Microsoft SC-200 - Microsoft Security Operations Analyst
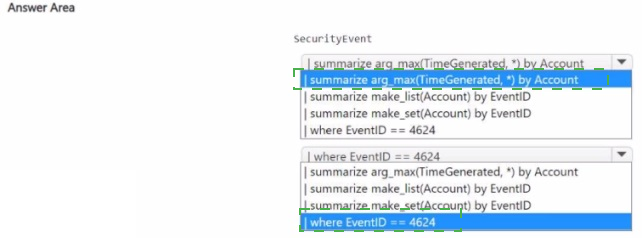
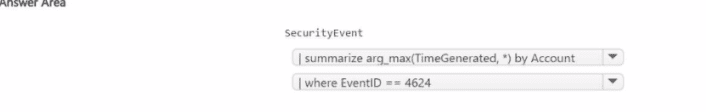
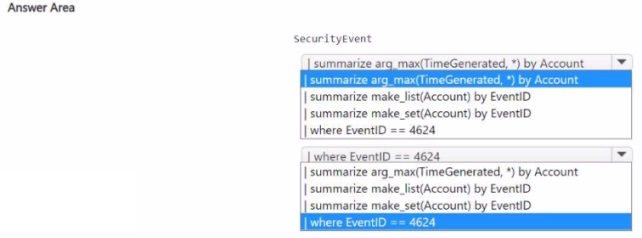
You need to build a KQL query in a Microsoft Sentinel workspace. The query must return the SecurityEvent record for accounts that have the last record with an EventID value of 4624. How should you complete the query' To answer, select the appropriate options in the answer area.
NOTE: Each coned selection is worth one point
You have a Microsoft 365 subscription that uses Microsoft Defender XOR and contains a Windows device named Oevice1. You investigate a suspicious process named Prod on Device! by using a live response session. You need to perform the following actions:
• Stop Prod.
• Send Prod for further review.
Which live response command should you run for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You recently deployed Azure Sentinel.
You discover that the default Fusion rule does not generate any alerts. You verify that the rule is enabled.
You need to ensure that the Fusion rule can generate alerts.
What should you do?
You have 100 Azure subscriptions that have enhanced security features m Microsoft Defender for Cloud enabled. All the subscriptions are linked to a single Azure AD tenant. You need to stream the Defender for Cloud togs to a syslog server. The solution must minimize administrative effort What should you do? To answer, select the appropriate options in the answer area NOTE: Each correct selection is worth one point
You have a Microsoft Sentinel workspace.
You receive multiple alerts for failed sign in attempts to an account.
You identify that the alerts are false positives.
You need to prevent additional failed sign-in alerts from being generated for the account. The solution must meet the following requirements.
• Ensure that failed sign-in alerts are generated for other accounts.
• Minimize administrative effort
What should do?
You need to ensure that the Group1 members can meet the Microsoft Sentinel requirements.
Which role should you assign to Group1?
Your company uses Microsoft Defender for Endpoint.
The company has Microsoft Word documents that contain macros. The documents are used frequently on the devices of the company’s accounting team.
You need to hide false positive in the Alerts queue, while maintaining the existing security posture. Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to implement the Defender for Cloud requirements.
Which subscription-level role should you assign to Group1?
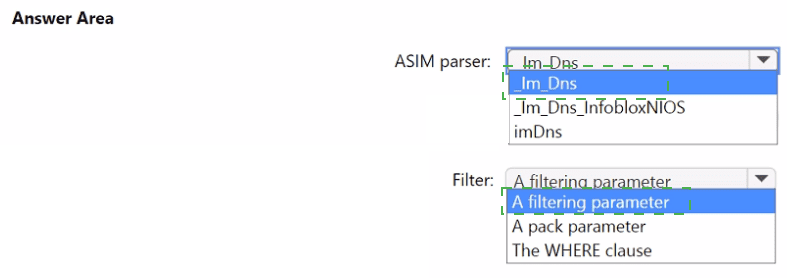
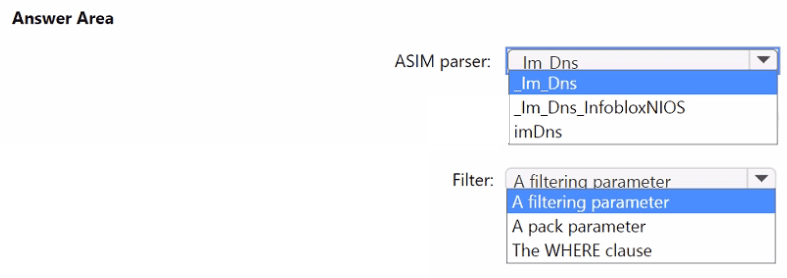
You need to implement the ASIM query for DNS requests. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to ensure that the configuration of HuntingQuery1 meets the Microsoft Sentinel requirements.
What should you do?