CompTIA SY0-601 - CompTIA Security+ Exam 2023
Which of the following enables the use of an input field to run commands that can view or manipulate data?
An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a "page not found" error message. Which of the following types of social engineering attacks occurred?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
A bank was recently provided a new version of an executable that was used to launch its core banking platform. During the upgrade process, a remote code execution exploit was publicly released that targeted the old version. Which of the following would best prevent a security incident?
A newly appointed board member with cybersecurity knowledge wants the board of directors to receive a quarterly report detailing the number of incidents that impacted the organization. The systems administrator is creating a way to present the data to the board of directors. Which of the following should the systems administrator use?
A company wants to ensure that ail devices are secured property through the MDM solution so that, if remote wipe fails, access to the data will still be inaccessible offline. Which of the following would need to be configured?
A systems administrator wants to implement a backup solution. The solution needs to allow recovery of the entire system, including the operating system, in case of a disaster. Which of the following backup types should the administrator consider?
Which of the following threat actors is the most likely to use large financial resources to attack critical systems located in other countries?
Which of the following provides guidelines for the management and reduction of information security risk?
Which of the following are cases in which an engineer should recommend the decommissioning of a network device? (Select two).
Which of the following vulnerabilities is associated with installing software outside of a manufacturer's approved software repository?
A security analyst is responding to a malware incident at a company. The malware connects to a command-and-control server on the internet in order to function. Which of the following should the security analyst implement first?
A security analyst is investigating a SIEM event concerning invalid log-ins The system logs that match the time frame of the event show the following:
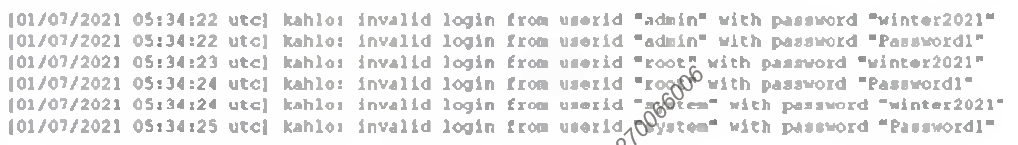
Which of the following best describes this type of attack?
A company is utilizing an offshore team to help support the finance department. The company wants to keep the data secure by keeping it on a company device but does not want to provide equipment to the offshore team. Which of the following should the company implement to meet this requirement?
An employee receives a text message that appears to have been sent by the payroll department and is asking for credential verification. Which of the following social engineering techniques are being attempted? (Select two).
A security analyst is reviewing alerts in the SIEM related to potential malicious network traffic coming from an employee's corporate laptop. The security analyst has determined that additional data about the executable running on the machine is necessary to continue the investigation. Which of the following logs should the analyst use as a data source?
After segmenting the network, the network manager wants to control the traffic between the segments. Which of the following should the manager use to control the network traffic?
A company was compromised, and a security analyst discovered the attacker was able to get access to a service account. The following logs were discovered during the investigation:

Which of the following MOST likely would have prevented the attacker from learning the service account name?
A security analyst wants to verify that a client-server (non-web) application is sending encrypted traffic. Which of the following should the analyst use?
A cybersecurity administrator needs to implement a Layer 7 security control on a network and block potential attacks. Which of the following can block an attack at Layer 7? (Select TWO).



