Paloalto Networks Practitioner - Palo Alto Networks Cybersecurity Practitioner (PCCP)
Total 227 questions
Which component of cloud security uses automated testing with static application security testing (SAST) to identify potential threats?
Which of these ports is normally associated with HTTPS?
At which layer of the OSI model are routing protocols defined?
Which native Windows application can be used to inspect actions taken at a specific time?
Which of the following is a Routed Protocol?
How does adopting a serverless model impact application development?
What is an advantage of virtual firewalls over physical firewalls for internal segmentation when placed in a data center?
What is a reason IoT devices are more susceptible to command-and-control (C2) attacks?
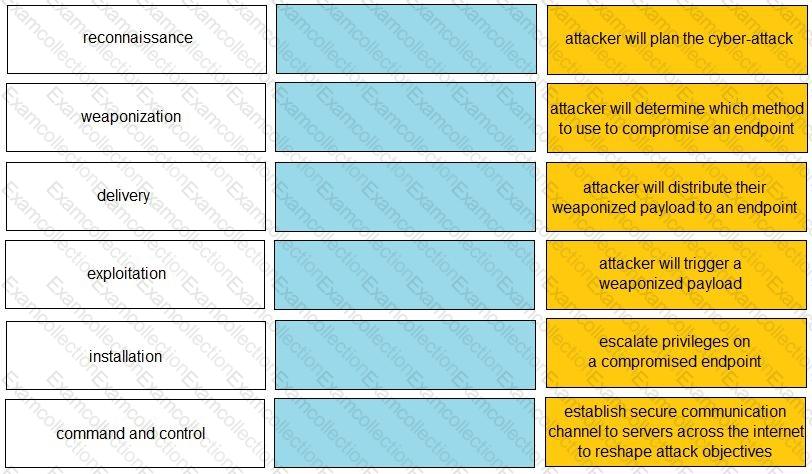
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?




