Qlik QSSA2018 - Qlik Sense System Administrator Certification Exam - June 2018 Release
A company recently experienced a merger and needs to integrate new users into the Qlik Sense environment.
A system administrator must make sure that the system sizing and the tokens match the requirements for all employees in the future.
The system administrator learns the following information.
* 450 active Qlik Sense users before the merger
* 300 new Qlik Sense users
* 500 current token licenses
* Reloads must have the same performance as before the merger
* The number or apps will approximately double
Management request an estimate from the system administrator about server resources and additional license.
Which set of tools should the system administrator use to meet these requirements?
A system administrator must make sure that only members of the "Dov" Active Directory group have the Work stream and are able to create Qlik Sense apps.
The administrator creates a security rule that only allows member of the "Dov" group to create apps. but other users can still see the Personal Work area and are able to create apps
What is the cause of this issue?
Which option should the system administrator recommend?
A data architect creates an app in Qlik Sense Desktop with an ODBC data connection from Apache Hive using a single sign-on solution (SSO). When the app os published in the huib, the data connection fails.
A system administrator tests the login credentials for the ODBC connection on the server and is able to access the database.
Why does the data connection fail?
Poor performance has been reported in a Qlik Sense environment. End users are losing connectivity to the system. When end users are eventually able to log in after many attempts, navigation and app consumption is slow. Long response times each click are also reported.
A system administrator confirms the following:
* The network is stable and has good throughput
* The QliK Sense server is running virtual on dedicated resources with high-end CPUs
* The number of users in the system has NOT incrased
* The data model has NOT changed
* The number and size of apps have increased over time
Which combination of tools should be used to diagnose this issue?
A system administrator installs Qlik Sense Enle.pr.se and is tasting the product with a small team of 10 users.
The system administrator completes the following steps in the proxy configuration
* Opens all necessary ports
* Checks in MMC that there is a personal certificate on the server
* Creates a DNS entry (or an easier URL
* Tries to connect with various Internal browsers on different machines including mobile devices
* Adds the page to trusted sites in the Internet configurations
* Installs OpenSSL in the environment
Which steps should the system administrator take lo resolve this issue?
A Qlik Sense deployment is planned for 200 users initially. Within a year, the number of users will grow to 2000, with over 100 apps. Most of these users will be the organization’s firewall. There are plans to eventually allows access to some apps to users outside the firewall.
Which two deployment modes will ensure secure access to Qlik Sense apps to users outside the firewall.
Which two deployment models will ensure secure access to Qlik Sense apps by authorized users outside the firewall? (Select two.)
Refer to the exhibit.
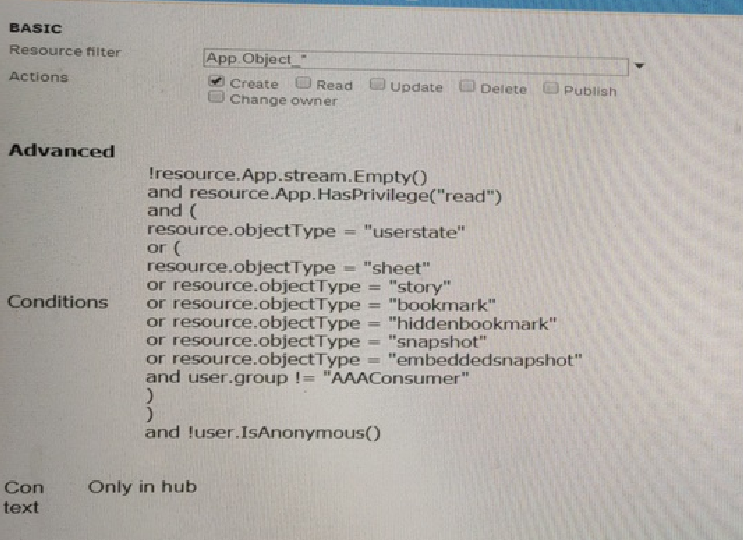
A system administrator creates the security rule shown No other custom security rules exist
What effect will the security rule have when applied to a user?
A security audit revealed problems with the newly installed multi-node environment The environment was deployed using the default settings for the central and nm nodes All possible services have been added to the rim node
The audit was based on the current IT security policy which states:
* All traffic between servers should be encrypted
* 2 56-bit encryption is required
* Traffic between client and server should be encrypted and trusted
* iOS devices must De supported
* Password length must be at least eight characters and include at least one number and one specie! character
What should the system administrator deploy to meet these requirements?
Refer to the exhibit.

A user from the HR department has access to the HR stream. The rule on the stream is:
When the user tries to open the app in the HR stream, the error in the exhibit displays.

What is causing this error?



