CompTIA PT0-002 - CompTIA PenTest+ Certification Exam
A penetration tester captured the following traffic during a web-application test:
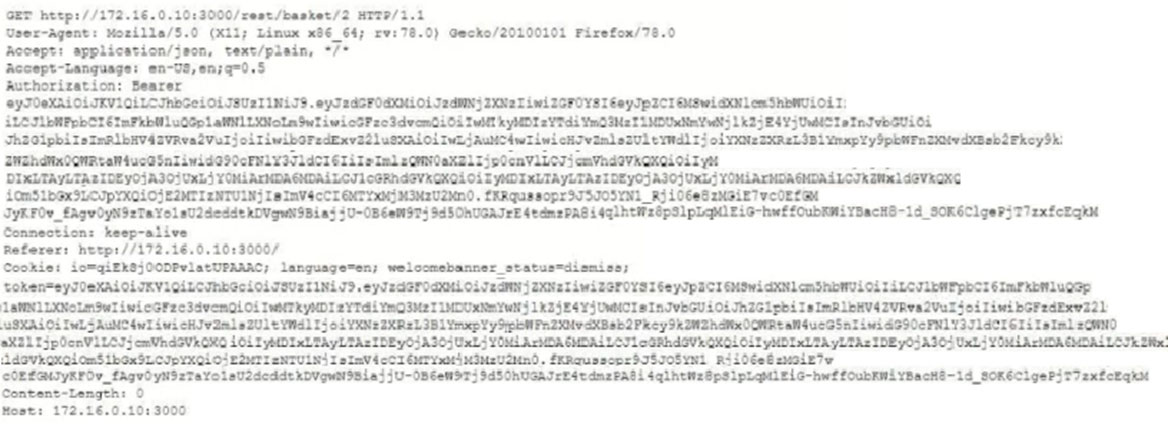
Which of the following methods should the tester use to visualize the authorization information being transmitted?
A penetration tester is trying to restrict searches on Google to a specific domain. Which of the following commands should the penetration tester consider?
Which of the following documents is agreed upon by all parties associated with the penetration-testing engagement and defines the scope, contacts, costs, duration, and deliverables?
A CentOS computer was exploited during a penetration test. During initial reconnaissance, the penetration tester discovered that port 25 was open on an internal
Sendmail server. To remain stealthy, the tester ran the following command from the attack machine:
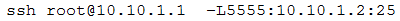
Which of the following would be the BEST command to use for further progress into the targeted network?
Appending string values onto another string is called:
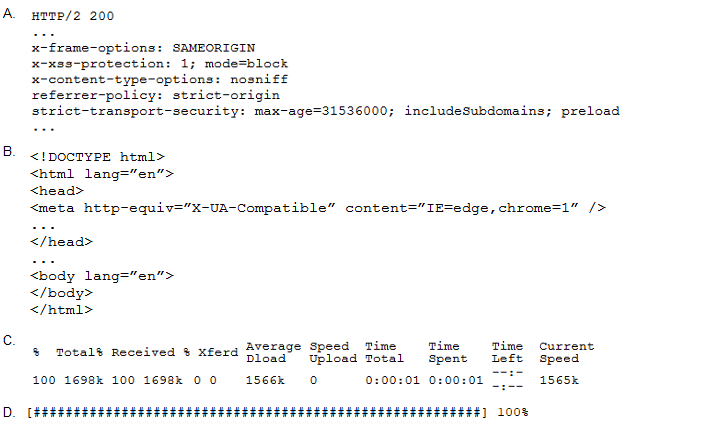
A penetration tester performs the following command:
curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
A penetration tester wrote the following script to be used in one engagement:
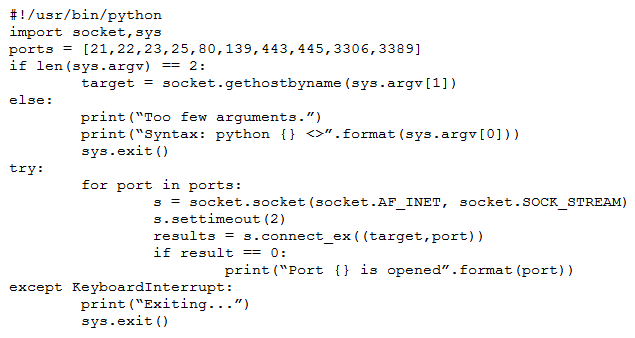
Which of the following actions will this script perform?



