Microsoft SC-401 - Administering Information Security in Microsoft 365
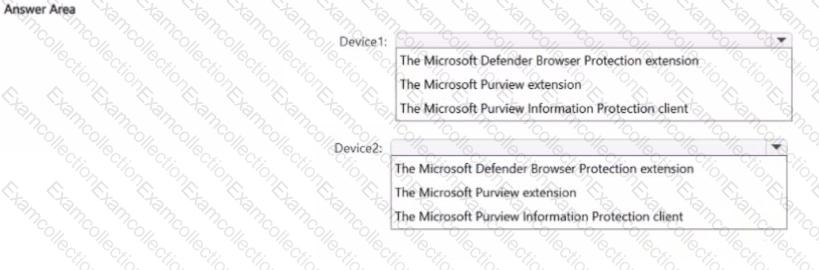
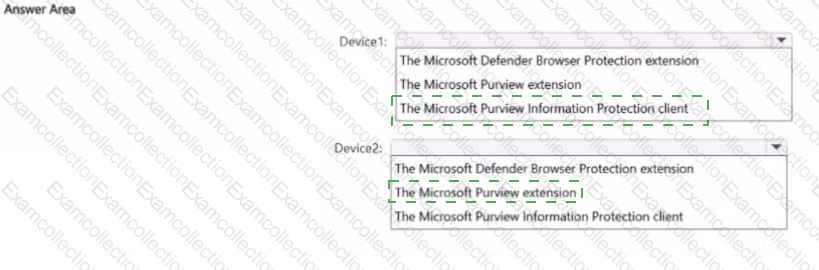
You have a Microsoft 36S ES subscription that contains two Windows devices named Devicel1and Device2 Device1 has the default browser set to Microsoft Edge. Devke2 has the default browser set to Google Chrome.
You need to ensure that Microsoft Purview insider risk management can collect signals when a user copies files to a USB device by using their default browser.
What should you deploy to each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a retention policy named RP1 as shown in the following table.
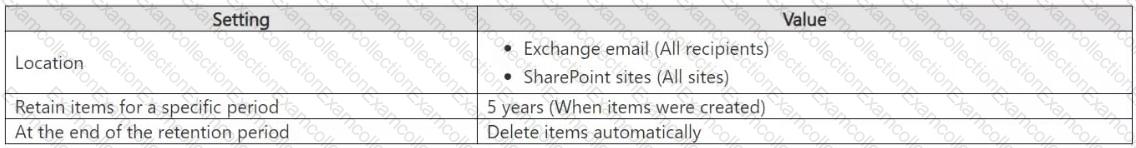
You place a preservation lock on RP1.
You need to modify RP1.
Which two modifications can you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You create and run a content search from the Microsoft Purview portal.
You need to download the results of the content search.
What should you obtain first?
You have a Microsoft J65 ES subscription.
You need to create a Microsoft Defender for Cloud Apps policy that will detect data loss prevention (DIP) violations. What should you create?
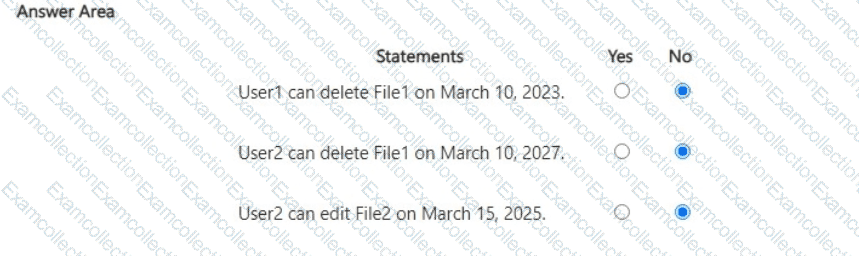
You have a Microsoft 365 subscription that contains a sensitivity label named Contoso Confidential.
You publish Contoso Confidential to all users.
Contoso Confidential is configured as shown in the Configuration exhibit. (Click the Configuration tab.)
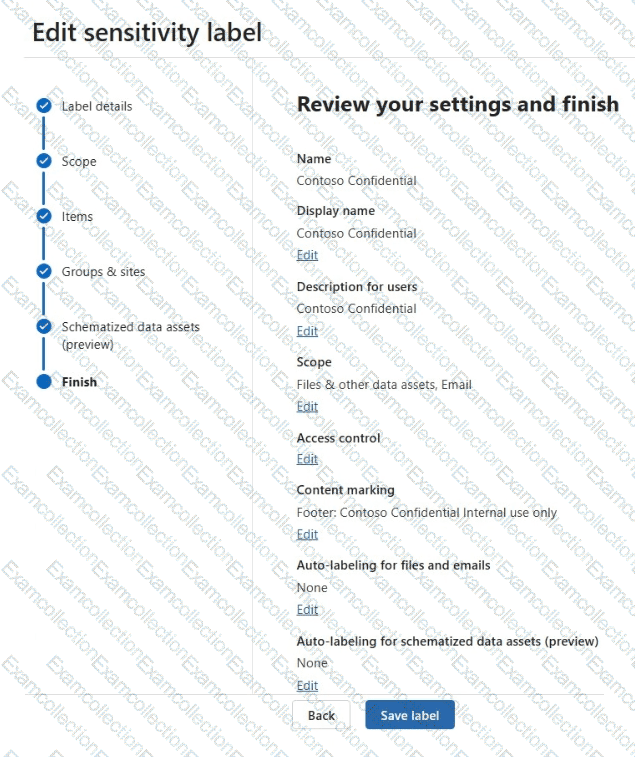
The Access control settings of Contoso Confidential are configured as shown in the Access control exhibit. (Click the Access control tab.)
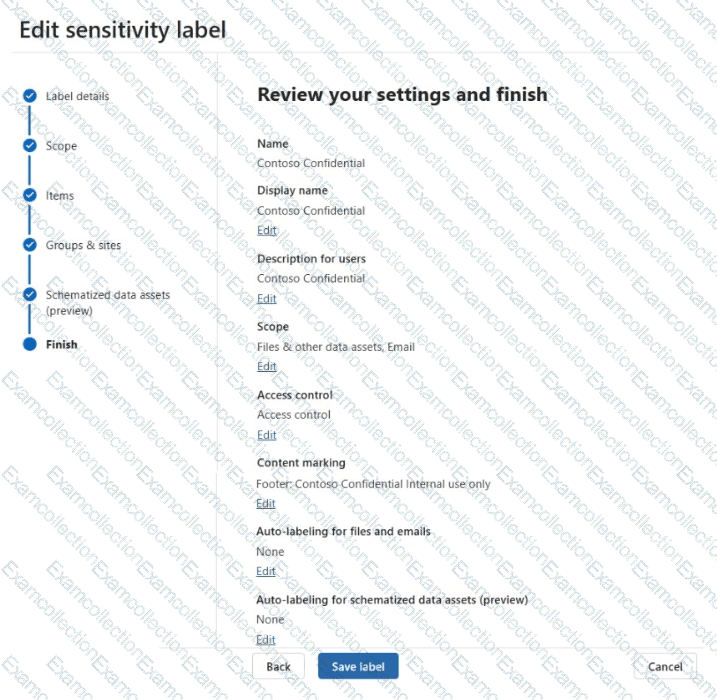
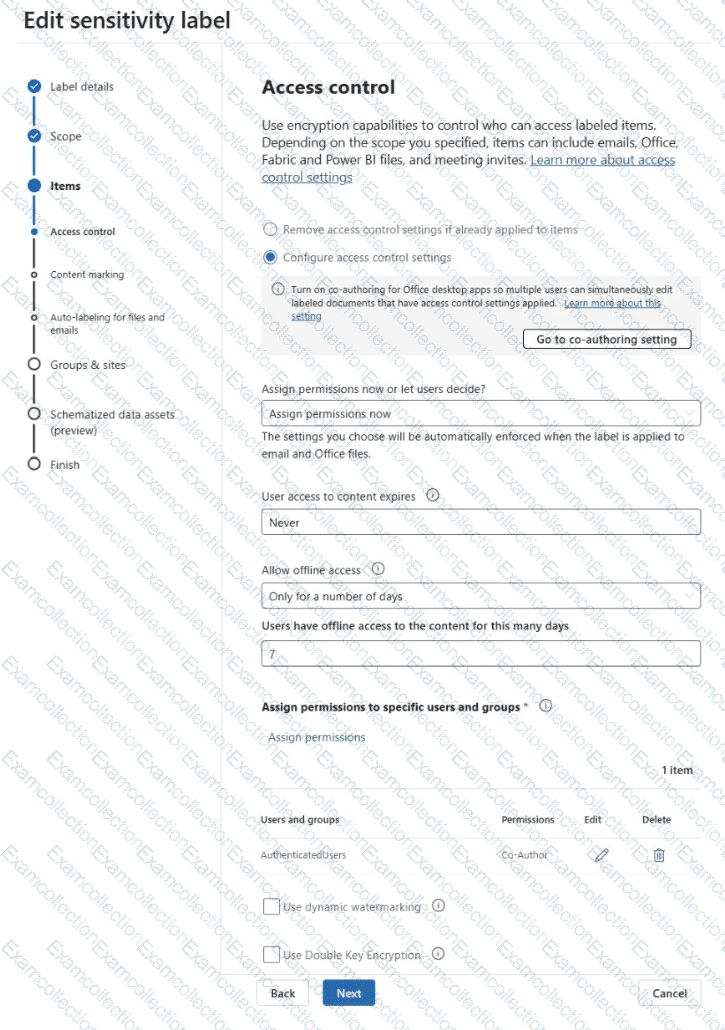
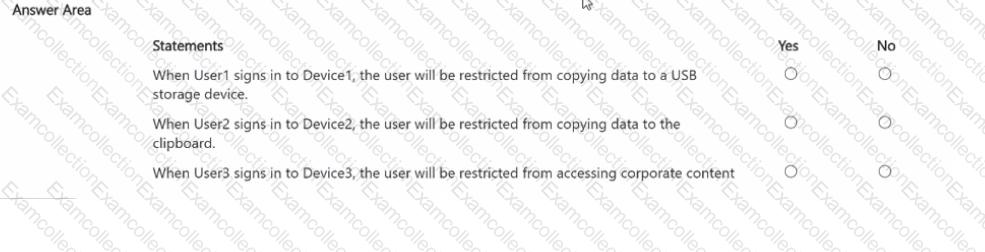
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

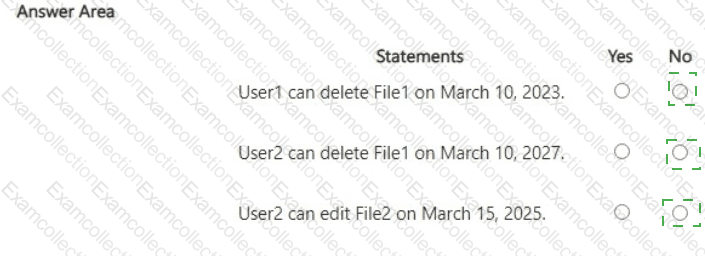
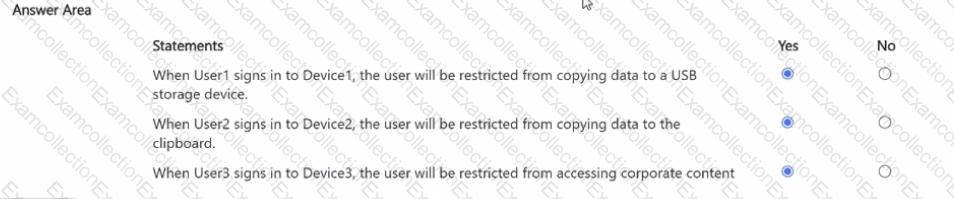
You have a Microsoft 365 E5 subscription that contains three users named U$er1, User2, and User3. The subscription contains the groups shown in the following table.
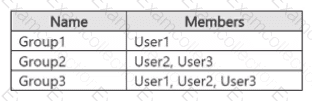
The subscription contains the devices shown in the following table.
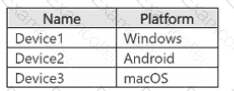
All the devices are onboarded to Microsoft Purview.
You have the data loss prevention (DLP) policies shown in the following table.
You have a Microsoft SharePoint Online site named Site1 that has the users shown in the following table.
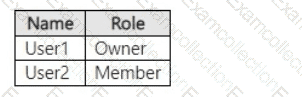
You create the retention labels shown in the following table.
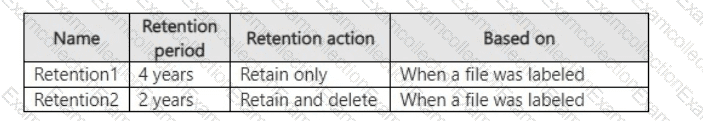
You publish the retention labels to Site1.
On March 1,2023, you assign the retention labels to the files shown in the following table.
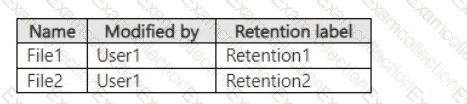
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
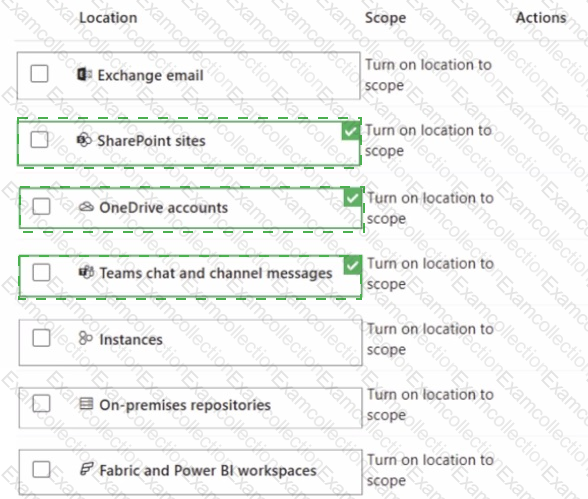
You have a Microsoft 365 tenant that uses Microsoft Teams.
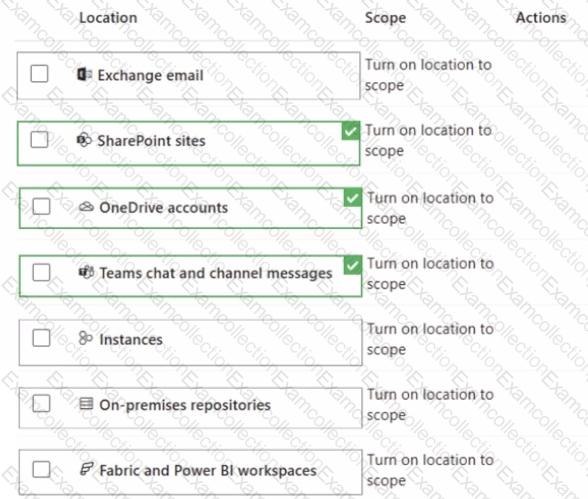
You create a data loss prevention (DLP) policy to prevent Microsoft Teams users from sharing sensitive information. You need to identify which locations must be selected to meet the following requirements:
• Documents that contain sensitive information must not be shared inappropriately in Microsoft Teams.
• If a user attempts to share sensitive information during a Microsoft Teams chat session, the message must be deleted immediately.
Which three locations should you select? To answer, select the appropriate locations in the answer area
NOTE: Each correct selection is worth one point.
You have a Microsoft SharePoint Online site named Site! that contains the files shown in the following table.

You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
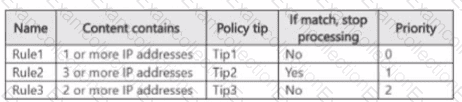
You apply DLP1 toSite1.
Which policy tips will appear for File2?
You recently discovered that the developers at your company emailed Azure Storage Account keys in plain text to third parties
You need to ensure that when Azure Storage Account keys are emailed, the emails are encrypted.
Solution: You create a data loss prevention (DLP) policy that has Exchange email, SharePoint sites, OneDrive accounts, and Teams chat and channel messages selected.
Does this meet the goal?






 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg