Paloalto Networks Practitioner - Palo Alto Networks Cybersecurity Practitioner (PCCP)
Total 227 questions
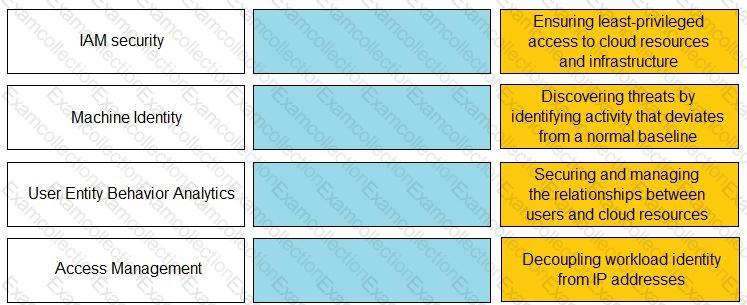
Match the Identity and Access Management (IAM) security control with the appropriate definition.
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
Which key component is used to configure a static route?
Which type of attack involves sending data packets disguised as queries to a remote server, which then sends the data back to the attacker?
Which next-generation firewall (NGFW) deployment option provides full application visibility into Kubernetes environments?
Which type of attack includes exfiltration of data as a primary objective?
The customer is responsible only for which type of security when using a SaaS application?
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
How does DevSecOps improve the Continuous Integration/Continuous Deployment (CI/CD) pipeline?
What does “forensics†refer to in a Security Operations process?




