CompTIA SY0-601 - CompTIA Security+ Exam 2023
Which of the following can be used to identify potential attacker activities without affecting production servers?
Which of the following describes the understanding between a company and a client about what will be provided and the accepted time needed to provide the company with the resumes?
Which of the following should a systems administrator use to ensure an easy deployment of resources within the cloud provider?
A new company wants to avoid channel interference when building a WLAN. The company needs to know the radio frequency behavior, identify dead zones, and determine the best place for access points. Which of the following should be done first?
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
A company is required to perform a risk assessment on an annual basis. Which of the following types of risk assessments does this requirement describe?
Which of the following would most likely mitigate the impact of an extended power outage on a company’s environment?
An employee in the accounting department receives an email containing a demand for payment for services performed by a vendor. However, the vendor is not in the vendor management database. Which of the following is this scenario an example of?
After a web server was migrated to a cloud environment, user access to that server was Wocked Ever though an on-premises firewall configuration has been modified to reflect the cloud infrastructure, users are still experiencing access issues. Which of the following most likely needs to be configured?
Which of the following is most likely to include a SCADA system?
Which of the following is the first step to take when creating an anomaly detection process?
An organization received threat intelligence describing an increase in credential harvesting across the industry A security analyst is reviewing the following authentication logs to look for potential Indicators of compromise.
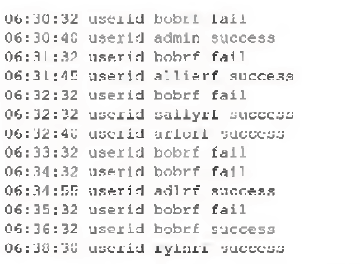
Which of the following configurations can help prevent this hype of attack from occurring?
A company wants to move one of its environments to the cloud. The biggest requirement is to have as much control as possible regarding the environment. Which of the following would most likely satisfy this requirement?
The cybersecurity investigation team is requesting a budget increase m order to purchase and implement a commercial tool for collecting information. The information might include disk images and volatile memory from computers used by remote employees Which of the following digital forensic categories does the company want to implement?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
When a newly developed application was tested a specific internal resource was unable to be accessed Which of the following should be done to ensure the application works correctly?
Which of the following best describes the tolerances a security architect follows when designing a control environment?
A company would like to implement a secure process for managing headless servers remotely Which of the following should the company most likely implement?
An organization wants to reduce the likelihood that a data breach could result in reputational. financial, or regulatory consequences. The organization needs an enterprise-wide solution that does not require new technology or specialized roles Which of the following describes the best way to achieve these goals?
An organization developed a virtual thin client running in kiosk mode mat is used to access various software depending on the users' roles During a security evaluation, the test team identified the ability to exit kiosk mode and access system-level resources which led to privilege escalation Which of the following mitigations addresses this finding?



