Amazon Web Services SCS-C02 - AWS Certified Security - Specialty
A company wants to migrate its static primary domain website to AWS. The company hosts the website and DNS servers internally. The company wants the website to enforce SSL/TLS encryption block IP addresses from outside the United States (US), and take advantage of managed services whenever possible.
Which solution will meet these requirements?
A company is running an application in The eu-west-1 Region. The application uses an IAM Key Management Service (IAM KMS) CMK to encrypt sensitive data. The company plans to deploy the application in the eu-north-1 Region.
A security engineer needs to implement a key management solution for the application deployment in the new Region. The security engineer must minimize changes to the application code.
Which change should the security engineer make to the IAM KMS configuration to meet these requirements?
A company has an application on Amazon EC2 instances that store confidential customer data. The company must restrict access to customer data. A security engineer requires secure access to the instances that host the application. According to company policy, users must not open any inbound ports, maintain bastion hosts, or manage SSH keys for the EC2 instances.
The security engineer wants lo monitor, store, and access all session activity logs. The logs must be encrypted.
Which solution will meet these requirements?
A company has an external web application that runs on Amazon EC2 instances behind an Application Load Balancer (ALB) within a VPC. The web application stores data in an Amazon RDS for MySQL DB instance. The company uses a Linux bastion host to apply schema updates to the database Administrators connect to the bastion host through SSH from their corporate workstations. The following security groups are applied to the infrastructure.
• sgLB associated with the ALB
• sgWeb associated with the EC2 instances
• sgDB associated with the DB instance
• sgBastion associated with the bastion host
Which security group configuration will meet these requirements MOST securely?
A security engineer is investigating a malware infection that has spread across a set of Amazon EC2 instances. A key indicator of the compromise is outbound traffic on TCP port 2905 to a set of command and control hosts on the internet.
The security engineer creates a network ACL rule that denies the identified outbound traffic. The security engineer applies the network ACL rule to the subnet of the EC2 instances. The security engineer must identify any EC2 instances that are trying to communtcate on TCP port 2905.
Which solution will identify the affected EC2 instances with the LEAST operational effort?
A company stores sensitive data in an Amazon S3 bucket. The company encrypts the data at rest by using server-side encryption with Amazon S3 managed keys (SSE-S3). A security engineer must prevent any modifications to the data in the S3 bucket. Which solution will meet this requirement?
A security engineer needs to suppress AWS. Security Hub findings automatically for resources that have a specific tag attached.
Which solution will meet this requirement?
A company wants to store all objects that contain sensitive data in an Amazon S3 bucket. The company will use server-side encryption to encrypt the S3 bucket. The company's operations team manages access to the company's S3 buckets. The company's security team manages access to encryption keys.
The company wants to separate the duties of the two teams to ensure that configuration errors by only one of these teams will not compromise the data by granting unauthorized access to plaintext data.
Which solution will meet this requirement?
A company uses AWS Organizations. The company wants to implement short-term cre-dentials for third-party AWS accounts to use to access accounts within the com-pany's organization. Access is for the AWS Management Console and third-party software-as-a-service (SaaS) applications. Trust must be enhanced to prevent two external accounts from using the same credentials. The solution must require the least possible operational effort.
Which solution will meet these requirements?
An AWS account includes two S3 buckets: bucketl and bucket2. The bucket2 does not have a policy defined, but bucketl has the following bucket policy:
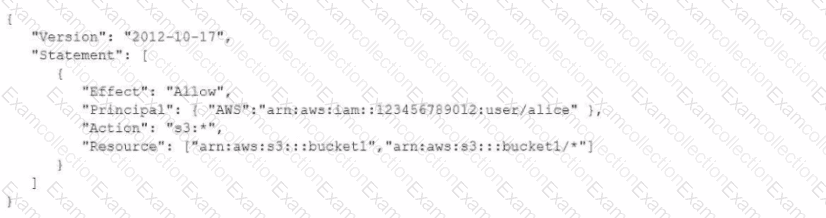
In addition, the same account has an 1AM User named "alice", with the following 1AM policy.

Which buckets can user "alice" access?



