CompTIA SY0-601 - CompTIA Security+ Exam 2023
Which of the following would be the best resource for a software developer who is looking to improve secure coding practices for web applications?
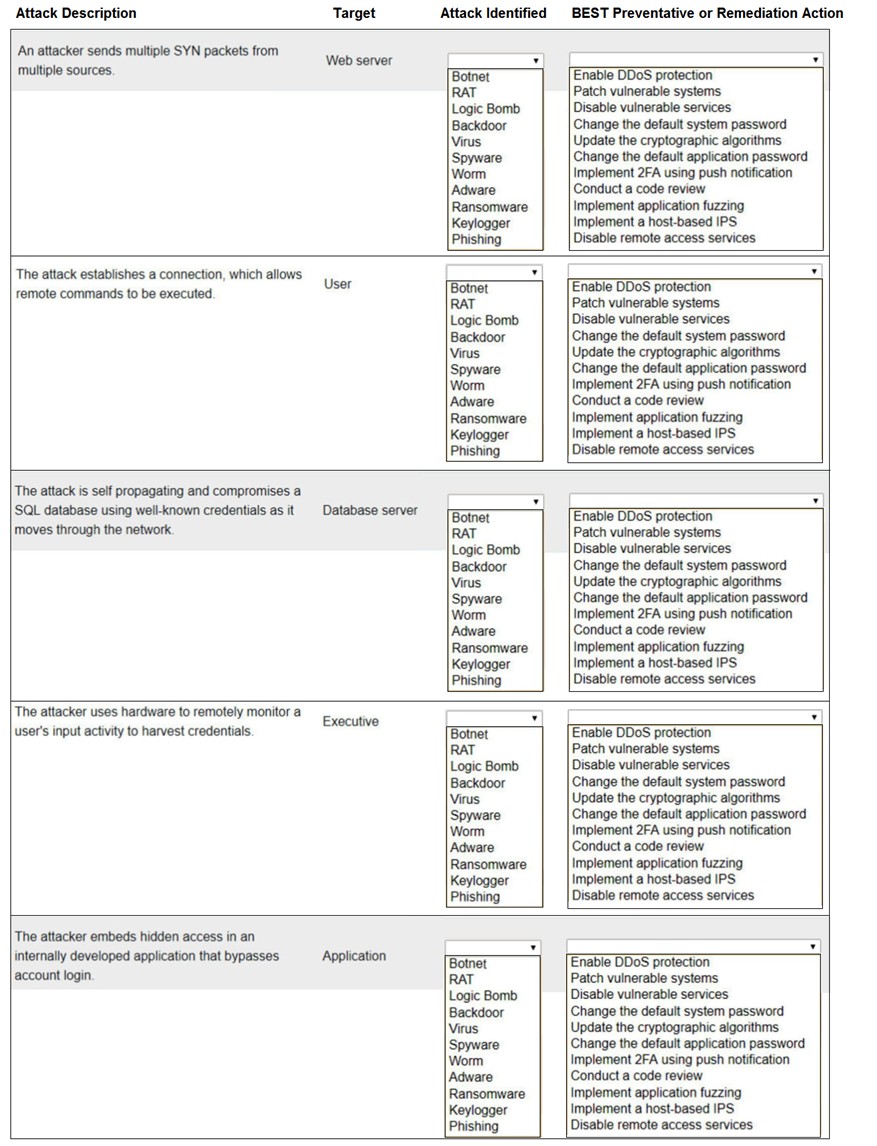
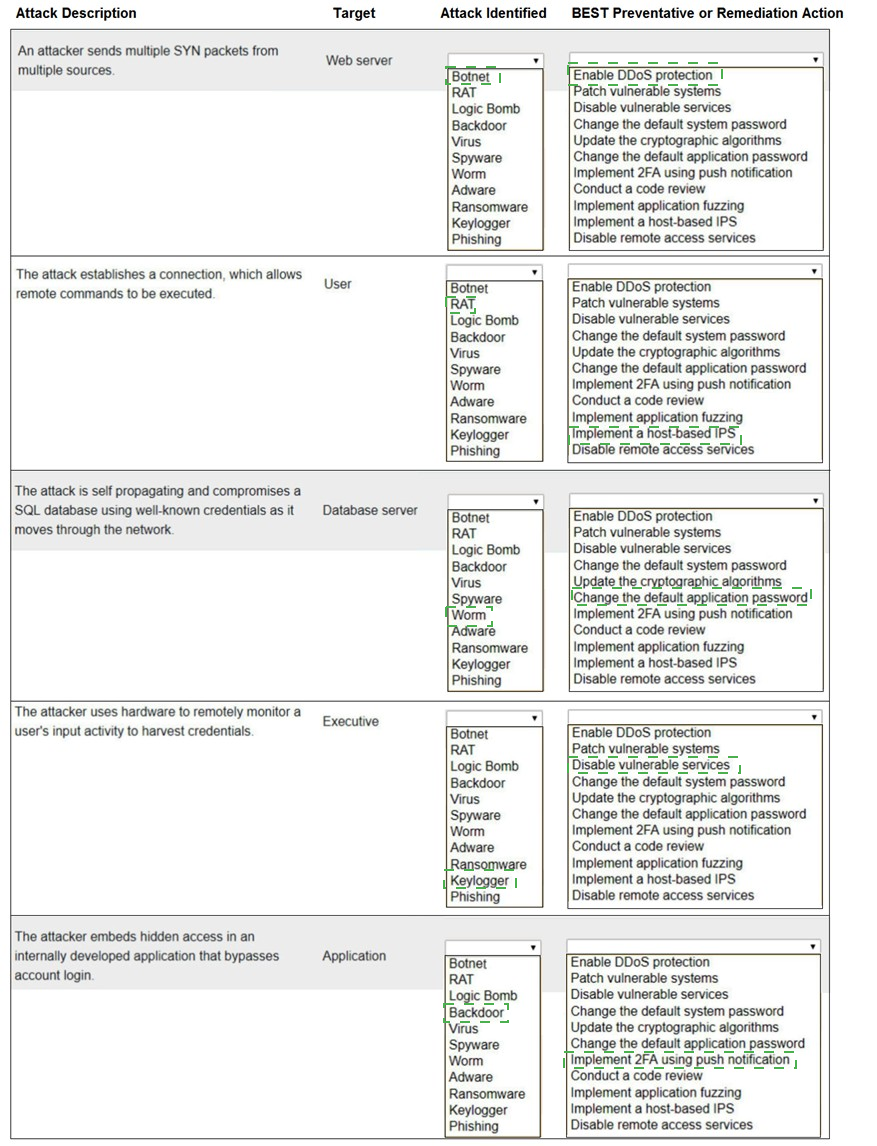
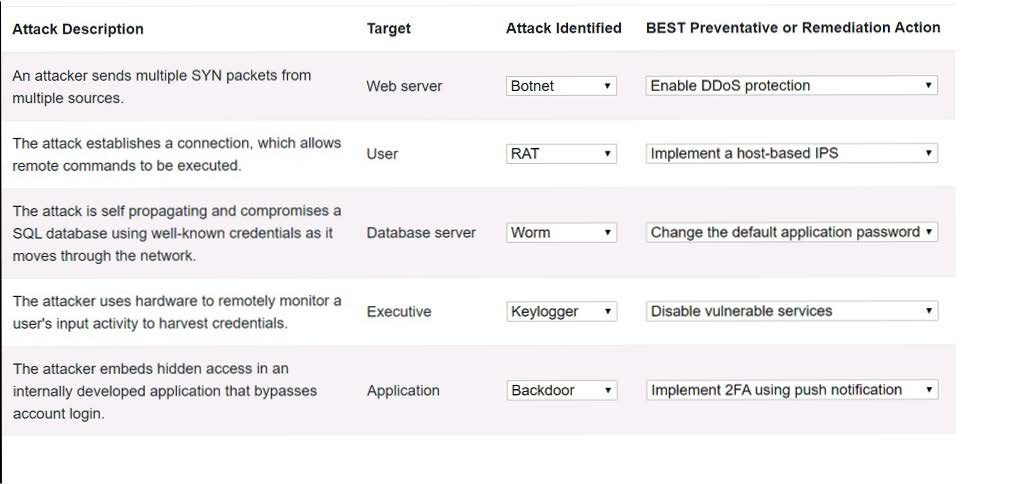
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
A network manager is concerned that business may be negatively impacted if the firewall in its data center goes offline. The manager would like to implement a high availability pair to:
Which of the following terms should be included in a contract to help a company monitor the ongo-ing security maturity Of a new vendor?
Which of the following best reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
A user downloaded an extension for a browser, and the user's device later became infected. The analyst who Is Investigating the Incident saw various logs where the attacker was hiding activity by deleting data. The following was observed running:
New-Partition -DiskNumber 2 -UseMaximumSize -AssignDriveLetter C| Format-Volume -Driveletter C - FileSystemLabel "New"-FileSystem NTFS - Full -Force -Confirm:$false
Which of the following is the malware using to execute the attack?
A security architect is designing a remote access solution for a business partner. The business partner needs to access one Linux server at the company. The business partner wants to avid managing a password for authentication and additional software installation. Which of the following should the architect recommend?
Which of the following supplies non-repudiation during a forensics investigation?
A network penetration tester has successfully gained access to a target machine. Which of the following should the penetration tester do next?
A web server has been compromised due to a ransomware attack. Further Investigation reveals the ransomware has been in the server for the past 72 hours. The systems administrator needs to get the services back up as soon as possible. Which of the following should the administrator use to restore services to a secure state?
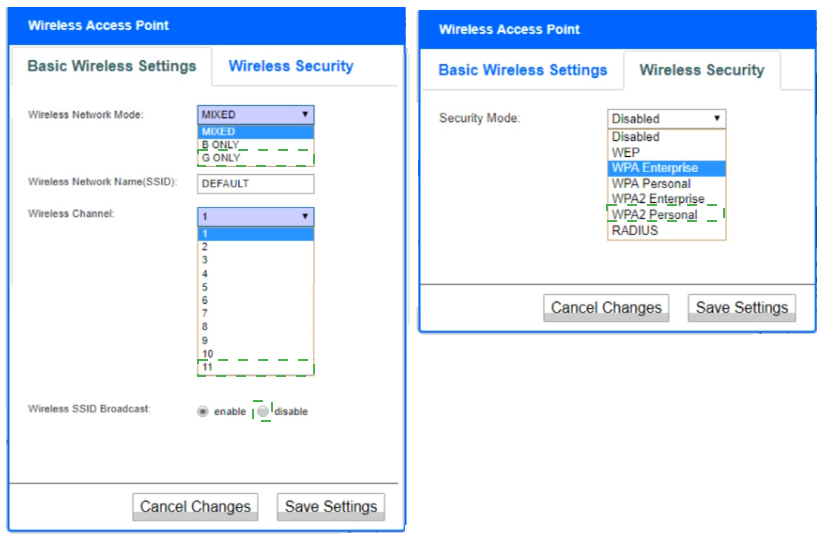
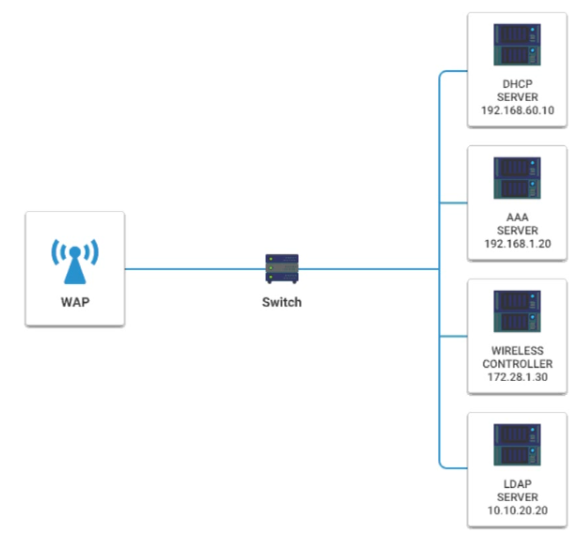
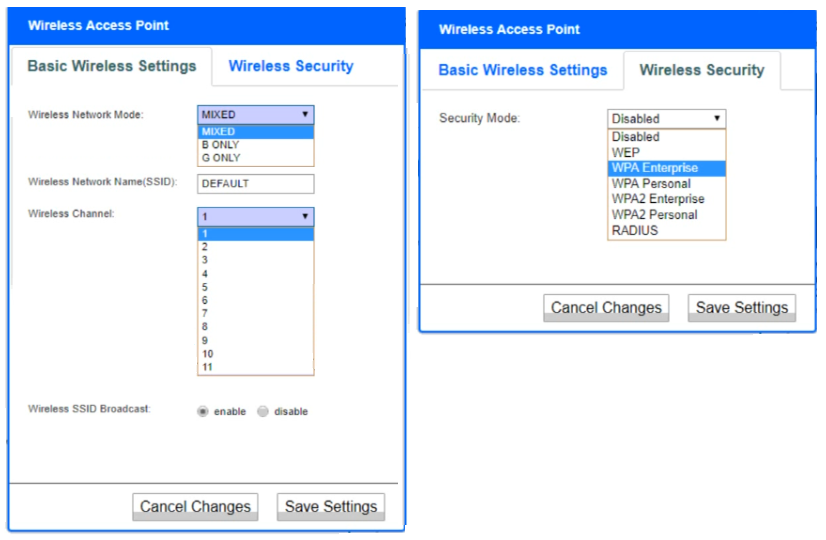
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
WAP
DHCP Server
AAA Server
Wireless Controller
LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A company's help desk has received calls about the wireless network being down and users being unable to connect to it. The network administrator says all access pcints are up and running. One of the help desk technicians notices the affected users are working in a near the parking Jot Which Of the following IS the most likely reason for the outage?
A security analyst is investigating what appears to be unauthorized access to a corporate web application. The security analyst reviews the web server logs and finds the following entries:
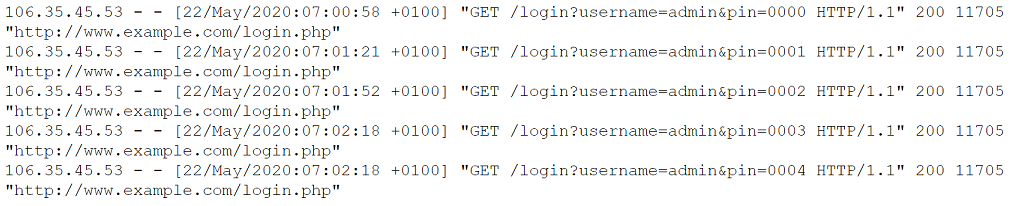
Which of the following password attacks is taking place?
Security analysts notice a server login from a user who has been on vacation for two weeks, The an-alysts confirm that the user did not log in to the system while on vacation After reviewing packet capture the analysts notice the following:
Which of the following occurred?
Which Of the following will provide the best physical security countermeasures to Stop intruders? (Select two).
An organization is repairing the damage after an incident. Which of the following controls is being implemented?
Which of the following threat actors is most likely to be motivated by ideology?
A company recently experienced a significant data loss when proprietary information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the best mitigation strategy to prevent this from happening in the future?
A security analyst is currently addressing an active cyber incident. The analyst has been able to identify affected devices that are running a malicious application with a unique hash. Which of the following is the next step according to the incident response process?



 A screenshot of a computer program
Description automatically generated with low confidence
A screenshot of a computer program
Description automatically generated with low confidence