WGU Secure-Software-Design - WGU Secure Software Design (D487, KEO1) Exam
What is an advantage of using the Agile development methodology?
Which secure software design principle assumes attackers have the source code and specifications of the product?
The security team is identifying technical resources that will be needed to perform the final product security review.
Which step of the final product security review process are they in?
What is the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or distribution to provide confidentiality, integrity, and availability?
During fuzz testing of the new product, an exception was thrown on the order entry view, which caused a full stack dump to be displayed in the browser window that included function names from the source code.
How should existing security controls be adjusted to prevent this in the future?
Credit card numbers are encrypted when stored in the database but are automatically decrypted when data is fetched. The testing tool intercepted the GET response, and testers were able to view credit card numbers as clear text.
How should the organization remediate this vulnerability?
Which threat modeling approach concentrates on things the organization wants to protect?
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
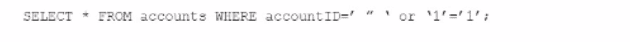
Which technique should be used to detect this vulnerability without running the source codes?
The software security team is performing security testing for a new software product that is close to production release. They are concentrating on integrations between the new product and database servers, web servers, and web services.
Which security testing technique is being used?
Which mitigation technique can be used to light against a threat where a user may gain access to administrator level functionality?



