Microsoft SC-300 - Microsoft Identity and Access Administrator
Task 9
You need to ensure that when users in the Sg-Operations group go to the My Apps portal a tab named Operations appears that contains only the following applications:
• Unkedln
• Box
Task 1
You need to deploy multi factor authentication (MFA). The solution must meet the following requirements:
• Require MFA registration only for members of the Sg-Finance group.
• Exclude Debra Berger from having to register for MFA.
• Implement the solution without using a Conditional Access policy.
Task 2
You need to implement a process to review guest users who have access to the Salesforce app. The review must meet the following requirements:
• The reviews must occur monthly.
• The manager of each guest user must review the access.
• If the reviews are NOT completed within five days, access must be removed.
• If the guest user does not have a manager, Megan Bowen must review the access.
Task 8
You need to prevent all users from using legacy authentication protocols when authenticating to Microsoft Entra ID.
Task 7
You need to lock out accounts for five minutes when they have 10 failed sign-in attempts.
Task 10
You need to create a group named Audit. The solution must ensure that the members of Audit can activate the Security Reader role.
Task 6
You need to implement additional security checks before the members of the Sg-Executive can access any company apps. The members must meet one of the following conditions:
• Connect by using a device that is marked as compliant by Microsoft Intune.
• Connect by using client apps that are protected by app protection policies.
Task 3
You need to add the Linkedln application as a resource to the Sales and Marketing access package. The solution must NOT remove any other resources from the access package.
Task 5
You need to assign a Windows 10/11 Enterprise E3 license to the Sg-Retail group.
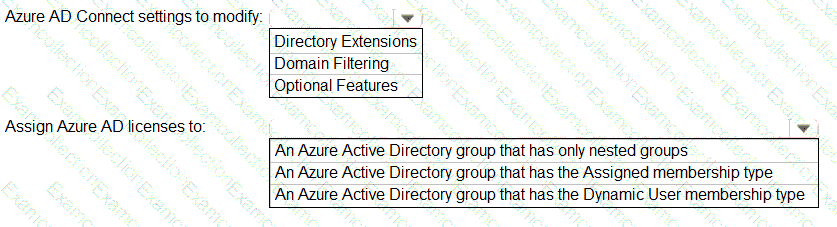
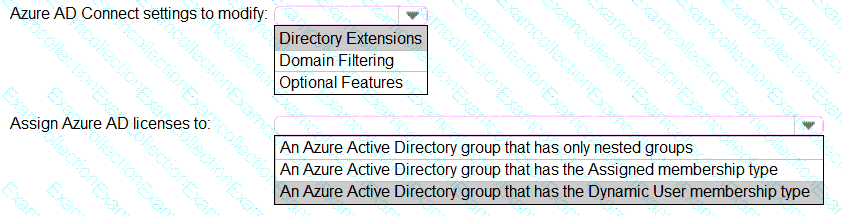
You need to configure the assignment of Azure AD licenses to the Litware users. The solution must meet the licensing requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.