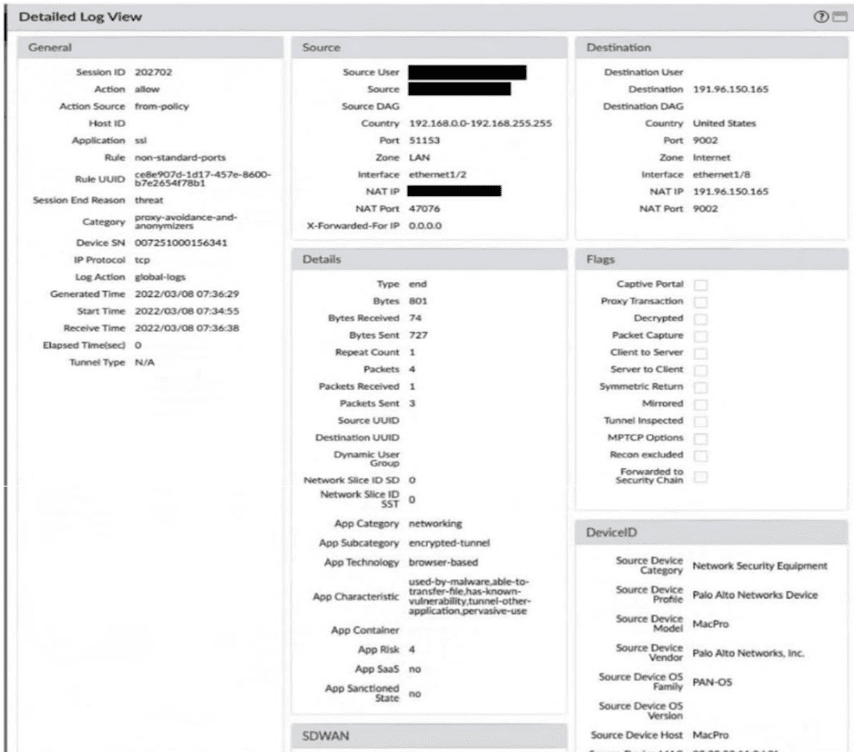
Given the screenshot, how did the firewall handle the traffic?



