Microsoft SC-200 - Microsoft Security Operations Analyst
You create an Azure subscription.
You enable Microsoft Defender for Cloud for the subscription.
You need to use Defender for Cloud to protect on-premises computers.
What should you do on the on-premises computers?
You have an Azure subscription that uses Microsoft Sentinel.
You need to minimize the administrative effort required to respond to the incidents and remediate the security threats detected by Microsoft Sentinel.
Which two features should you use? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
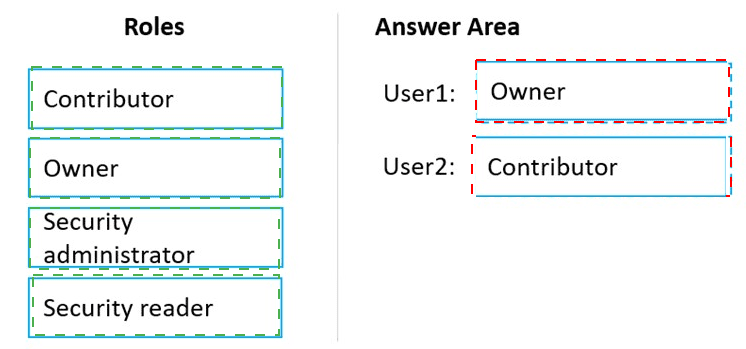
You have an Azure subscription linked to an Azure Active Directory (Azure AD) tenant. The tenant contains two users named User1 and User2.
You plan to deploy Azure Defender.
You need to enable User1 and User2 to perform tasks at the subscription level as shown in the following table.
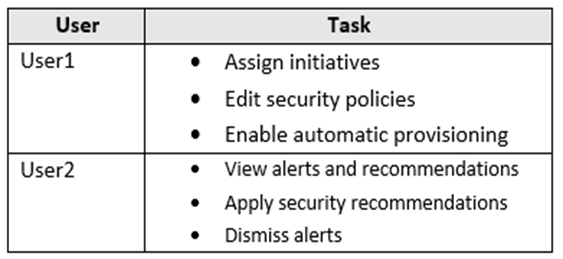
The solution must use the principle of least privilege.
Which role should you assign to each user? To answer, drag the appropriate roles to the correct users. Each role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
You are investigating a potential attack that deploys a new ransomware strain.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information.
You have three custom device groups.
You need to be able to temporarily group the machines to perform actions on the devices. Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
You have the resources shown in the following table.
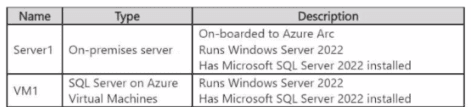
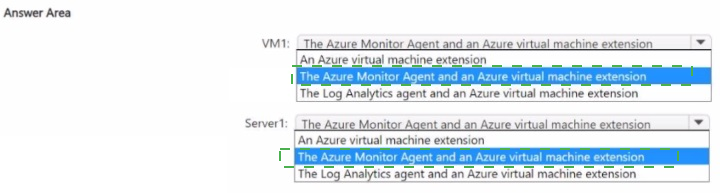
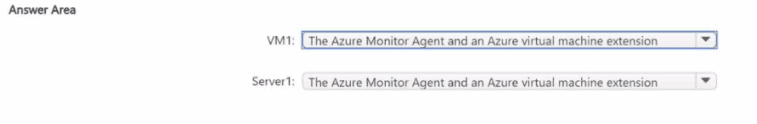
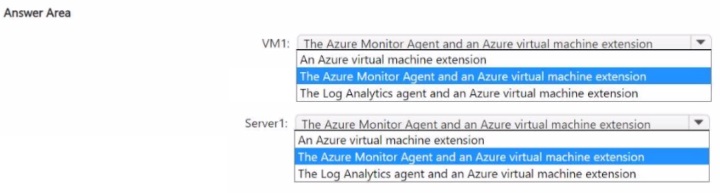
You have an Azure subscription that uses Mictosoft Defender for Cloud.
You need to use Defender for Cloud to protect VM1 and Server1. The solution must meet the following requirements:
• Support Advanced Threat Protection and vulnerability assessment
• Register each SQL Server 2022 instance as a SQL virtual machine.
• Minimize implementation and administrative effort
What should you deploy to each server? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR.
You have a query that contains the following statements.
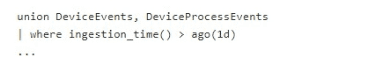
You need to configure a custom detection rule that will use the query. The solution must minimize how long it takes to be notified about events that match the query.
Which frequency should you select for the rule?
You have a Microsoft 365 B5 subscription that contains a user named User1. The subscription uses Microsoft 365 Copilot for Security. Copilot for Security uses the Sentinel plugin. User1 is assigned the Copilot Contributor role.
During an investigation, User1 submits a prompt and receives a notification that Copilot for Security cannot respond to requests because the security compute unit (SCU) usage is nearing the provisioned capacity limit.
You need to ensure that User1 can use Copilot for Security to generate a successful response.
What should User1 do?
You have a Microsoft Sentinel workspace named workspace1 that contains custom Kusto queries.
You need to create a Python-based Jupyter notebook that will create visuals. The visuals will display the results of the queries and be pinned to a dashboard. The solution must minimize development effort.
What should you use to create the visuals?
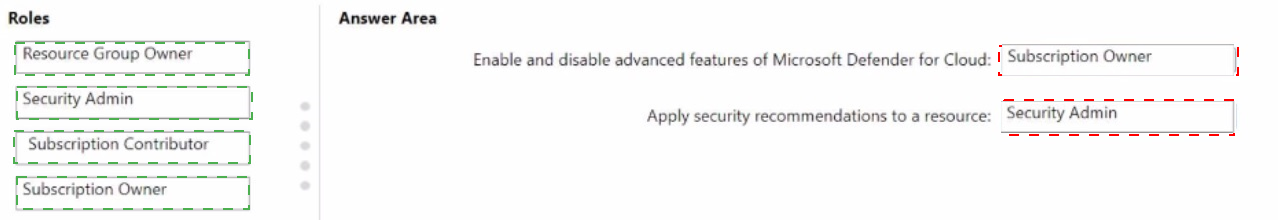
You have an Azure subscription.
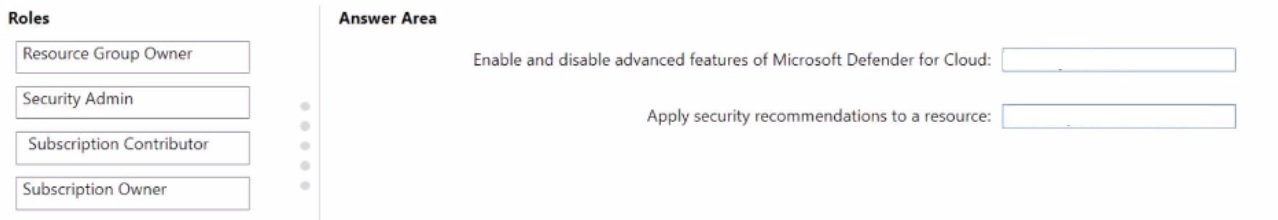
You need to delegate permissions to meet the following requirements:
• Enable and disable advanced features of Microsoft Defender for Cloud.
• Apply security recommendations to a resource.
The solution must use the principle of least privilege.
Which Microsoft Defender for Cloud role should you use for each requirement? To answer, drag the appropriate roles to the correct requirements. Each role may be used once, mote than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Your company uses Microsoft Sentinel
A new security analyst reports that she cannot assign and resolve incidents in Microsoft Sentinel.
You need to ensure that the analyst can assign and resolve incidents. The solution must use the principle of least privilege.
Which role should you assign to the analyst?