SNIA S10-210 - Storage Networking Management and Administration
You have received an emergency call from the night shift after they attempted to merge three small SANs in the engineering department. Once completed, all devices in SANs A and B communicate with one another but SAN C could not communicate with either of the other SANs because the fabric has become segmented.
Which statement is correct?
What is the maximum distance between two 8 Gb FC ports that can be connected using 50 µOM3 grade multimode fiber cable?
A new FC switch has been installed into the data center. You want to disable any unsecure protocols used to access the management ports.
Which two protocols should be disabled? (Choose two.)
What is a common protocol used in cloud communications?
You have been asked to create a LUN on a storage array that is comprised of 7,200 rpm SATA drives. Each drive is rated at 100 IOPS. The LUN should provide a minimum of 1100 IOPS and withstand multiple drive failures using the least number of drives.
How many drives and which RAID level should you use to create this LUN?
You have been asked to secure your FC switches in the data center. Unsecure protocols have already been disabled but you also need to restrict access to the switches only from specific IP addresses located on the production network.
What should be used?
Click the Exhibit button.
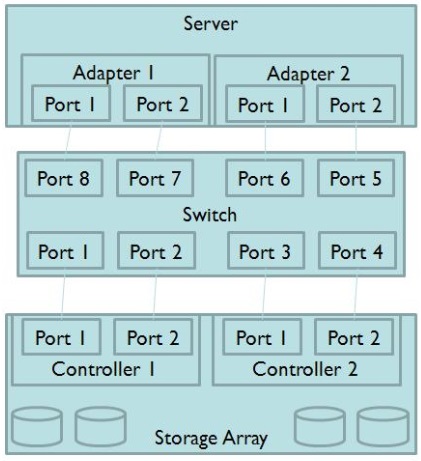
Referring to the exhibit, what are the two largest risks to a highly available solution? (Choose two.)
What describes the FCoE transport protocol?
You are using asynchronous storage replication to protect your critical database server. There are no replication agents installed on the database server. After a disaster, you are unable to bring up the database at the DR site.
What is the cause?
Which process allows for the reduction of disk space consumption on a shared storage of OS images used by 200 users?



