HashiCorp Vault-Associate - HashiCorp Certified: Vault Associate (002)
What is the Vault CLI command to query information about the token the client is currently using?
Which of these are a benefit of using the Vault Agent?
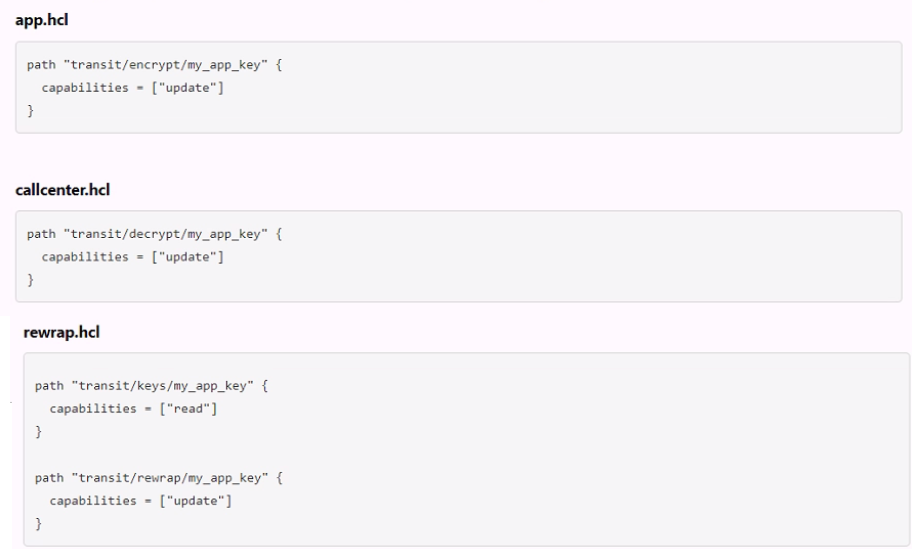
The following three policies exist in Vault. What do these policies allow an organization to do?
Which of these is not a benefit of dynamic secrets?
To make an authenticated request via the Vault HTTP API, which header would you use?
An authentication method should be selected for a use case based on:
What are orphan tokens?
Running the second command in the GUI CLI will succeed.
A developer mistakenly committed code that contained AWS S3 credentials into a public repository. You have been tasked with revoking the AWS S3 credential that was in the code. This credential was created using Vault's AWS secrets engine and the developer received the following output when requesting a credential from Vault.
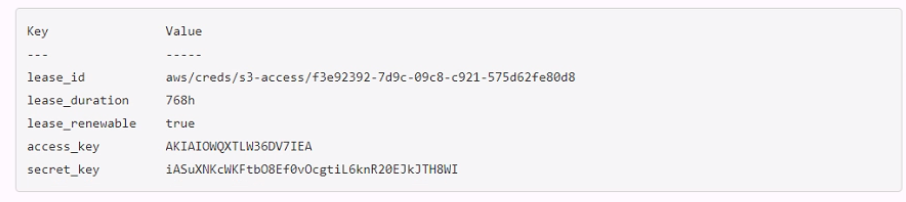
Which Vault command will revoke the lease and remove the credential from AWS?
Which of the following are replication methods available in Vault Enterprise? Choose two correct answers.



