CompTIA SY0-601 - CompTIA Security+ Exam 2023
An organization is building a new headquarters and has placed fake cameras around the building in an attempt to discourage potential intruders. Which of the following kinds of controls describes this security method?
A security analyst discovers that one of the web APIs is being abused by an unknown third party. Logs indicate that the third party is attempting to manipulate the parameters being passed to the API endpoint. Which of the following solutions would best help to protect against the attack?
A company needs to centralize its logs to create a baseline and have visibility on its security events Which of the following technologies will accomplish this objective?
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would best support the policy?
An organization has expanded its operations by opening a remote office. The new office is fully furnished with office resources to support up to 50 employees working on any given day. Which of the following VPN solutions would best support the new office?
Which of the following are common VoIP-associated vulnerabilities? (Select two).
Which of the following roles is responsible for defining the protection type and Classification type for a given set of files?
Which of the following cloud models provides clients with servers, storage, and networks but nothing else?
Which of the following tools can assist with detecting an employee who has accidentally emailed a file containing a customer's Pll?
A company wants to deploy decoy systems alongside production systems in order to entice threat actors and to learn more about attackers. Which of the follow r 3 best describes these systems?
Two organizations are discussing a possible merger Both Organizations Chief Fi-nancial Officers would like to safely share payroll data with each Other to de-termine if the pay scales for different roles are similar at both organizations Which Of the following techniques would be best to protect employee data while allowing the companies to successfully share this information?
A government organization is developing an advanced Al defense system. Develop-ers are using information collected from third-party providers Analysts are no-ticing inconsistencies in the expected powers Of then learning and attribute the Outcome to a recent attack on one of the suppliers. Which of the following IS the most likely reason for the inaccuracy of the system?
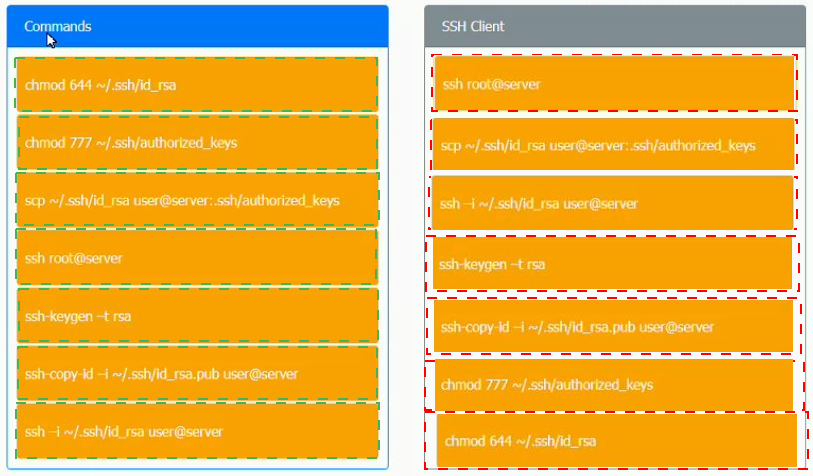
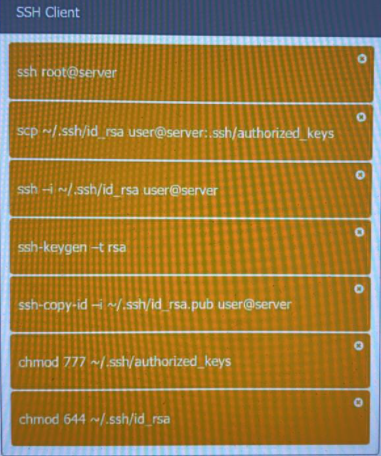
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which of the following would help ensure a security analyst is able to accurately measure the overall risk to an organization when a new vulnerability is disclosed?
Which of the following is a primary security concern for a company setting up a BYOD program?
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly Which of the following technologies should the IT manager use when implementing MFA?
A security analyst is looking for a solution to help communicate to the leadership team the seventy levels of the organization's vulnerabilities. Which of the following would best meet this need?
A security analyst is hardening a network infrastructure The analyst is given the following requirements
• Preserve the use of public IP addresses assigned to equipment on the core router
• Enable "in transport" encryption protection to the web server with the strongest ciphers.
Which of the following should the analyst implement to meet these requirements? (Select two).
During an assessment, a systems administrator found several hosts running FTP and decided to immediately block FTP communications at the firewall. Which of the following describes the
greatest risk associated with using FTP?
A company's help desk has received calls about the wireless network being down and users being unable to connect to it The network administrator says all access points are up and running One of the help desk technicians notices the affected users are working in a building near the parking lot. Which of the following is the most likely reason for the outage?



 A screenshot of a computer
Description automatically generated with medium confidence
A screenshot of a computer
Description automatically generated with medium confidence