Splunk SPLK-3003 - Splunk Core Certified Consultant
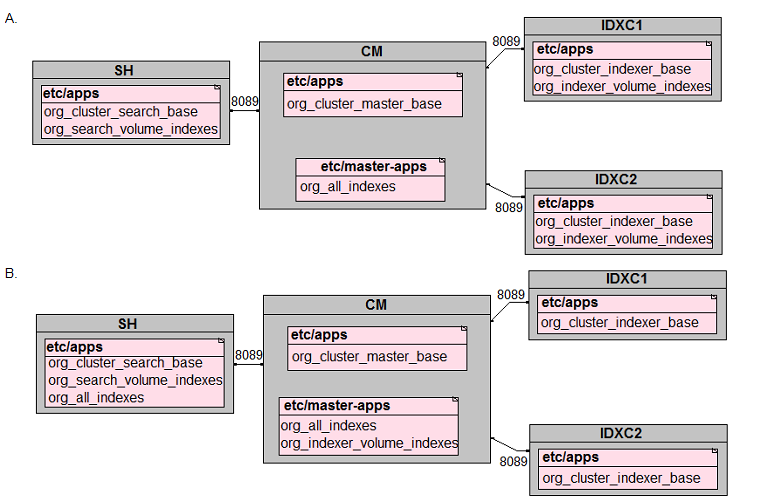
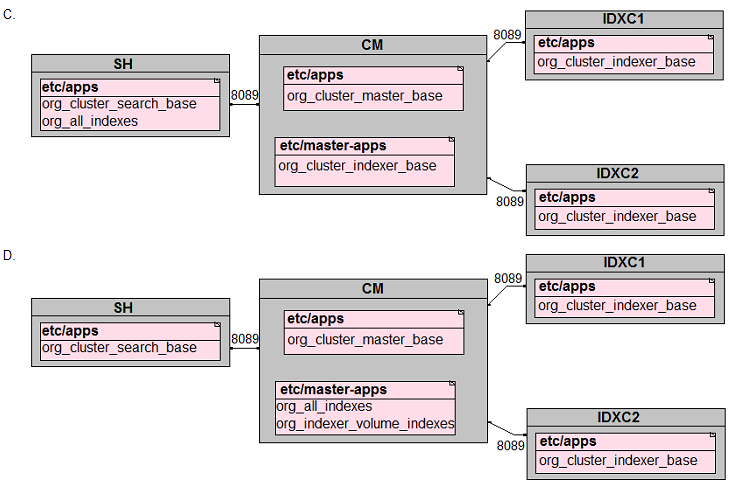
In preparation for the deployment of a new environment for a customer, which of the following mappings are correct per PS best practices?
Consider the scenario where the /var/log directory contains the files secure, messages, cron, audit. A customer has created the following inputs.conf stanzas in the same Splunk app in order to attempt to monitor the files secure and messages:

Which file(s) will actually be actively monitored?
Data can be onboarded using apps, Splunk Web, or the CLI.
Which is the PS preferred method?
When using SAML, where does user authentication occur?
What does Splunk do when it indexes events?
Which of the following processor occur in the indexing pipeline?
In which of the following scenarios is a subsearch the most appropriate?
Which of the following statements applies to indexer discovery?
A customer would like to remove the output_file capability from users with the default user role to stop them from filling up the disk on the search head with lookup files. What is the best way to remove this capability from users?
Which of the following server roles should be configured for a host which indexes its internal logs locally?



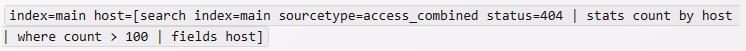 This search will return the events from the main index that have a host value that matches the subsearch. The subsearch will find the hosts that have more than 100 events with status 404 in the access_combined sourcetype, and pass them to the outer search as a list of values. This way, we can dynamically filter the hosts based on another search criterion.
This search will return the events from the main index that have a host value that matches the subsearch. The subsearch will find the hosts that have more than 100 events with status 404 in the access_combined sourcetype, and pass them to the outer search as a list of values. This way, we can dynamically filter the hosts based on another search criterion.