CompTIA SY0-701 - CompTIA Security+ Exam 2025
A university uses two different cloud solutions for storing student data. Which of the following does this scenario represent?
An employee fell for a phishing scam, which allowed an attacker to gain access to a company PC. The attacker scraped the PC’s memory to find other credentials. Without cracking these credentials, the attacker used them to move laterally through the corporate network. Which of the following describes this type of attack?
Which of the following best describe the benefits of a microservices architecture when compared to a monolithic architecture? (Select two).
Which of the following steps in the risk management process involves establishing the scope and potential risks involved with a project?
Which of the following documents details how to accomplish a technical security task?
While investigating a possible incident, a security analyst discovers the following log entries:
67.118.34.157 ----- [28/Jul/2022:10:26:59 -0300] "GET /query.php?q-wireless%20headphones / HTTP/1.0" 200 12737
132.18.222.103 ----[28/Jul/2022:10:27:10 -0300] "GET /query.php?q=123 INSERT INTO users VALUES('temp', 'pass123')# / HTTP/1.0" 200 935
12.45.101.121 ----- [28/Jul/2022:10:27:22 -0300] "GET /query.php?q=mp3%20players I HTTP/1.0" 200 14650
Which of the following should the analyst do first?
A systems administrator wants to prevent users from being able to access data based on their responsibilities. The administrator also wants to apply the required access structure via a simplified format. Which of the following should the administrator apply to the site recovery resource group?
A company is in the process of migrating to cloud-based services. The company's IT department has limited resources for migration and ongoing support. Which of the following best meets the company's needs?
A company wants to ensure secure remote access to its internal network. The company has only one public IP and would like to avoid making any changes to the current network setup. Which of the following solutions would best accomplish this goal?
An engineer needs to ensure that a script has not been modified before it is launched. Which of the following best provides this functionality?
Which of the following is an algorithm performed to verify that data has not been modified?
After failing an audit twice, an organization has been ordered by a government regulatory agency to pay fines. Which of the following caused this action?
Which of the following is a type of vulnerability that may result from outdated algorithms or keys?
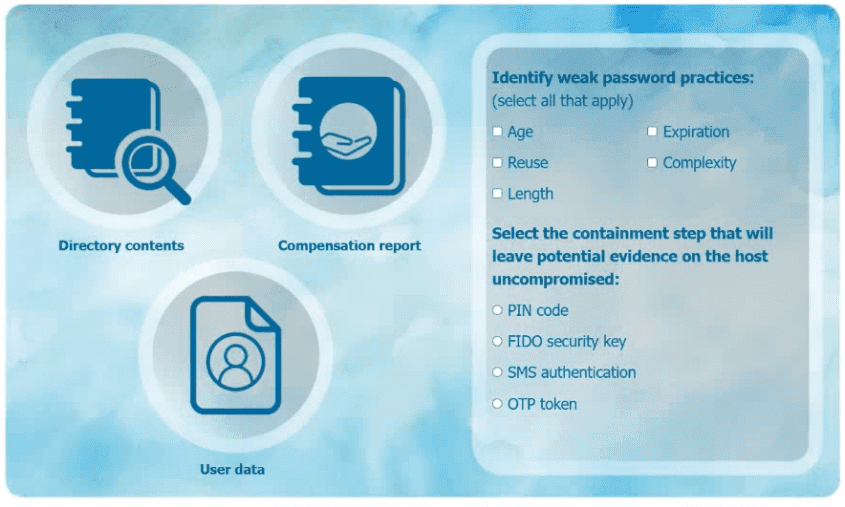
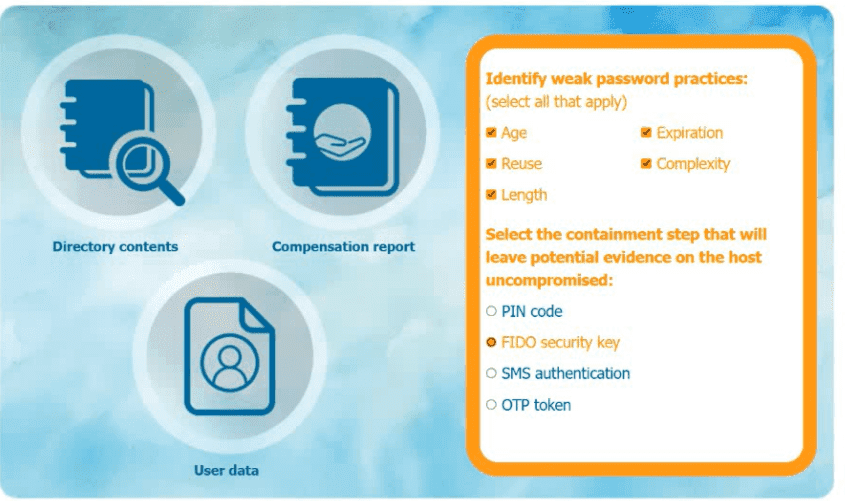
An organization has learned that its data is being exchanged on the dark web. The CIO
has requested that you investigate and implement the most secure solution to protect employee accounts.
INSTRUCTIONS
Review the data to identify weak security practices and provide the most appropriate
security solution to meet the CIO's requirements.
A security report shows that during a two-week test period. 80% of employees unwittingly disclosed their SSO credentials when accessing an external website. The organization purposelycreated the website to simulate a cost-free password complexity test. Which of the following would best help reduce the number of visits to similar websites in the future?



 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.