CompTIA SY0-701 - CompTIA Security+ Exam 2025
After creating a contract for IT contractors, the human resources department changed several clauses. The contract has gone through three revisions. Which of the following processes should the human resources department follow to track revisions?
Which of the following attacks primarily targets insecure networks?
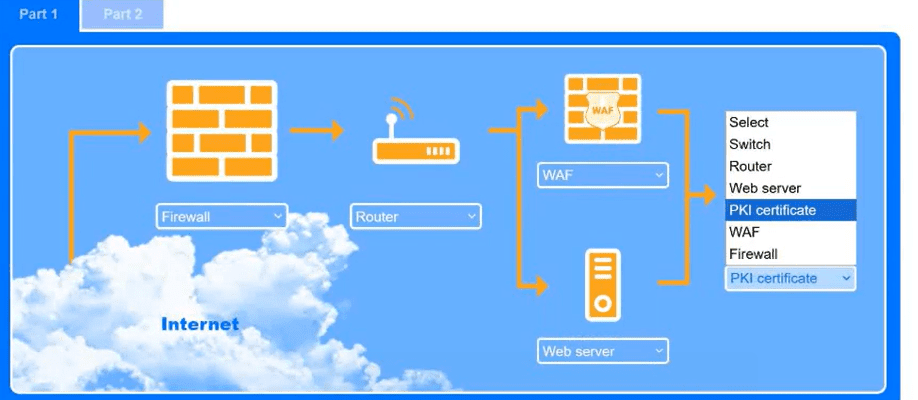
A recent black-box penetration test of http://example.com discovered that external
website vulnerabilities exist, such as directory traversals, cross-site scripting, cross-site forgery, and insecure protocols.
You are tasked with reducing the attack space and enabling secure protocols.
INSTRUCTIONS
Part 1
Use the drop-down menus to select the appropriate technologies for each location to implement a secure and resilient web architecture. Not all technologies will be used, and technologies may be used multiple times.
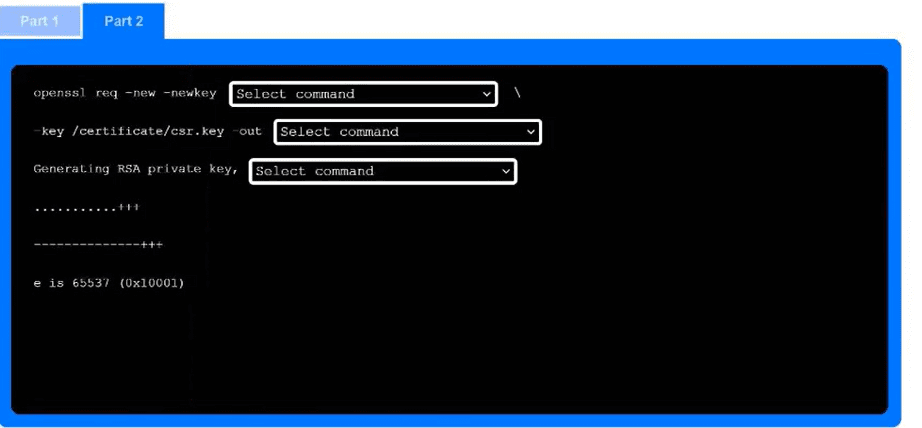
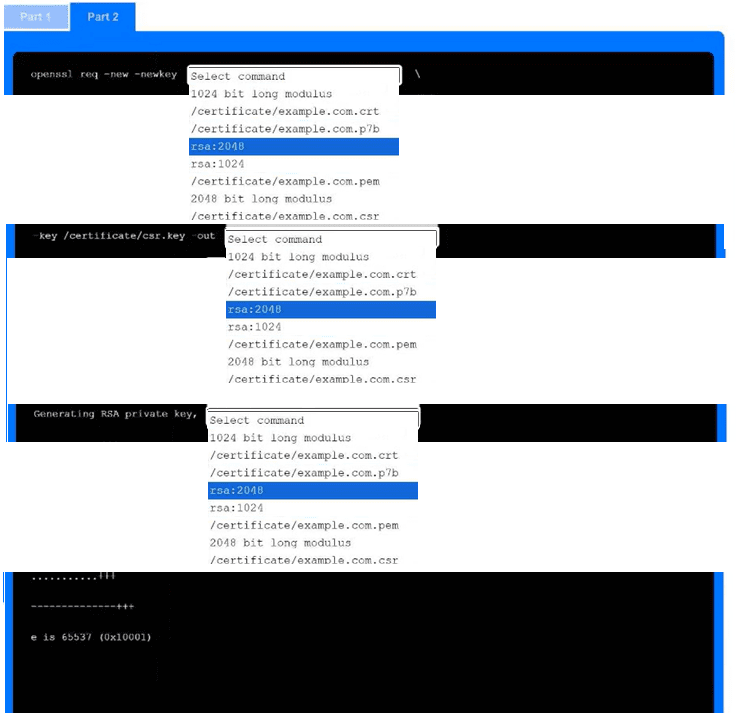
Part 2
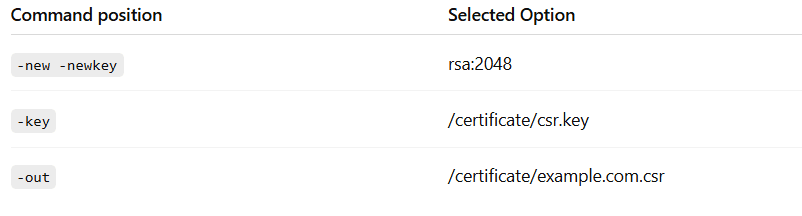
Use the drop-down menus to select the appropriate command snippets from the drop-down menus. Each command section must be filled.
Which of the following should a security team do first before a new web server goes live?
At the start of a penetration test, the tester checks OSINT resources for information about the client environment. Which of the following types of reconnaissance is the tester performing?
Which of the following control types describes an alert from a SIEM tool?
Employees sign an agreement that restricts specific activities when leaving the company. Violating the agreement can result in legal consequences. Which of the following agreements does this best describe?
An engineer moved to another team and is unable to access the new team's shared folders while still being able to access the shared folders from the former team. After opening a ticket, the engineer discovers that the account was never moved to the new group. Which of the following access controls is most likely causing the lack of access? 1 Â
A healthcare organization wants to provide a web application that allows individuals to digitally report health emergencies.
Which of the following is the most important consideration during development?
A company prevented direct access from the database administrators’ workstations to the network segment that contains database servers. Which of the following should a database administrator use to access the database servers?
A company is planning a disaster recovery site and needs to ensure that a single natural disaster would not result in the complete loss of regulated backup data. Which of the following should the company consider?
Which of the following actors attacking an organization is the most likely to be motivated by personal beliefs?
A security officer observes that a software development team is not complying with its corporate security policy on encrypting confidential data. Which of the following categories refers to this type of non-compliance?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
Which of the following vulnerabilities is exploited when an attacker overwrites a register with a malicious address?