Microsoft SC-900 - Microsoft Security Compliance and Identity Fundamentals
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

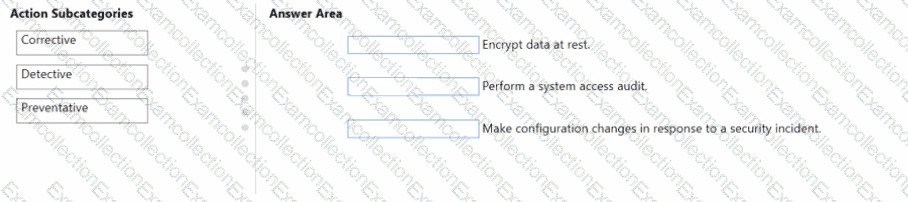
You are evaluating the compliance score in Microsoft Purview Compliance Manager.
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

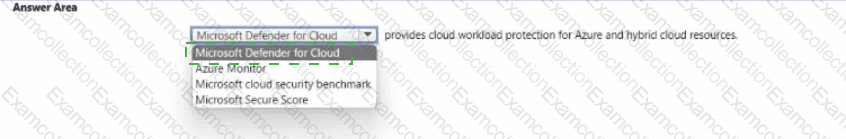
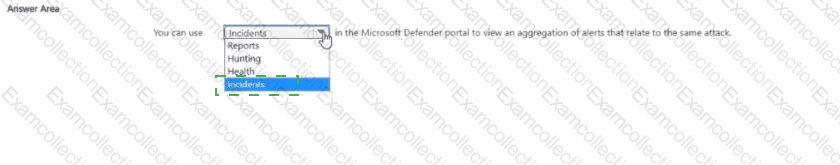
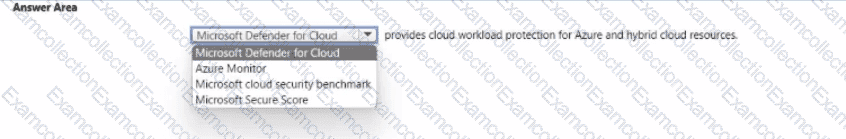
Select the answer that correctly completes the sentence.
You plan to move resources to the cloud.
You are evaluating the use of Infrastructure as a service (laaS),
Platform as a service (PaaS), and Software as a service (SaaS) cloud models.
You plan to manage only the data, user accounts, and user devices for a cloud-based app.
Which cloud model will you use?
Which compliance feature should you use to identify documents that are employee resumes?
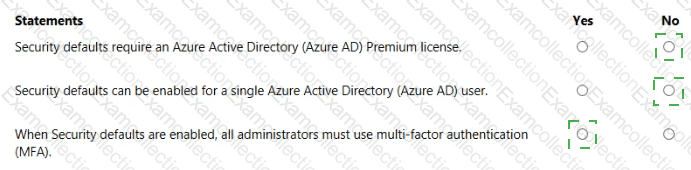
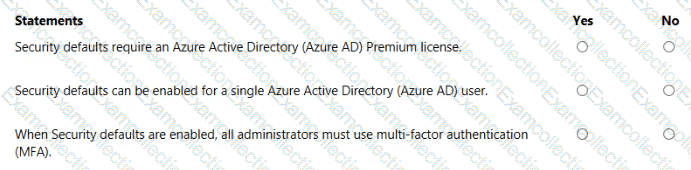
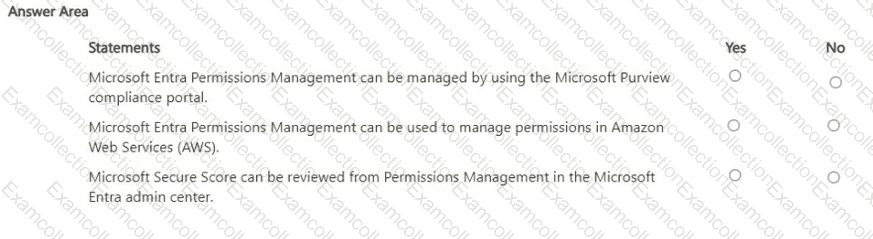
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
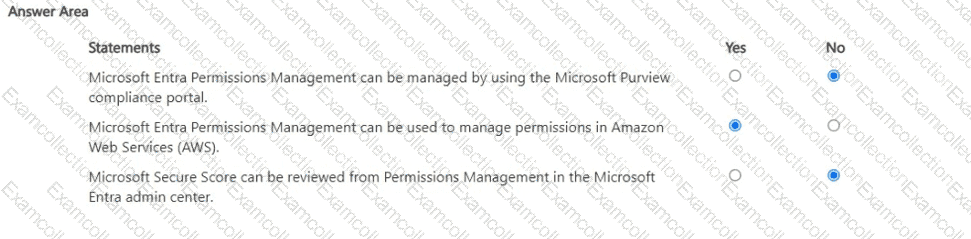
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What should you use in the Microsoft Defender portal to view security trends and track the protection status of identities?
Select the answer that correctly completes the sentence.