CompTIA SY0-601 - CompTIA Security+ Exam 2023
A company recently decided to allow employees to work remotely. The company wants to protect its data without using a VPN. Which of the following technologies should the company implement?
A newly implemented wireless network is designed so that visitors can connect to the wireless network for business activities. The legal department is concerned that visitors might connect to the network and perform illicit activities. Which of the following should the security team implement to address this concern?
A security administrator is reviewing reports about suspicious network activity occurring on a subnet Users on the network report that connectivity to various websites is intermittent. The administrator logs in to a workstation and reviews the following command output:
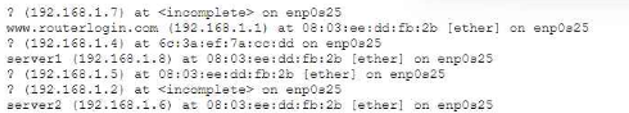
Which of the following best describes what is occurring on the network?
After a security incident, a systems administrator asks the company to buy a NAC platform. Which of the following attack surfaces is the systems administrator trying to protect?
In order to save on expenses Company A and Company B agree to host each other's compute and storage disaster recovery sites at their primary data centers The two data centers are about a mile apart, and they each have their own power source When necessary, one company will escort the other company to its data center. Which of the following is the greatest risk with this arrangement?
An employee recently resigned from a company. The employee was responsible for managing and supporting weekly batch jobs over the past five years. A few weeks after the employee resigned, one of the batch jobs failed and caused a major disruption. Which of the following would work best to prevent this type of incident from reoccurring?
One of a company's vendors sent an analyst a security bulletin that recommends a BIOS update. Which of the following vulnerability types is being addressed by the patch?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 802.1X for access control. To be allowed on the network, a device must have a known hardware address, and a valid username and password must be entered in a captive portal. The following is the audit report:
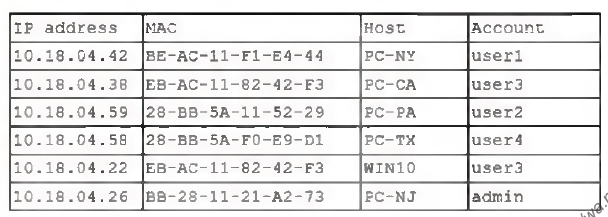
Which of the following is the most likely way a rogue device was allowed to connect?
Which of the following attributes would be the most appropriate to apply when implementing MFA?
Which of the following would be the best way to block unknown programs from executing?
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device. Which of the following best describes the user’s activity?
Which of the following best describes why the SMS OTP authentication method is more risky to implement than the TOTP method?
A third-party vendor is moving a particular application to the end-of-life stage at the end of the current year. Which of the following is the most critical risk if the company chooses to continue running the application?
Which of the following describes a social engineering technique that may include scam emails addressed directly to the Chief Financial Officer?
While performing digital forensics, which of the following is considered the most volatile and should have the contents collected first?
Which of the following involves an attempt to take advantage of database misconfigurations?
The Chief Information Security Officer of an organization needs to ensure recovery from ransomware would likely occur within the organization's agreed-upon RPOs and RTOs. Which of the following backup scenarios would best ensure recovery?
Which of the following should a security operations center use to improve its incident response procedure?
A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
An analyst observed an unexpected high number of DE authentication on requests being sent from an unidentified device on the network. Which of the following attacks was most likely executed in this scenario?



