CompTIA SY0-601 - CompTIA Security+ Exam 2023
A software company adopted the following processes before releasing software to production
• Peer review
• Static code scanning
• Signing
A considerable number of vulnerabilities are still being detected when code is executed on production Which of the following security tools can improve vulnerability detection on this environment?
An organization is concerned about intellectual property theft by employees who leave the organization Which of the following should the organization most likely implement?
A security administrator received an alert for a user account with the following log activity:
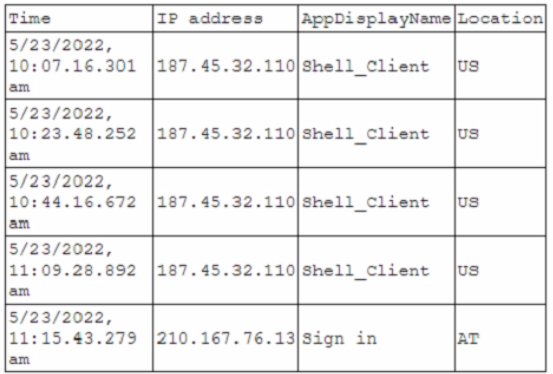
Which of the following best describes the trigger for the alert the administrator received?
The concept of connecting a user account across the systems of multiple enterprises is best known as:
The Chief Executive Officer (CEO) of an organization would like staff members to have the flexibility to work from home anytime during business hours, including during a pandemic or crisis. However, the CEO is concerned that
some staff members may take advantage of the flexibility and work from high-risk countries while on holiday or outsource work to a third-party organization in another country. The Chief Information Officer believes the company
can implement some basic controls to mitigate the majority of the risk. Which of the following would be best to mitigate the CEO's concerns? (Select two).
A security analyst wants to fingerprint a web server. Which of the following tools will the security analyst MOST likely use to accomplish this task?
Which of the following requirements apply to a CYOD policy? (Select two).
A systems administrator needs to set up a secure, cloud-based file transfer environment between two data centers. Which of the following architecture models would meet this requirement?
A security analyst has been tasked with ensuring all programs that are deployed into the enterprise have been assessed in a runtime environment Any critical issues found in the program must be sent back to the developer for verification and remediation. Which of the following lost describes the type of assessment taking place?
A Chief Information Security Officer has defined resiliency requirements for a new data center architecture. The requirements are as follows:
• Critical fileshares will remain accessible during and after a natural disaster.
• Five percent of hard disks can fail at any given time without impacting the data.
• Systems will be forced to shut down gracefully when battery levels are below 20%.
Which of the following are required to BEST meet these objectives? (Select THREE).
A cybersecurity analyst reviews the log files from a web server end sees a series of files that indicate a directory traversal attack has occurred Which of the following is the analyst most likely seeing?
A company's marketing department collects, modifies, and stores sensitive customer data. The infrastructure team is responsible for Securing the data while in transit and at rest. Which of the following data roles describes the customer?
A security team created a document that details the order in which critical systems should be brought back online after a major outage. Which of the following documents did the team create?
Which of the following best describes the action captured in this log file?
A company would like to enhance the authentication technologies being used by remote employees Which of the following should the company most likely choose?
Which of the following would be the best ways to ensure only authorized personnel can access a secure facility? (Select two).
An employee fell for a phishing scam, which allowed an attacker to gain access to a company PC. The attacker scraped the PC's memory to find other credentials. Without cracking these credentials, the attacker used them to move laterally through the corporate network. Which of the following describes this type of attack?
Which of the following security concepts is the best reason for permissions on a human resources fileshare to follow the principle of least privilege?
An organization wants to minimize the recovery time from backups in case of a disaster. Backups must be retained for one month, while minimizing the storage space used for backups. Which of the following is the best approach for a backup strategy?
Which of the following best practices gives administrators a set period to perform changes to an operational system to ensure availability and minimize business impacts?