CompTIA PT0-002 - CompTIA PenTest+ Certification Exam
A penetration tester is conducting a test after hours and notices a critical system was taken down. Which of the following contacts should be notified first?
Within a Python script, a line that states print (var) outputs the following:
[{'1' : 'CentOS', '2' : 'Ubuntu'), {'1' : 'Windows 10', '2' : 'Windows Server 2016'}]
Which of the following objects or data structures is var ?
An organization is using Android mobile devices but does not use MDM services. Which of the following describes an existing risk present in this scenario?
An external consulting firm is hired to perform a penetration test and must keep the confidentiality of the security vulnerabilities and the private data found in a customer's systems. Which of the following documents addresses this requirement?
During a vulnerability scan a penetration tester enters the following Nmap command against all of the non-Windows clients:
nmap -sX -T4 -p 21-25, 67, 80, 139, 8080 192.168.11.191
The penetration tester reviews the packet capture in Wireshark and notices that the target responds with an RST packet flag set for all of the targeted ports. Which of the following does this information most likely indicate?
During a client engagement, a penetration tester runs the following Nmap command and obtains the following output:
nmap -sV -- script ssl-enum-ciphers -p 443 remotehost
| TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
| TLS_ECDHE_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_RC4_128_SHA (rsa 2048)
TLS_RSA_WITH_RC4_128_MD5 (rsa 2048)
Which of the following should the penetration tester include in the report?
A penetration tester is conducting an assessment on 192.168.1.112. Given the following output:
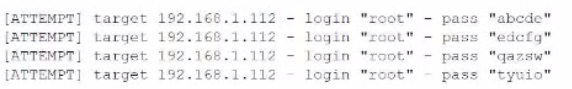
Which of the following is the penetration tester conducting?
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
A penetration testing firm wants to hire three additional consultants to support a newly signed long-term contract with a major customer. The following is a summary of candidate
background checks:

Which of the following candidates should most likely be excluded from consideration?
In a standard engagement, a post-report document is provided outside of the report. This document:
• Does not contain specific findings
• Exposes vulnerabilities
• Can be shared publicly with outside parties that do not have an in-depth understanding about the client's network
Which of the following documents is described?



