Microsoft SC-900 - Microsoft Security Compliance and Identity Fundamentals
Select The answer that correctly completes the sentence.

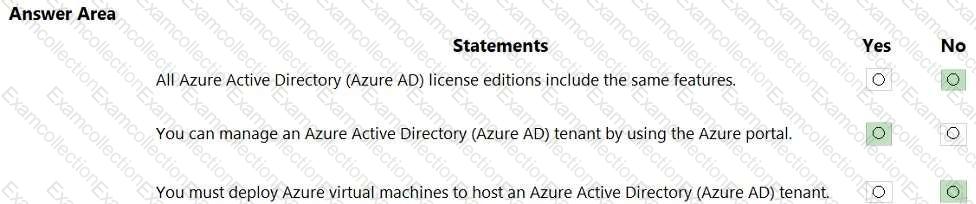
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

What are customers responsible for when evaluating security in a software as a service (SaaS) cloud services model?
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Which security feature is available in the free mode of Microsoft Defender for Cloud?
Select the answer that correctly completes the sentence.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface?
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
You have an Azure subscription that contains multiple resources.
You need to assess compliance and enforce standards for the existing resources.
What should you use?